User real information security certification system and method
A technology of information security and user information, which is applied in the field of user real information security authentication system, can solve the problems that it is difficult to avoid punching cards and shifts, high cost, and poor scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
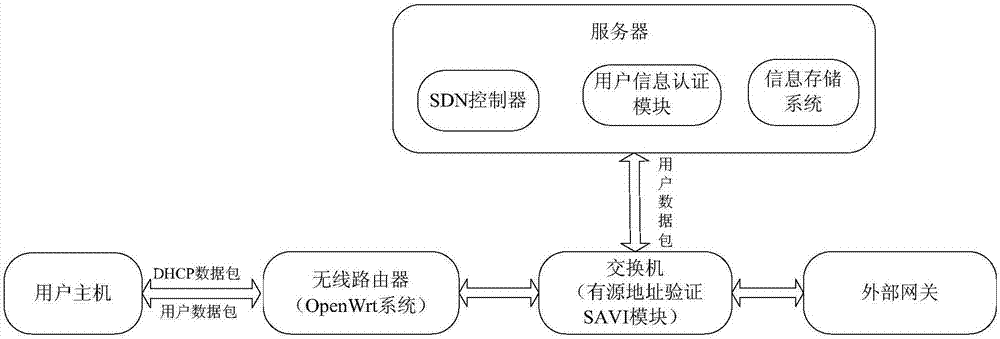
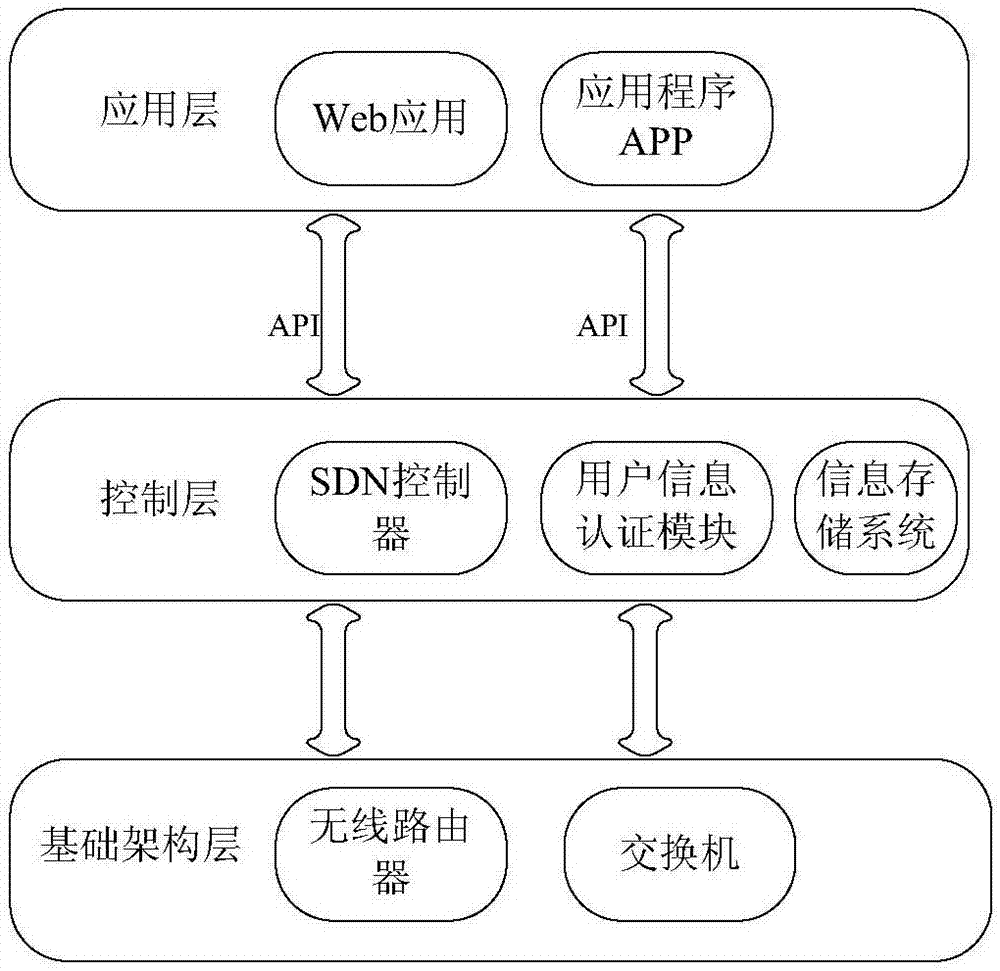
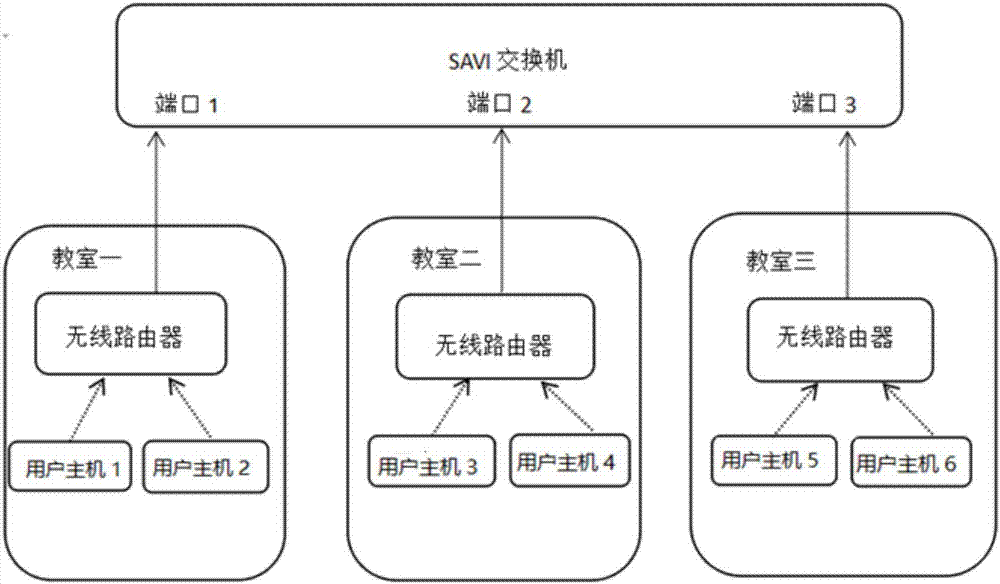
[0055] The invention discloses a user real information security authentication system, such as figure 1 , including user hosts, wireless routers, switches and servers, such as figure 2 As shown, it is mainly composed of an infrastructure layer, a control layer and an application layer; it is characterized in that the infrastructure layer includes a wireless router and a switch, and is used for data forwarding; the control layer includes an SDN controller in a server, a user An information authentication module and an information storage system are used to process data; the application layer includes web applications and applications running on user hosts, which are used to display data; wherein:
[0056] The user host is connected to the wireless router through the wireless network, and is used to send a DHCP packet to the wireless router to request the DHCP server in the wireless router to assign a legal IP address; it is used to receive the RA notification forwarded by the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com