Method for realizing follow-up safe access of user data
A technology for secure access and user data, applied in the field of realizing user data follow-up secure access, can solve problems such as limited network transmission speed, loss, impact on public cloud service quality and user experience, etc., to improve data access speed , the effect of increasing the speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
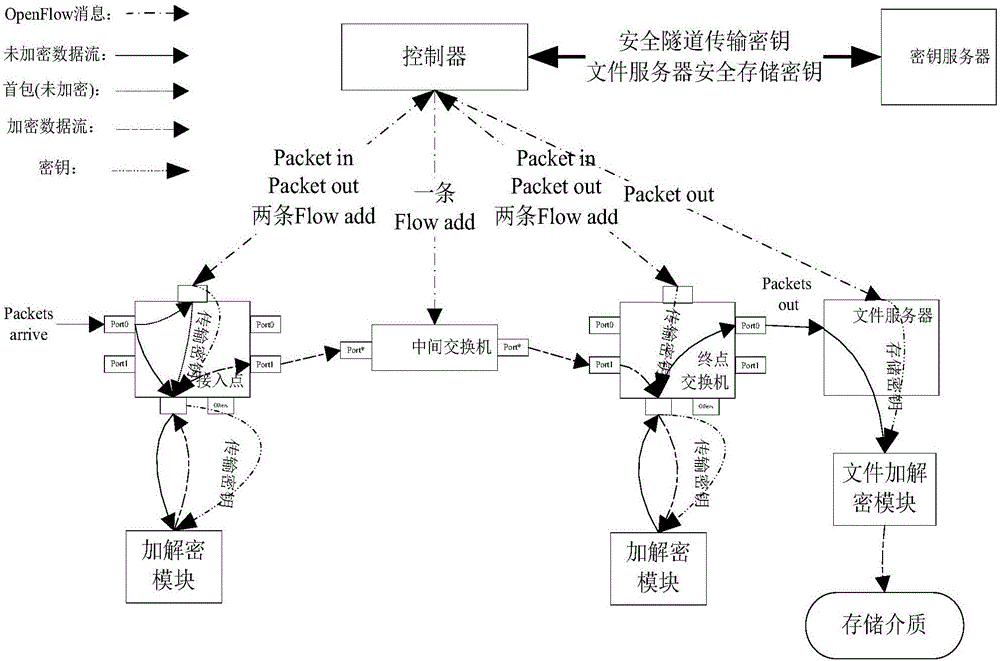
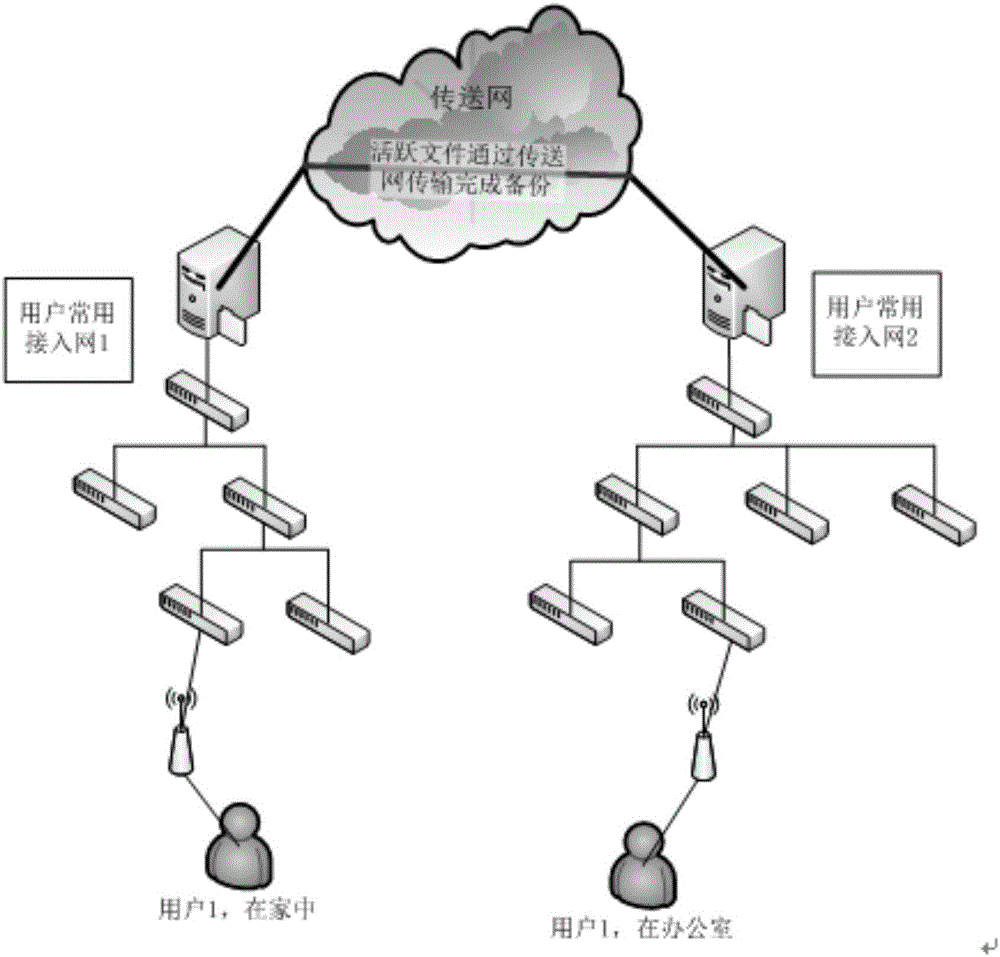
[0051] For the convenience of description, the relevant technical terms appearing in the specific implementation manner are explained first:
[0052] BRAS (Broadband Remote Access Server): Broadband Remote Access Server;
[0053] NAS (Network Attached Storage): Network Attached Storage;
[0054] AP (AccessPoint): access point;
[0055] SDN (Software Defined Networking): Software Defined Network;
[0056] OpenFlow: The standard for the southbound interface of the controller in the SDN architecture determined by the standardization organization ONF;
[0057] Packet in: OpenFlow protocol message, which enables the switch to send data packets to the controller;
[0058] Packet-out: OpenFlow protocol message, enabling the controller to send packets through the switch;
[0059] Flow add: OpenFlow protocol message, which enables the controller to add a flow entry to the switch;
[0060] Intel DPDK (Intel Dataplane Packet Development Kit): An open-source packet processing softwar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com