A ddos detection method based on deep learning
A DDOS and detection method technology, applied in the field of network communication, can solve the problems of ferocious attacks and difficult prevention
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
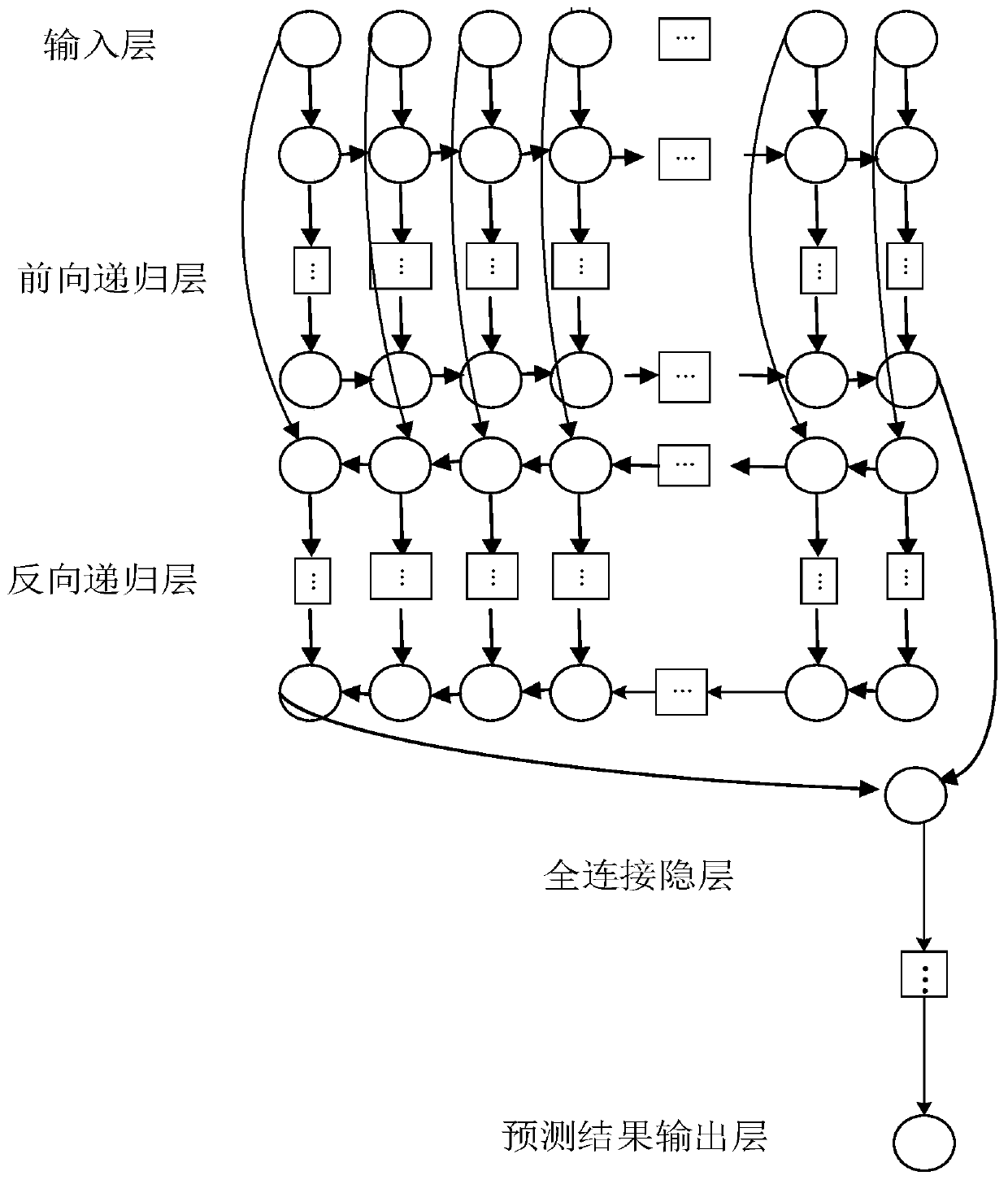
[0040] The present invention will be further described below in conjunction with embodiment.
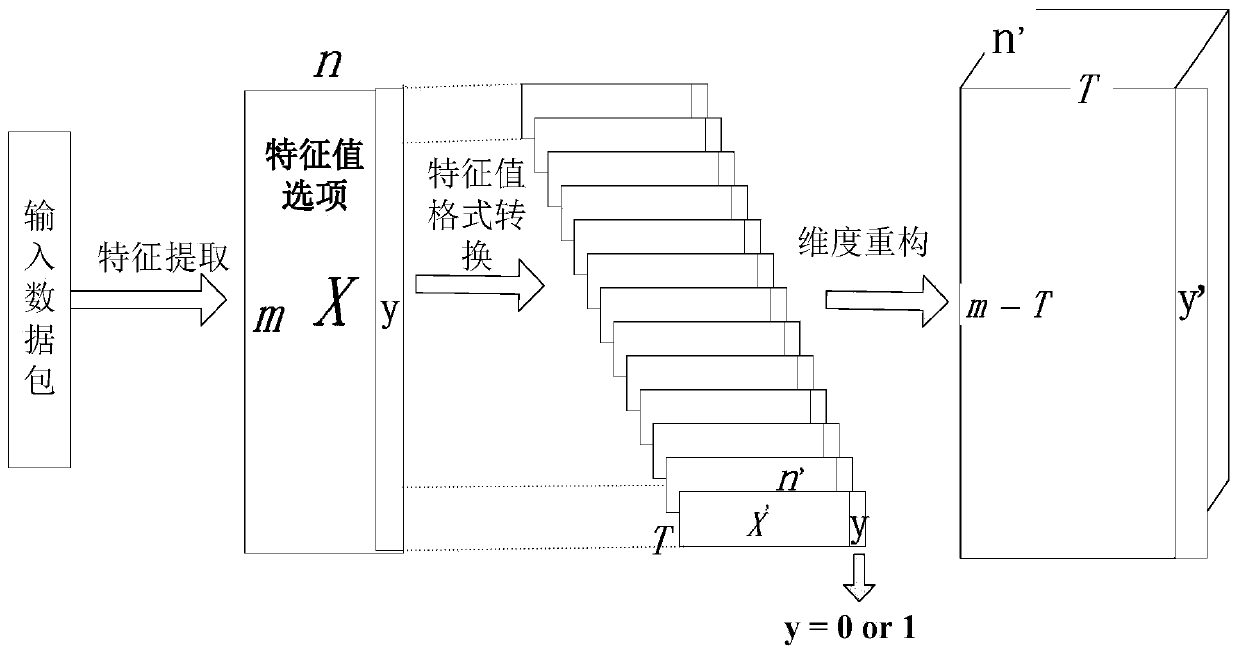
[0041] The specific process of DDOS detection involved in the present invention can be described as follows:
[0042] The open source network data set ISCX2012 (Information Security Center of Excellence 2012) is used as a sample of the deep learning network model in the DDoS attack detection scheme based on deep learning. ISCX2012 records 7 days of traffic information in the real network environment, including legitimate network traffic and various types of malicious DDoS attack traffic.
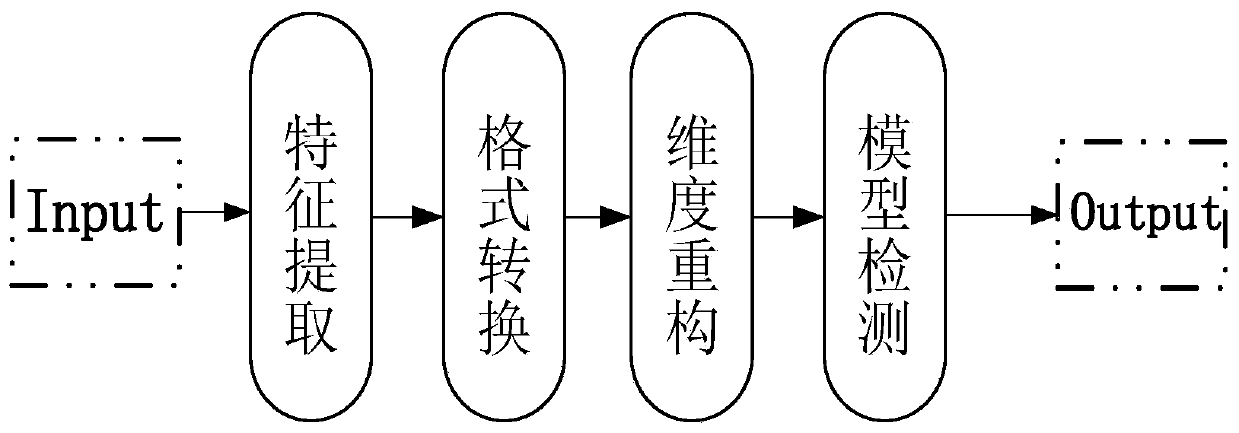
[0043] (1) The specific embodiment of the feature processing stage
[0044] (1.1) Extract 20 data message fields from the ISCX2012 dataset as feature values, and define the corresponding data types of the fields. The specific content is shown in Table 1, and a set of specific examples about these 20 fields are given.
[0045] Table 1 Data characteristic field type
[0046]
[0047]
[0048...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com