Biometric key extraction method based on fingerprint bit string and error correction coding
A technology of biological key and extraction method, applied in the field of biological key extraction, can solve the problem of fingerprint privacy leakage, and achieve the effect of resisting brute force attack, reducing computing cost, and protecting user fingerprint privacy information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
[0051] A biological key extraction method based on fingerprint bit string and error correction coding, the specific method is: based on fingerprint bit string and error correction coding algorithm, an irreversible and changeable change function or parameter is designed to transform the original biological characteristics, and the original The template is transformed into a transformation template to generate a biometric revocable template; and through fuzzy extraction, the registration template and verification template brake registration problem is solved under the transformation domain, so that the biometric authentication has a low rejection rate and ensures the usability of the authentication scheme.
[0052] This transformation is one-way, even if the attacker obtains the transformation template and transformation function or parameters, the original template cannot be restored. If the existing transformation template is suspected to have a problem, as long as the new tran...
specific Embodiment 2
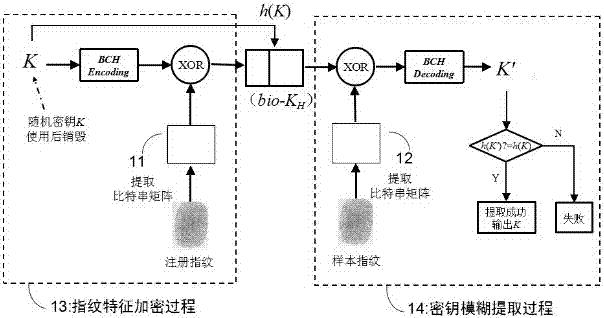
[0054] On the basis of specific embodiment 1, such as figure 1 shown, specifically including,
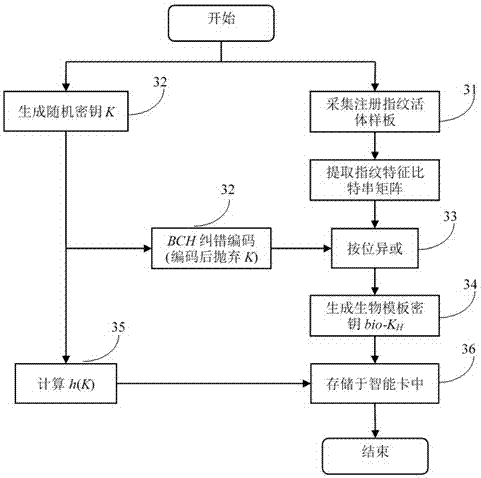
[0055] Fingerprint feature registration process: collect and register live fingerprint samples, extract fingerprint bit string matrix H d ;Any one of the fingerprint bit strings β i The length of each is d; a randomly generated binary key K is encoded as a binary sequence with the same length d as the fingerprint bit string; and this binary sequence is combined with the bit string matrix H d Diff OR, generate biological template auxiliary data bio-K H ;
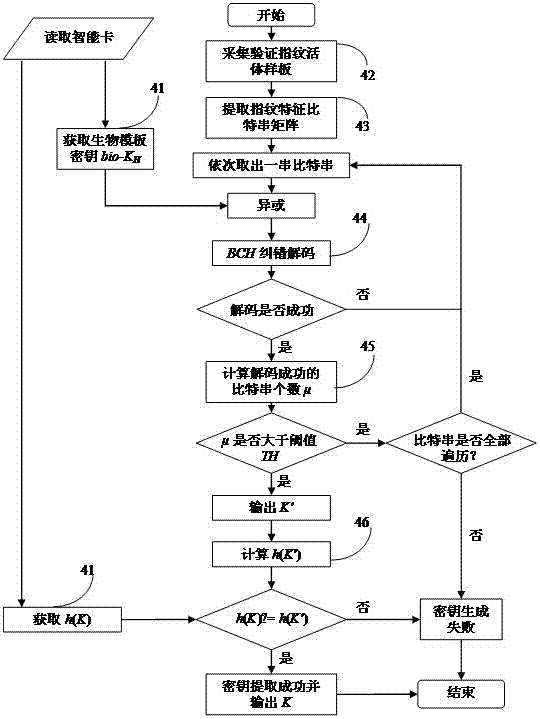
[0056] Key fuzzy extraction process: extract the bit string matrix H of fingerprint minutiae features from the user's fingerprint d '; the bit string matrix H d ' with the biological template auxiliary data bio-K H XOR, decode the result after XOR to obtain a bit string; judge whether the number of bit strings successfully obtained by decoding is greater than or equal to the set threshold, if yes, restore the key K' after ver...
specific Embodiment 3
[0058] On the basis of specific embodiment 2, the method also includes, the bio-K to be preserved H It is stored in the smart card as a biological template, so that the authentication can only be successful if the smart card token and valid fingerprint are provided to the system at the same time, which is equivalent to adding two locks to the system, thereby further improving security. For the accidental loss of the smart card, in order to minimize the security risk, this solution can also realize the new generation of auxiliary data in the smart card, that is, it has revocability.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com