Method and device for recognizing, authenticating, unlocking and encrypting storage space by using human face
A technology of encrypted storage and face recognition, which is applied in biometric recognition, character and pattern recognition, instruments, etc., can solve the problems of cracking, endangering system security, non-randomness and small length of passwords, etc., and achieves difficult memory, easy cracking and prevention The effect of falsification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
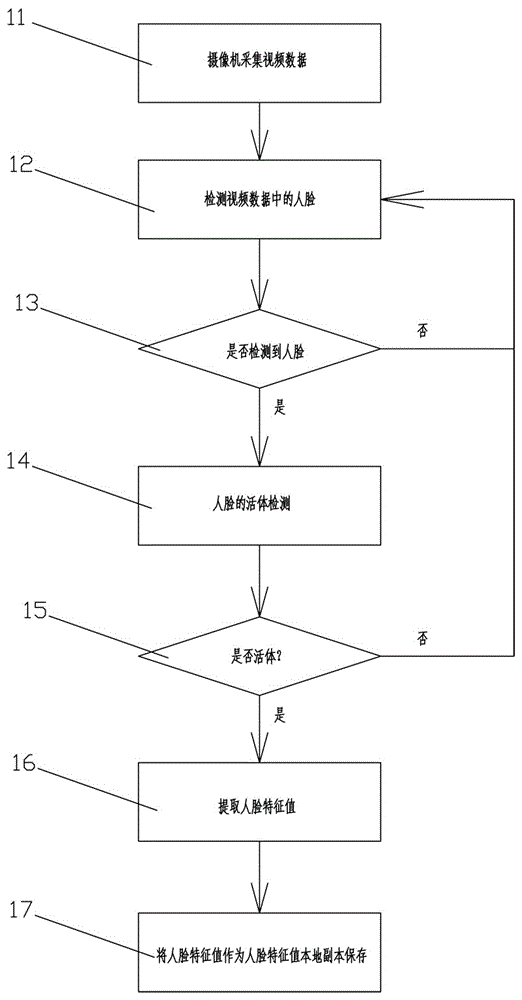
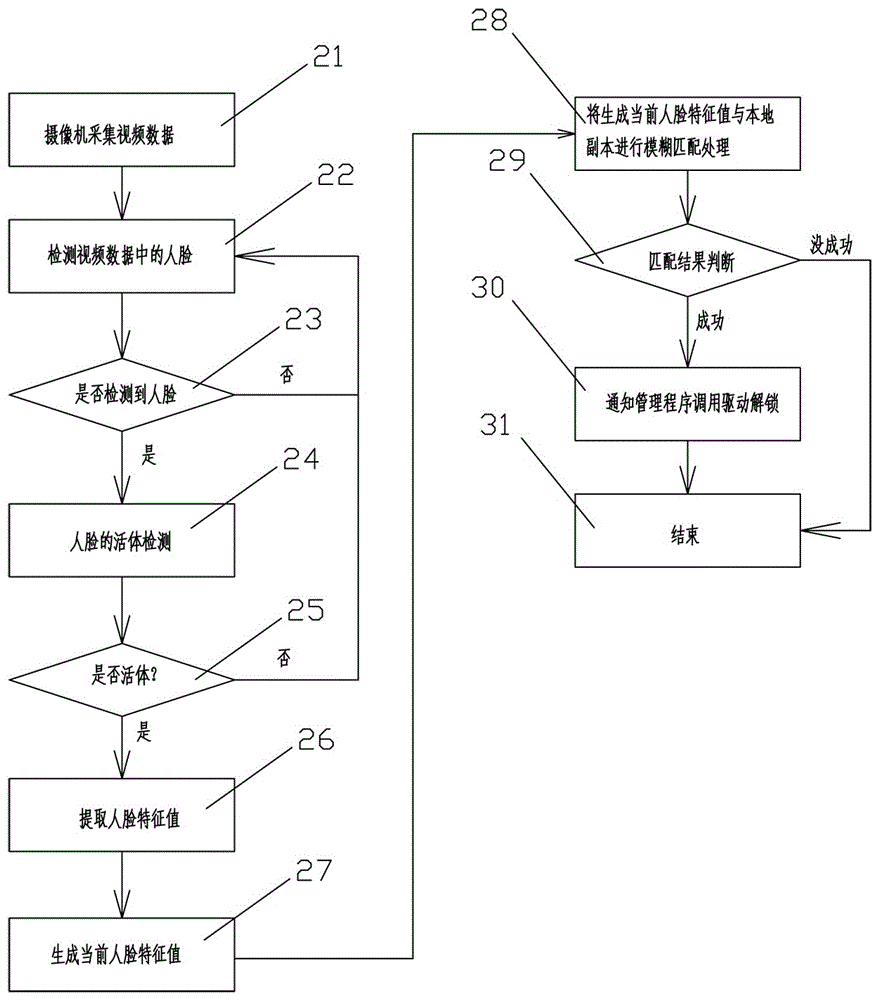
[0050] See figure 1 and figure 2 , figure 1 and figure 2 Revealed is a method of unlocking encrypted storage space with facial recognition authentication, including:
[0051] Face registration steps
[0052] 11. Use a camera to collect video data; of course, the camera in this step can also be replaced by a high-speed camera (the same below);
[0053] 12. Detect the face image in the video from the collected video data; the technology to detect the face is the existing technology, mainly the pre-stored face image, and detect whether there are several main parts of the face for comparison Yes, if the comparison is successful, the face is detected, otherwise the face is not detected;
[0054] 13. Whether the face image is detected, if not, return to step 12, if yes, enter step 14;
[0055] 14. Human face detection;
[0056]15. Whether the human face is alive or not, within the predetermined time, if the physiological parts of the human face that can move are detected, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com