Strong Privacy Preserving Dual Authentication Method Based on Node Identity and Reputation in Internet of Vehicles
A two-factor authentication and privacy protection technology, applied in the field of information security, can solve problems such as incomplete reliability, achieve the effect of rapid judgment basis, protect trajectory privacy, and enhance accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The specific implementation of the present invention will be further explained in detail below in conjunction with the accompanying drawings.
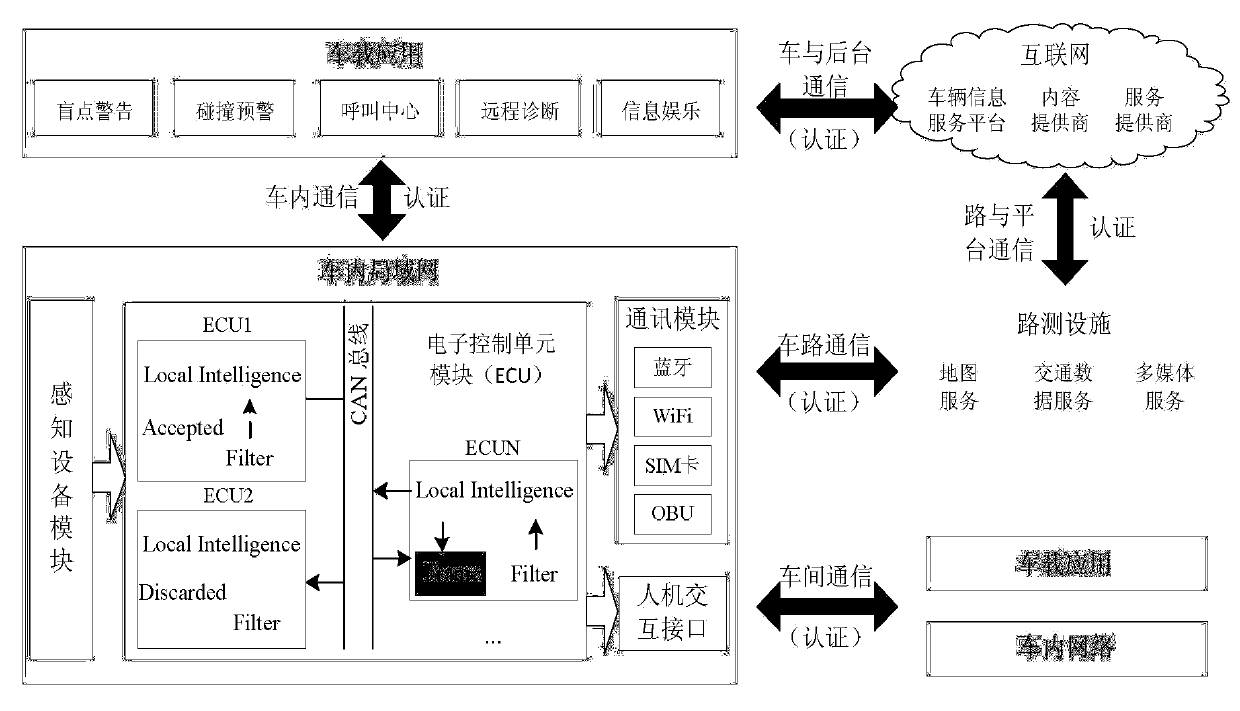
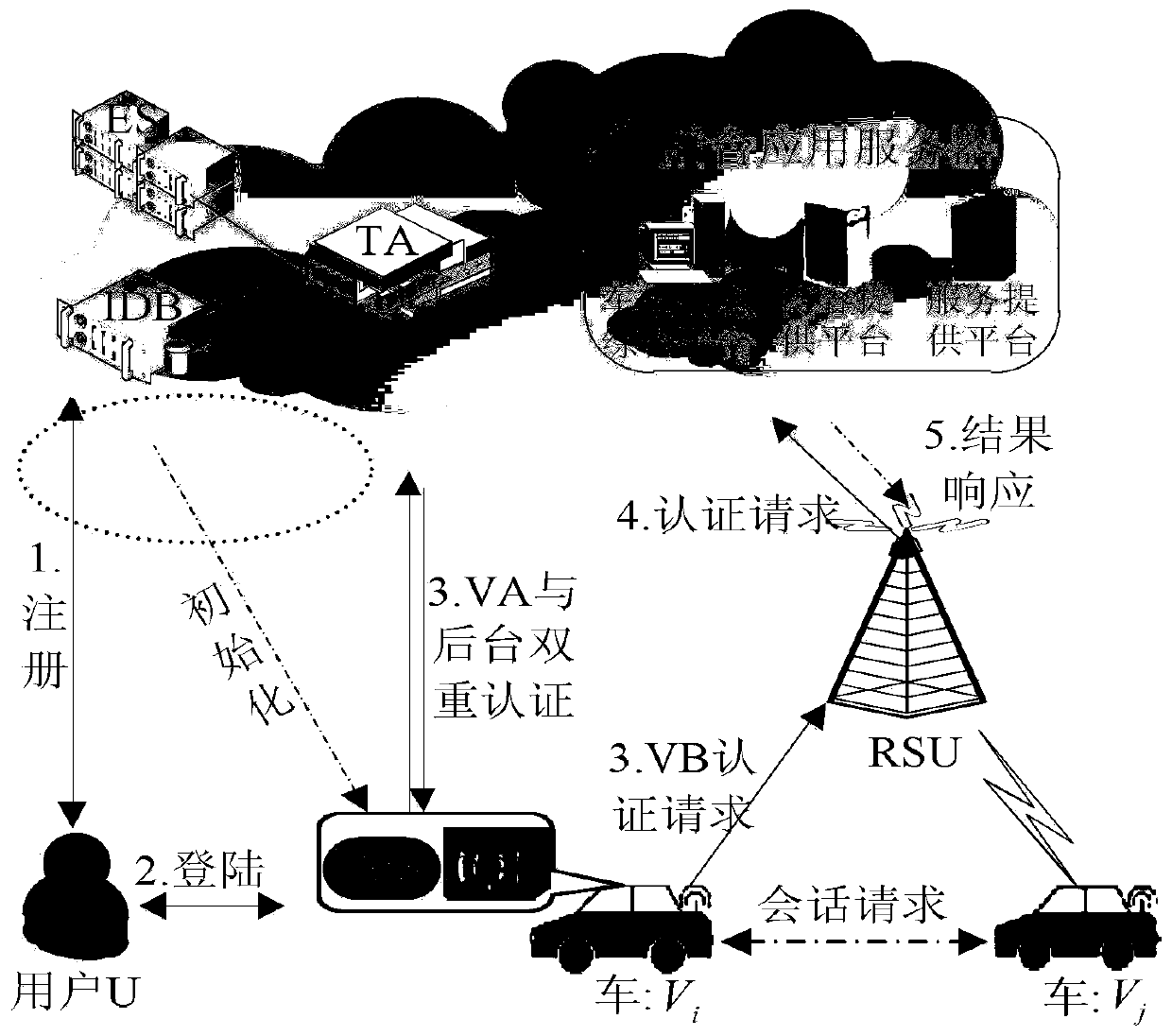
[0022] Such as figure 2 Shown is a schematic diagram of the communication scene between the vehicle node and the background application server and the V2V communication scene of the present invention, image 3 It is a structural diagram of the overall architecture of the authentication system. These include: authentication server (TA: Trust Authority), node reputation evaluation server (ES: Evaluation Server), high reputation node storage server (IDB: IdentityDatabase), intelligent vehicle node (V i ,V j ), and a background application server cluster (AppSC: Application ServerCluster). Since the RSU is responsible for forwarding, the image 3 Not indicated in.
[0023]Such as Figure 4 Shown is a schematic diagram of the vehicle node internal data flow principle of the present invention, including: environmental informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com