Cooperative protection system of security of electric power wide area Internet and protection method thereof
A protection system and Internet technology, applied in the electric power wide-area Internet security collaborative protection system and its protection field, can solve the problems of inability to guarantee the safety of electric power intelligent terminals, blurred network boundaries, and increased exposure of power grid information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0047] The main types of security services in the power wide-area interconnection network include: security data monitoring (including Events, Notification), remote security control, data security processing, and combination with traditional security communication services and other security services.
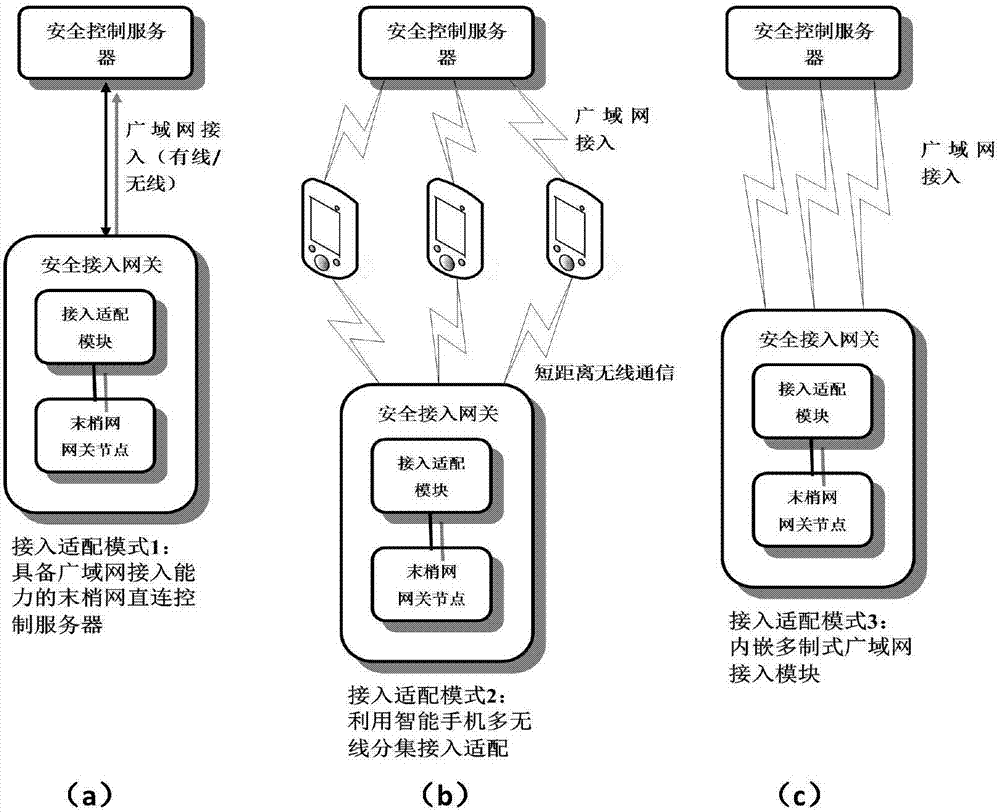
[0048] Considering that the secure data transmission type of the ubiquitous network is different from the Internet of Things, which focuses on secure data collection (one-way upload), the security data transmission types of the ubiquitous network include: secure data collection (uplink), secure broadcast (downlink) and secure transport / bridging classes (bidirectional) like figure 1 In (a), (b), (c) shown.
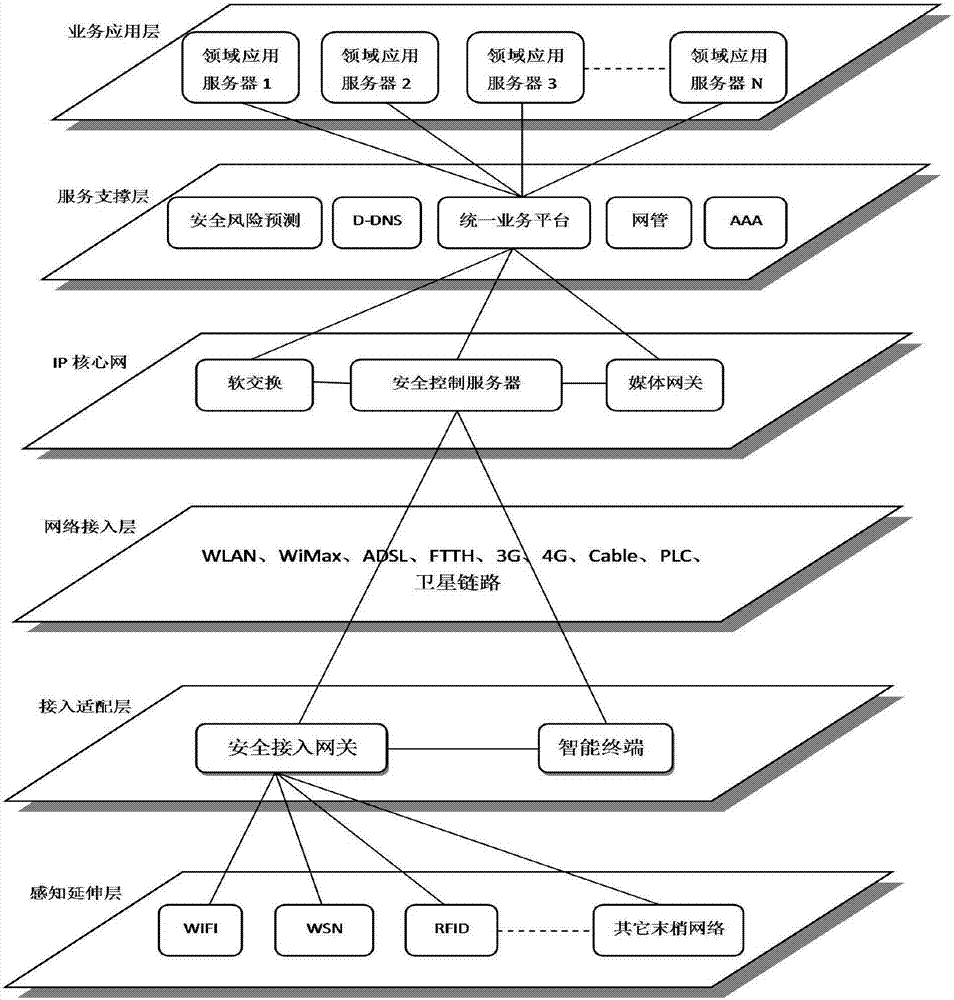
[0049] The present invention provides an electric power wide-area Internet security collaborative protection system, by adding two main functional entities of fusion security access gateway (abbreviated as security access gateway) and virtual reconstruction security control ...
Embodiment 2
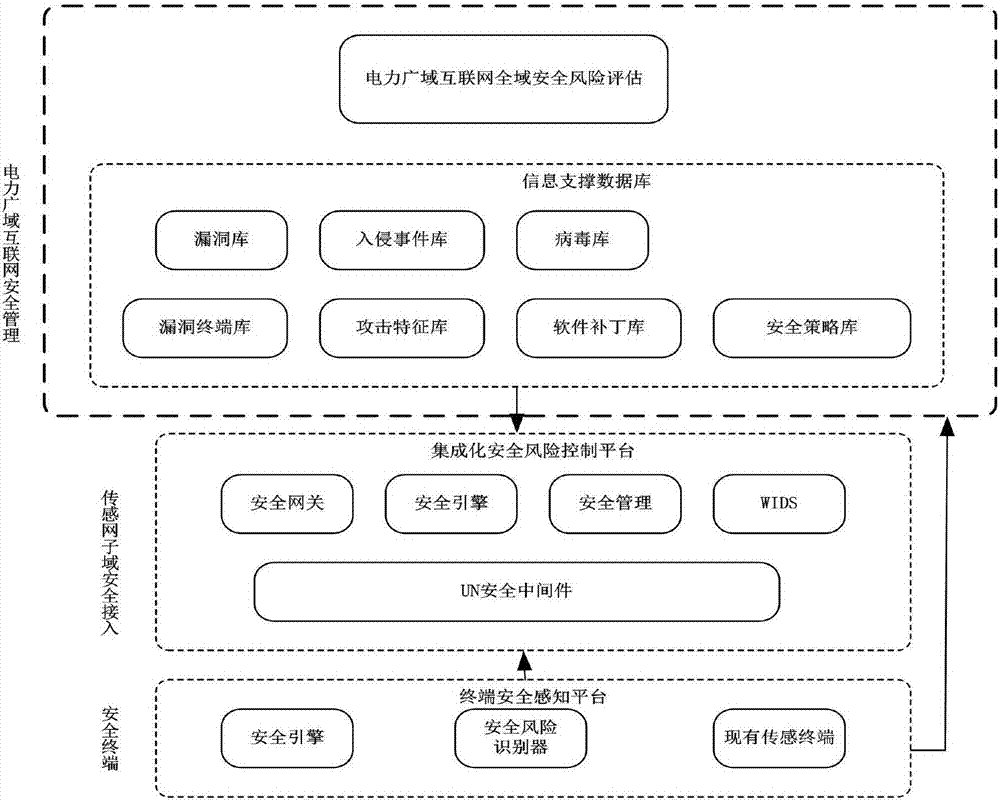
[0061] Since the power wide-area Internet system has distributed, hierarchical, heterogeneous spatial characteristics and dynamic evolution time characteristics, security also has dynamic and heterogeneous spatio-temporal characteristics, and its security life cycle is divided into: protection, detection, prediction, Four stages of response. The present invention formally defines security policies, related concepts, relations and operations of policy trees in Z mode, proposes construction methods of security policies, correctness verification of abstract descriptions, proves security policy consistency theorem, and designs automatic check of policy consistency method.
[0062] The invention provides a protection method for a power wide-area Internet security collaborative protection system. The protection method includes four sub-strategies of construction protection, detection, prediction and response;
[0063] The four sub-strategies are taken as sub-steps in each stage of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com