Illegal website identification system and method based on critical path
An identification system and critical path technology, which is applied in the field of illegal website identification system based on critical path, can solve the problems of insufficient detection of unknown illegal websites, insufficient accuracy of website clustering methods, inability to quickly identify illegal websites, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] In order to better describe the technical solutions of the present invention, specific examples are given below for further illustration.
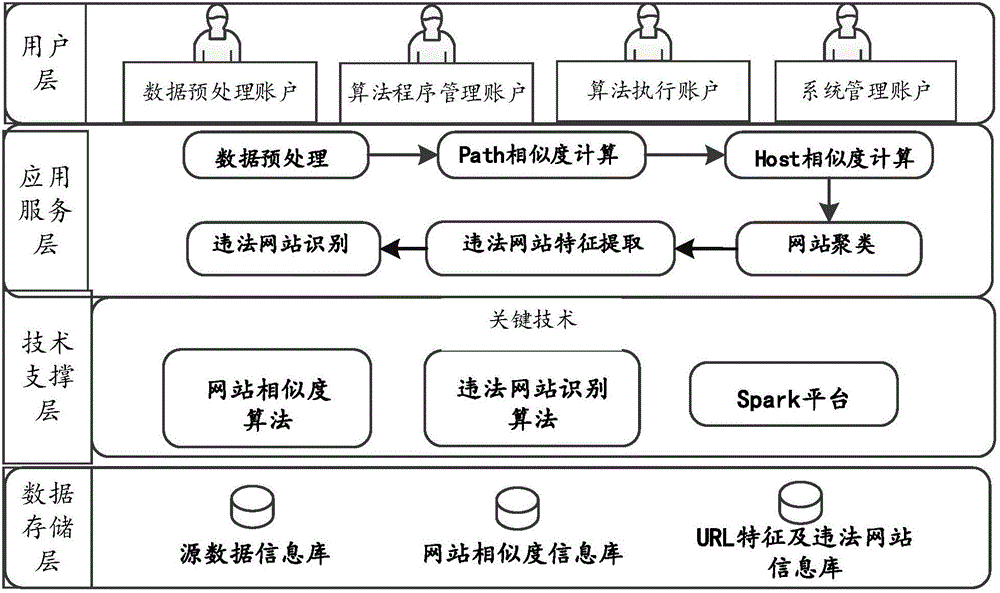
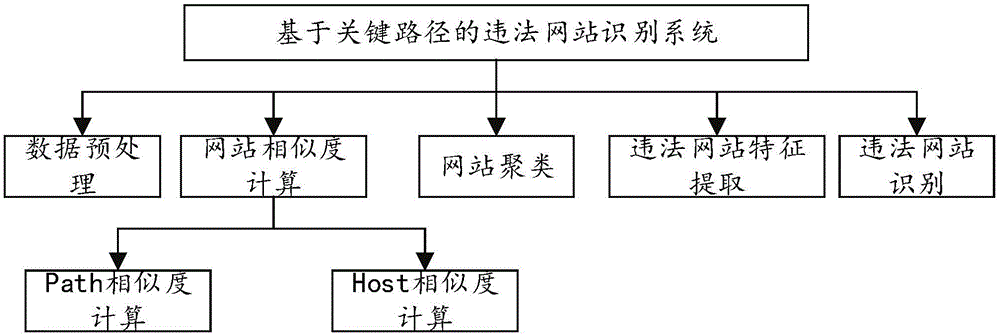
[0056] see figure 1 As shown, the critical path-based illegal website identification system includes user layer, application service layer, technical support layer and data storage layer. ,
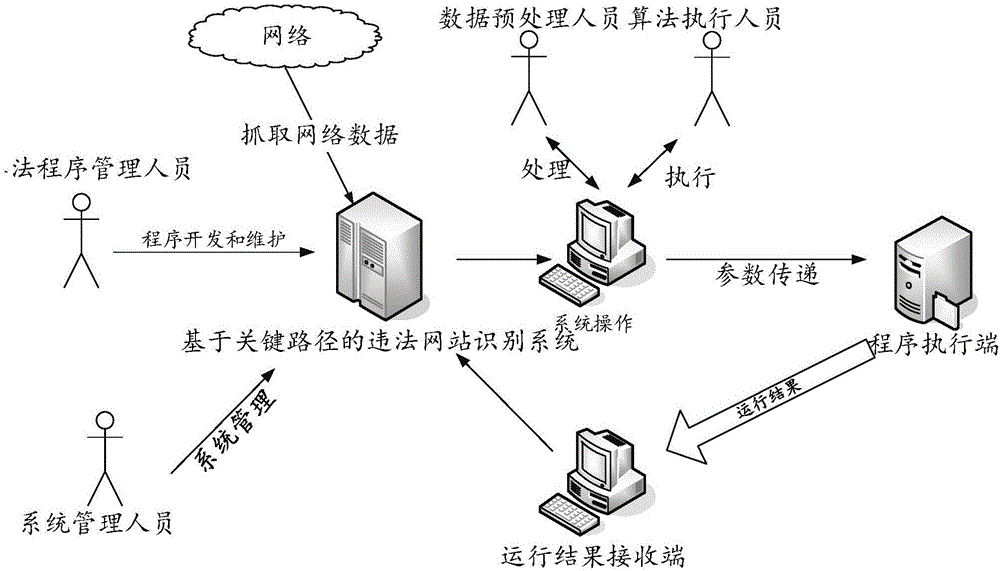
[0057] see figure 2 As shown, the user layer is used to provide the main accounts of the system, including data preprocessing accounts, algorithm program management accounts, algorithm execution accounts and system management accounts, wherein:
[0058] The data preprocessing account is used to realize the development of the data processing program of the system, the operation of the data processing program and the management of the data obtained by the system after data processing. The algorithm program management account is used to realize the algorithm of the system development and maintenance, wherein the algorithm includes a similarity...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com