System and method for preventing and controlling dissemination of untrusted resources in Internet of Vehicles
A vehicle networking and resource technology, applied in the field of information security, to avoid mistrust, meet real-time requirements, and improve efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The technical solutions in the embodiments of the present invention will be described clearly and in detail below in conjunction with the accompanying drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
[0039] The technical scheme that the present invention solves the problems of the technologies described above is:
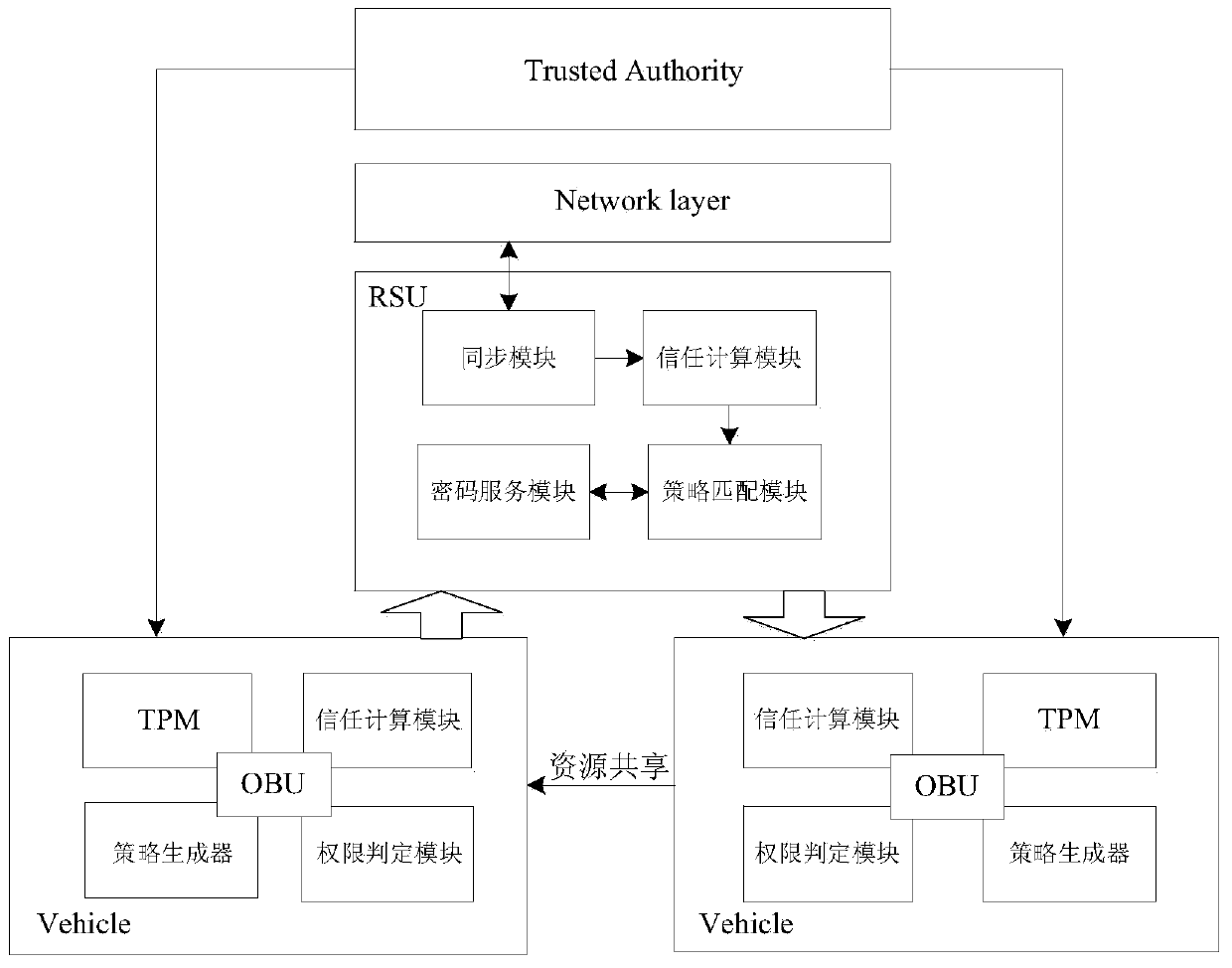
[0040] Such as figure 1 Shown is the overall structure structure diagram of the system of the present invention, including: trusted party TA, roadside infrastructure RSU, vehicle node V A and V B .
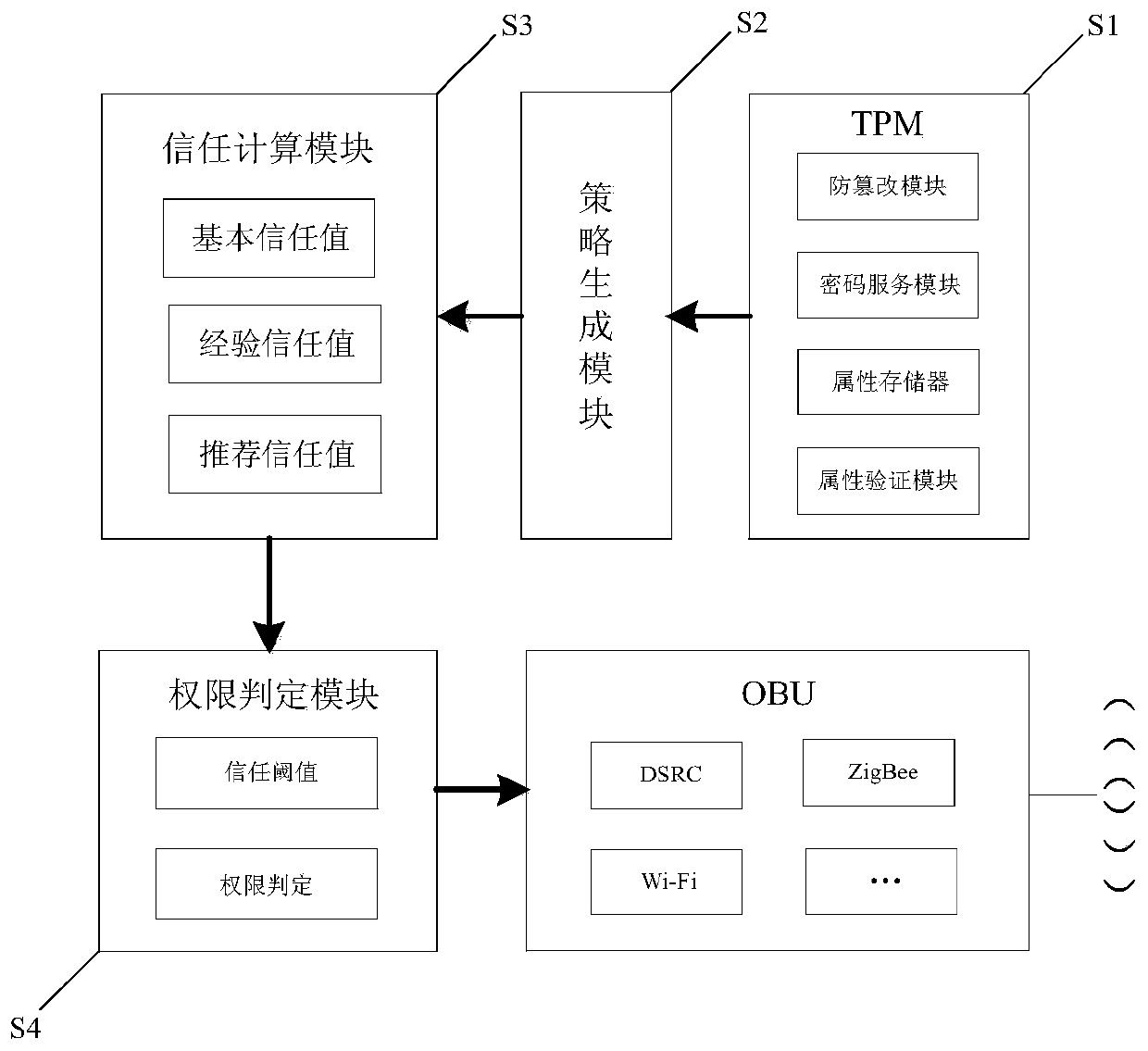
[0041] Such as figure 2 It is a vehicle terminal structure diagram, which is divided into several parts: TPM mainly stores and verifies vehicle attributes, and provides vehicle cryptographic services TPM provides cryptographic security services for vehicles, including CP-ABE technology, RSU digital signature technology, and asymmetric encryption and decryption Technology to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com