Phishing website processing method and device
A technology of phishing websites and processing methods, applied in the network field, can solve problems such as difficulty in participation, inability of websites to promptly and proactively discover phishing websites, information security and property security threats of enterprises and users phishing websites, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] Such as figure 1 As shown, the present embodiment provides a method for processing phishing websites, the method comprising:
[0040] Step S110: Obtain traffic data of the website server;
[0041] Step S120: analyzing the traffic data of the website server, determining the domain name information of the website visited by the terminal and the communication identification of the terminal;
[0042] Step S130: Determine whether the website accessed by the terminal is a phishing website or a suspected phishing website according to the domain name information;
[0043] Step S140: If the website accessed by the terminal is the phishing website or a suspected phishing website, send reminder information to the terminal through the communication identifier.
[0044] The method for processing phishing websites described in this embodiment can be applied to enterprise servers or community servers that provide network services. For example, a bank server that provides banking se...
Embodiment 2
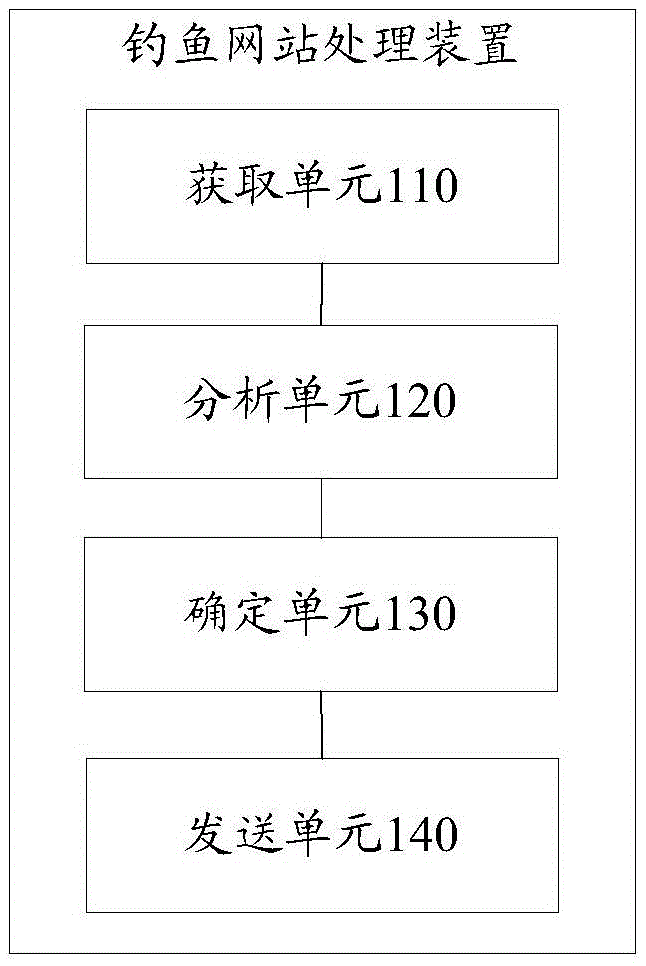
[0080] Such as image 3 As shown, the present embodiment provides a device for processing phishing websites, the device comprising:
[0081] An acquisition unit 110, configured to acquire traffic data of the website server;
[0082] The analysis unit 120 is configured to analyze the traffic data of the website server, determine the domain name information of the website visited by the terminal and the communication identification of the terminal;
[0083] A determining unit 130, configured to determine whether the website accessed by the terminal is a phishing website or a suspected phishing website according to the domain name information;
[0084] The sending unit 140 is configured to send reminder information to the terminal through the communication identifier if the website visited by the terminal is the phishing website or a suspected phishing website.
[0085] This embodiment provides that the device for processing phishing websites can be applied to various website s...
example 1
[0102] The present embodiment provides a kind of phishing website processing method, comprises the following steps:
[0103] Step 1: Remotely capture server-side traffic. When designing this phishing website monitoring and protection system, the traffic data of the website server is obtained through the front-end mirroring or splitting of the enterprise server traffic. The phishing website detection and protection system may be a system running on an enterprise server.
[0104] The second step: traffic data preprocessing. Analyze the acquired traffic data and parse it into recognizable formats and fields.
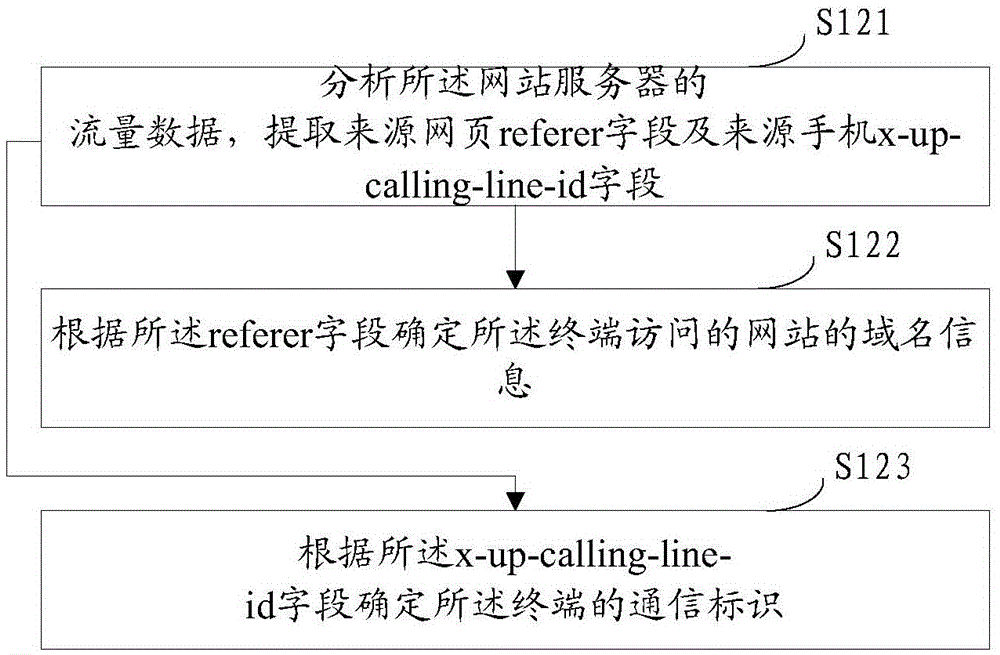
[0105] Step 3: Extract and analyze relevant fields, where the relevant fields may include referer field and x-up-calling-line-id field.
[0106] According to the access traffic generated by the converged access point name (APN) container, extract the relevant referer field for analysis, mainly extract, count and analyze the domain name information in the referer field in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com