Clock frequency error injection attack resisting defense circuit of security chip
A technology of error injection attack and clock frequency, which is applied in the protection of internal/peripheral computer components, etc., can solve the problems of security chips not suitable for low power consumption, complex clock frequency detection circuit, and large chip area occupied, and achieve fast detection speed , simple structure, reduced area and power consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
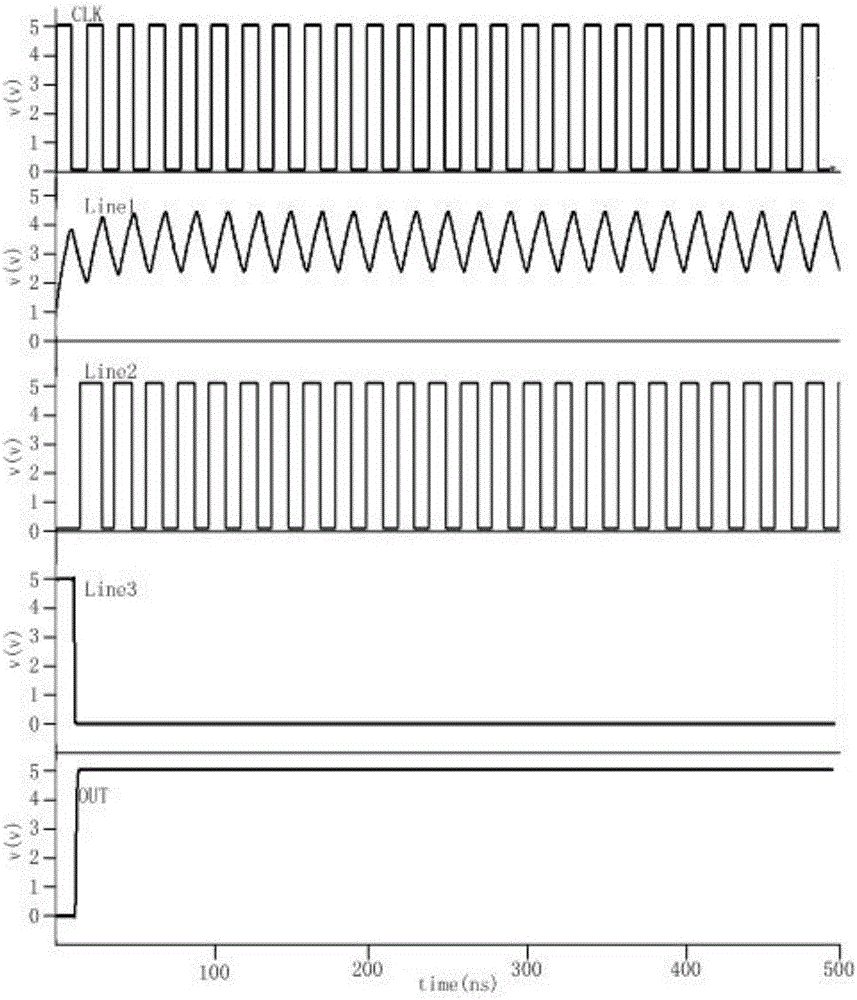
[0036] In this embodiment, a defense circuit against clock frequency error injection attack of a security chip is used to detect the frequency of the clock CLK, such as figure 1 As shown, including detection module 10 and detection module 20:
[0037] The detection module 10 includes: a first NMOS transistor M1, a second NMOS transistor M2, a first transmission gate TG1, a second transmission gate TG2, a third transmission gate TG3, and a fourth transmission gate TG4; and the area of the first NOMS transistor M1 is larger than The second NOMS transistor M2 mainly realizes charging the NMOS capacitor when the clock is at a high level, and discharging the NMOS capacitor when the clock is at a low level;
[0038] The source and drain of the first NMOS transistor are connected in parallel with one end of the first transmission gate TG1, and the gate of the first NMOS transistor is connected in parallel with the other end of the first transmission gate TG1 and then connected in s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com