Method and device for generating identification information
A technology of identification information and identification, applied in the computer field, can solve the problem of low flexibility, achieve the effect of solving low flexibility, supporting client needs, and simplifying the process of generating identification information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
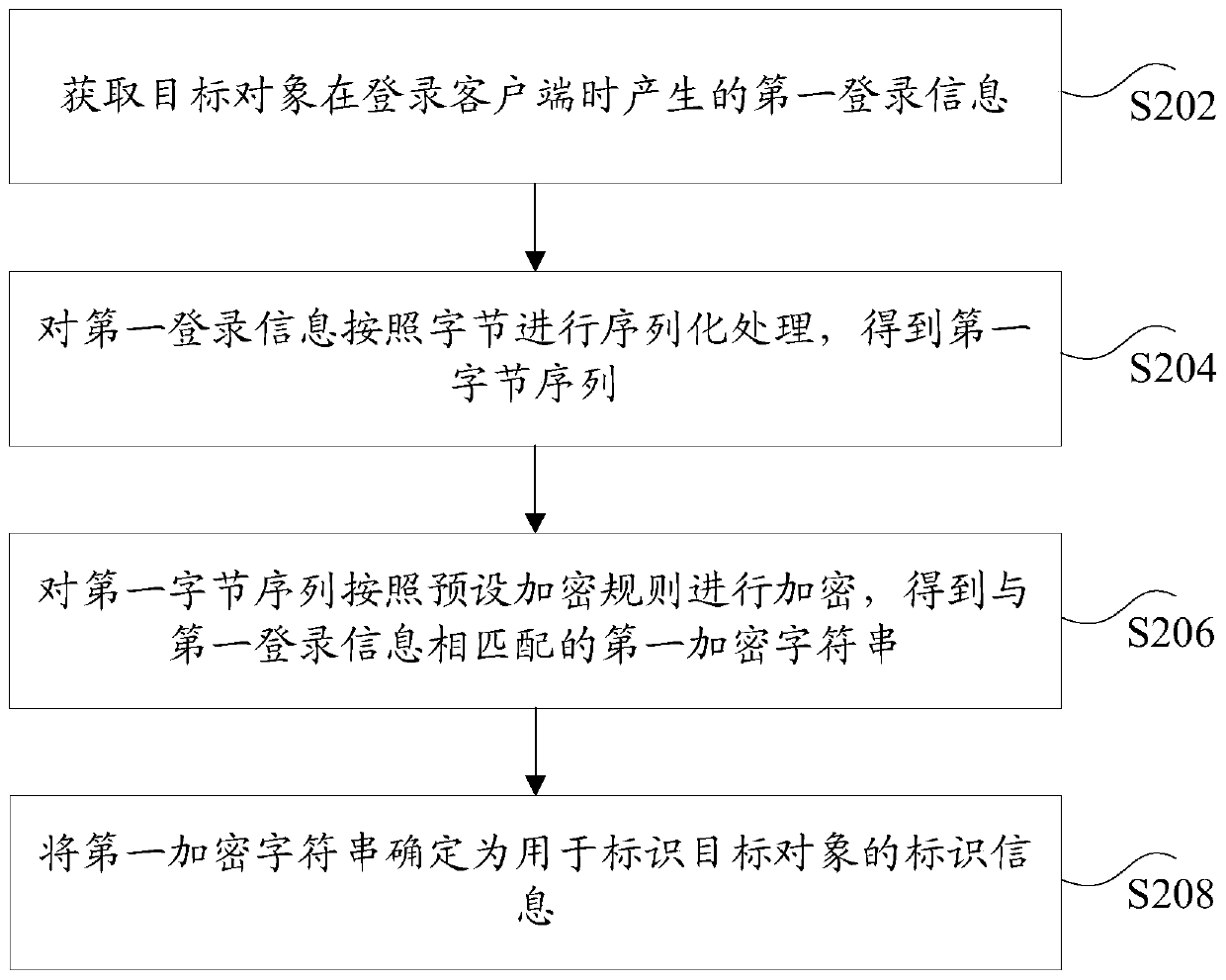
[0031] According to an embodiment of the present invention, an embodiment of a method for generating identification information is provided.
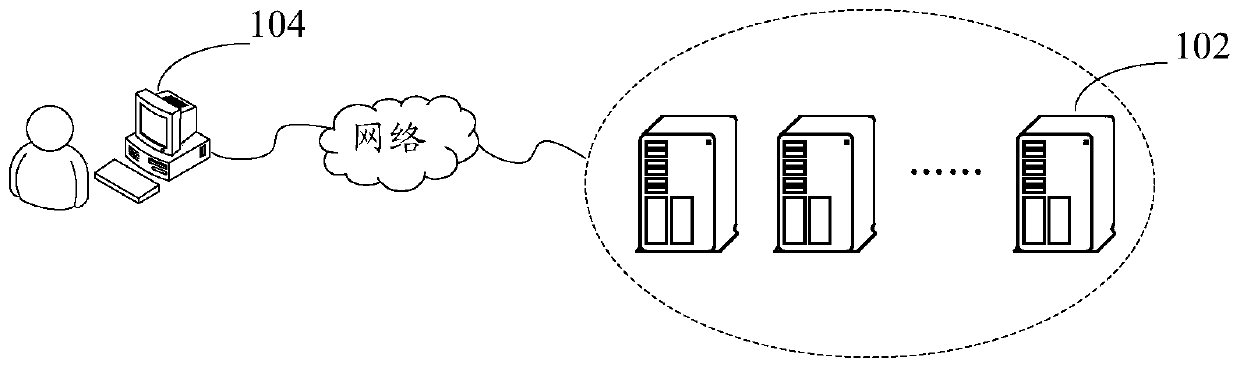
[0032] Optionally, in this embodiment, the method for generating the above identification information can be applied to such as figure 1 In the hardware environment constituted by the server 102 and the terminal 104 as shown. figure 1 It is a schematic diagram of a hardware environment of a method for generating identification information according to an embodiment of the present invention. like figure 1 As shown, the server 102 is connected to the terminal 104 through a network. The above-mentioned network includes but not limited to: a wide area network, a metropolitan area network or a local area network. The terminal 104 is not limited to a PC, a mobile phone, a tablet computer, and the like. The method for generating identification information in this embodiment of the present invention may be executed by the server 102, may also...
Embodiment 2
[0142] The technical solutions of the present invention will be described below in conjunction with preferred embodiments.
[0143] In this embodiment, the login information generated by the target object when logging into the client is user key information, including: user identification information, time identification information, client identification information, client version information and random numbers.
[0144] The method for generating the identification information is introduced below.
[0145] The first step is to extract the key information of the user, including user identification information, time identification information, client identification information, client version information, and random numbers.
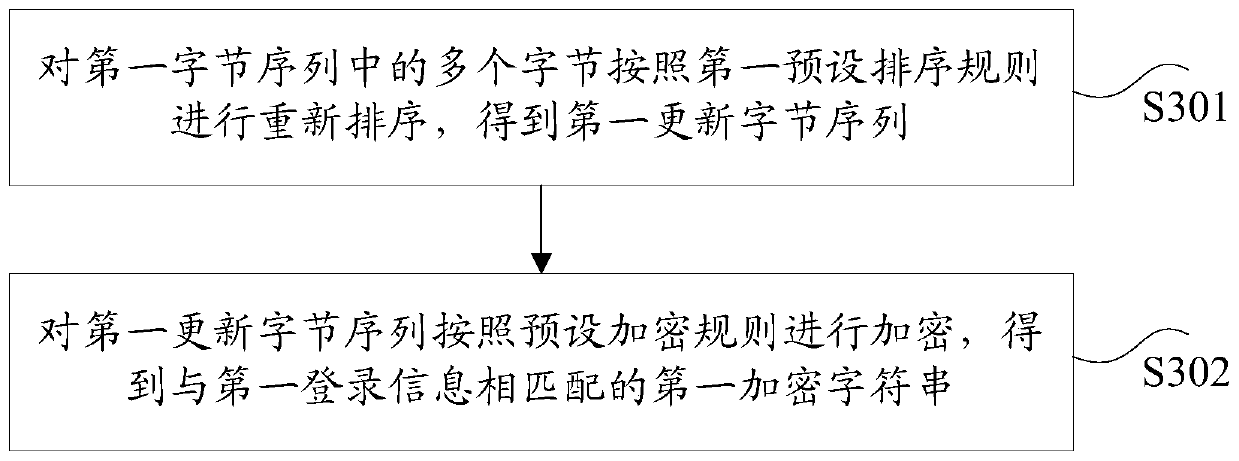
[0146] The second step is to serialize key user information. First, the 2-byte client identification information and the 1-byte version information are combined into a 4-byte value by shifting. Then the user identification information, time identificat...
Embodiment 3
[0159] The application environment of the embodiment of the present invention may refer to, but is not limited to, the application environment in the foregoing embodiments, which will not be described in detail in this embodiment. The embodiment of the present invention provides an optional specific application for implementing the method for generating the above identification information, which is specifically described with a ticket used to represent an identity credential.
[0160] The bearer in the embodiment of the present invention is a video service, and the login supported by each video terminal includes a login mode of an instant messaging application. For the storage of background data and the verification of user identities, a system is required to carry them. Otherwise, two types of data must be stored, one is account number, and the other is OpenID. Among them, OpenID is a user-centric digital identity. The identification framework has open and decentralized main...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com