An identity authentication system and method based on user habitual behavior characteristics
A technology of identity authentication and behavior, which is applied in the field of identity authentication system, can solve problems such as behavior changes that cannot identify the user himself, capture subtle changes in user habitual behavior, etc., and achieve the effect of reducing the risk of passing authentication and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0108] The specific implementation process of this method in the offline micropayment application is as follows:
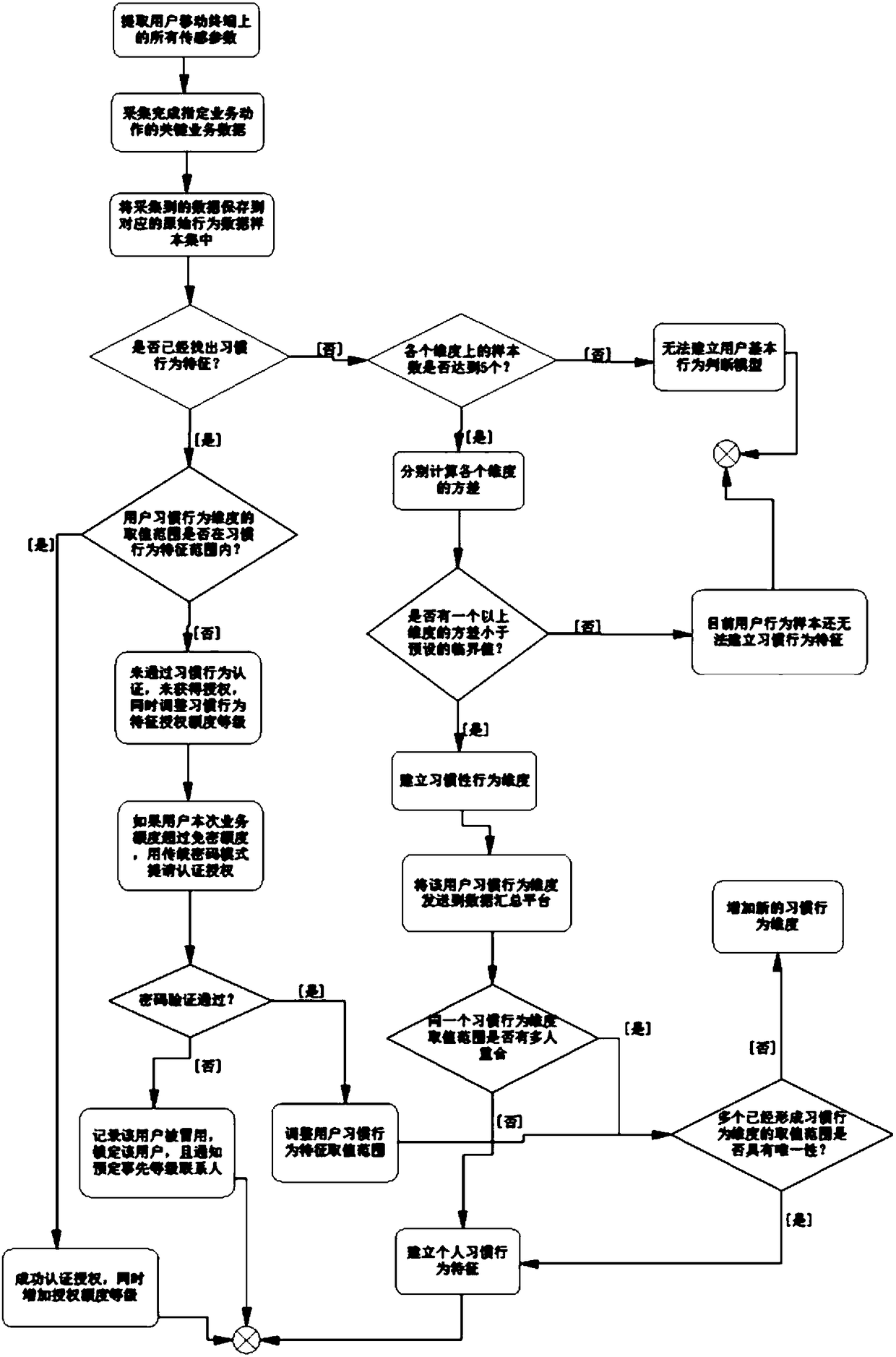
[0109] S1, starting from the user installing the offline micropayment application, the following raw behavioral data samples are continuously collected: the merchant, time point, single consumption amount of the user each time, and gestures when approaching the payment terminal, recorded as: u( x, y, z, t), where x represents the single consumption amount, y represents the merchant, t represents the consumption time, and z represents the gesture feature value;
[0110] S2, continuous collection for one week to obtain 20 effective samples, U={u 1 , u 2 ,...,u 20}
[0111] S21, calculate the standard deviation of the four dimensions of single consumption amount x, merchant y, consumption time t, and gesture action characteristic value z, respectively recorded as Set the variance threshold to be There are the following discrimination results:
[0112]
[0...
Embodiment 2
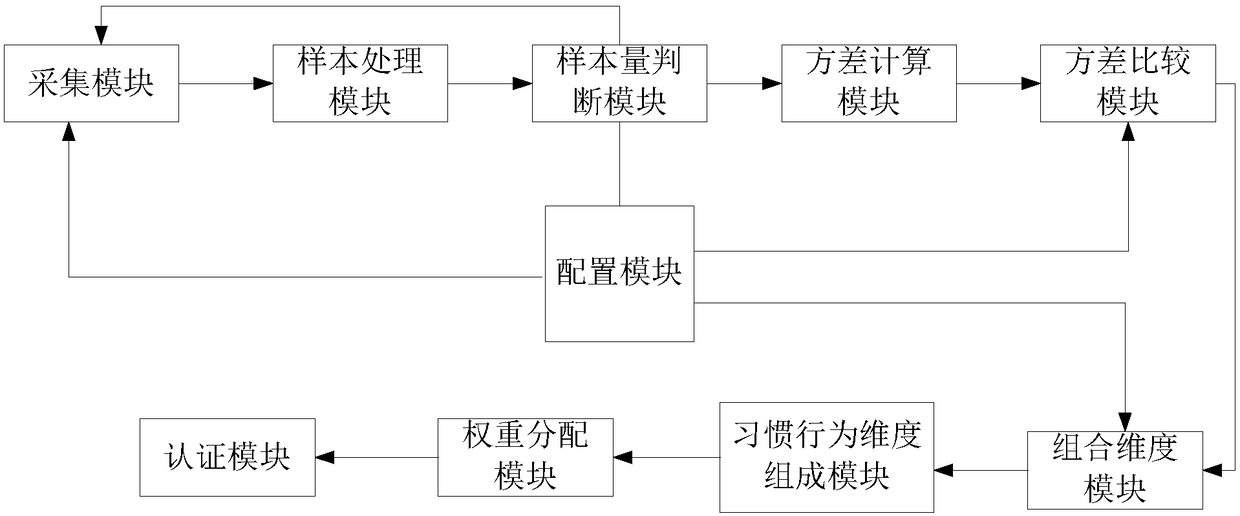
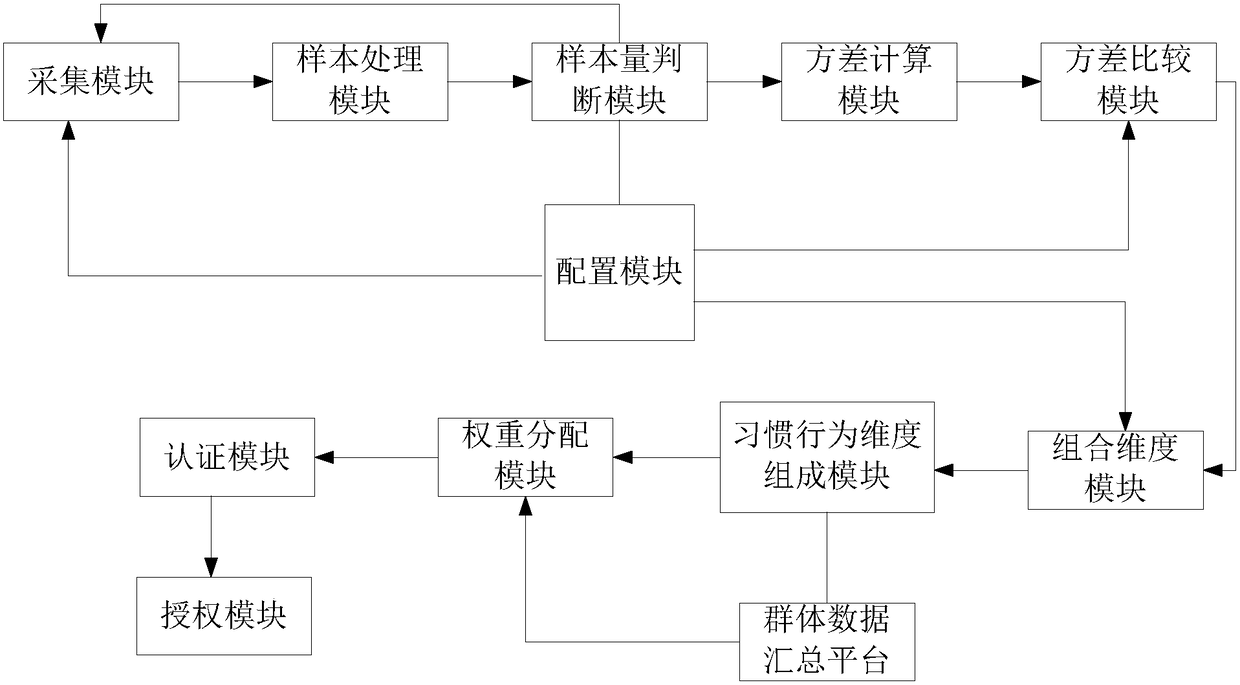
[0131] S1 extracts all sensing parameters on the user's mobile terminal;
[0132] S2 collects business data that completes specified business actions;
[0133] S3 saves the collected business data into the corresponding type of original behavior data sample set;
[0134] S4 judges whether habitual behavior characteristics have been found out;
[0135] If the habitual behavior feature is found, it is judged whether the value range of the user's habitual behavior degree is within the range of the habitual behavior feature;
[0136] If it is within the range, the authorization is successfully authenticated and the authorization level is increased at the same time;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com