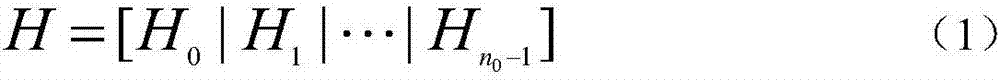Secure lightweight McEliece public key mask encryption method
An encryption method and masking technology, which is applied in the field of information security, can solve the problems of being unable to resist power consumption analysis and large key size, and achieve the effects of resisting power consumption analysis, resisting quantum computing attacks, and reducing the volume of keys
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The following are specific embodiments of the present invention, and further clearly and completely describe the technical solutions of the present invention in conjunction with the accompanying drawings. The quasi-dyadic error-correcting code C has code length n=128, dimension k=64, codimension r=64, and code error-correcting ability t=49.
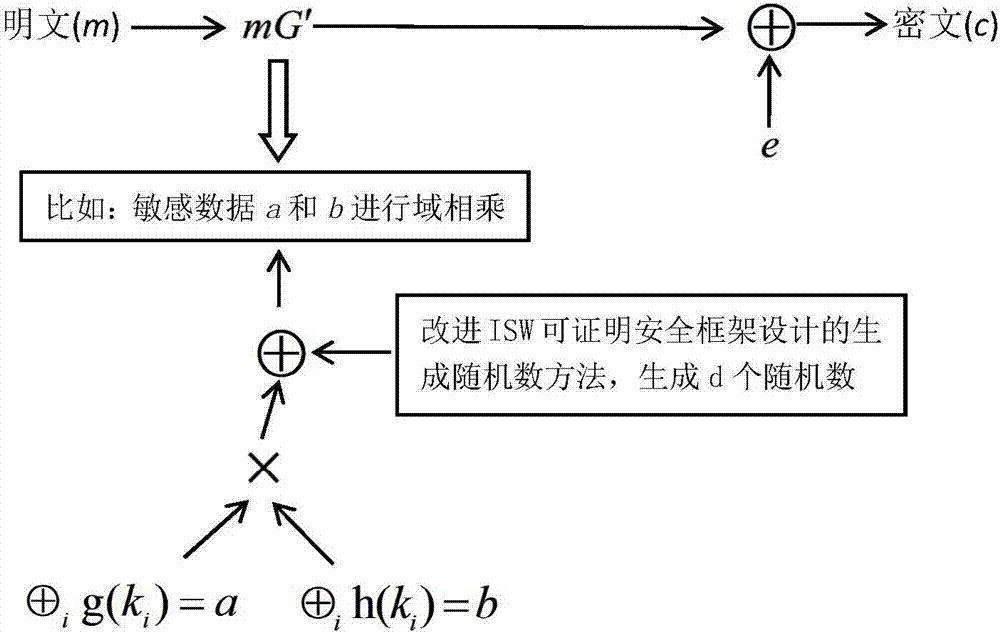
[0046] A secure and lightweight McEliece-type public key encryption method based on Quasi-Dyadic MDPC codes, including the construction of McEliece encryption algorithms with small key size and the design of mask protection methods against energy analysis attacks :
[0047] One, the construction process of the Quasi-Dyadic MDPC code McEliece cryptographic algorithm that described key volume is little comprises the steps:
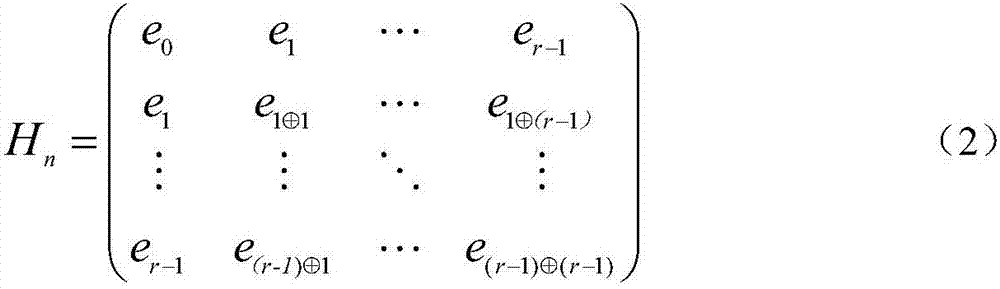
[0048]Step 1, construct Quasi-Dyadic MDPC code: in finite field Above, the form of the density check matrix is designed, n in this embodiment 0 = 2:
[0049] H=[H 0 |H 1 ] (1)
[0050] where H 0 and H ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com