Method for actively defending against Trojan horse based on virtual environments
A virtual environment, active defense technology, applied in the field of network security, to achieve the effect of strengthening security and changing the operating environment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
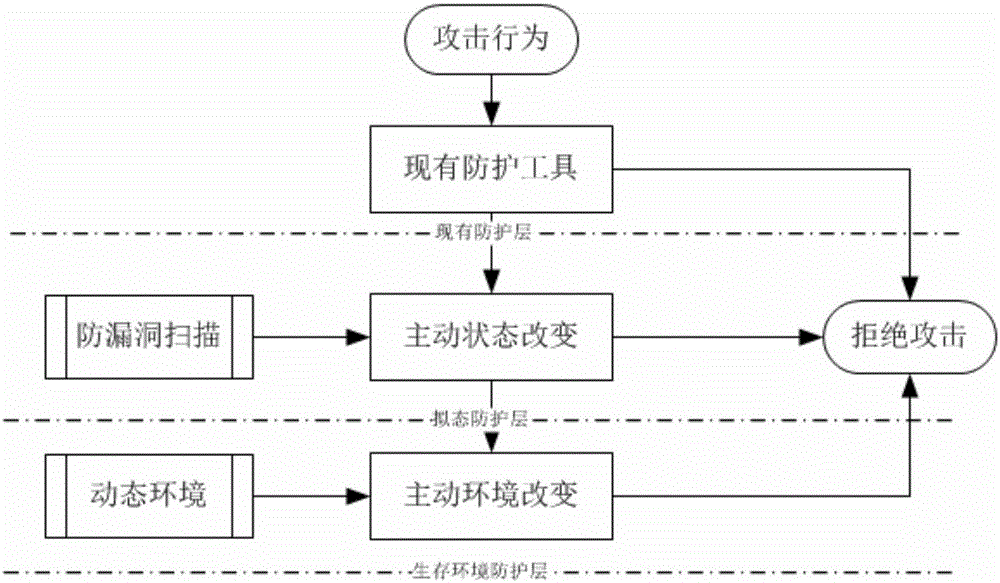
[0041] According to the attached figure 1 and 2 , describe in detail the specific implementation process of the present invention.
[0042] The present invention is based on the method for the active defense Trojan of virtual environment, comprises the following steps:
[0043] 1. During system initialization or operation, a virtual environment is automatically built; this step is realized through the following sub-steps:
[0044] (1.1) Build a virtual environment V={v i |i=1,2,···,n}, where n is the number of virtual systems built, v i is the i-th virtual environment;
[0045] (1.2) Use different operating systems Sys={sys in each virtual environment i |i=1,2,···,n}, where, sys i is the operating system of the i-th virtual environment;
[0046] (1.3) Use different configuration environments Ev={ev in each virtual environment i |i=1,2,···,n}, where, ev i is the configuration parameter of the i-th virtual environment;
[0047] (1.4) In the virtual environment v i Deplo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com