A fingerprint identification method and mobile terminal
A fingerprint identification and mobile terminal technology, applied in the field of communication, can solve the problem of difficult to provide security strength fingerprint payment guarantee, and achieve the effect of avoiding malicious tampering, protecting fund security and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0028] The first embodiment of the present invention provides a fingerprint identification method, which is applied to a mobile terminal provided with an embedded security chip and a trusted area module. Send to the trusted zone module, so that the trusted zone module digitally signs the result of the judgment and then sends it to the mobile terminal.
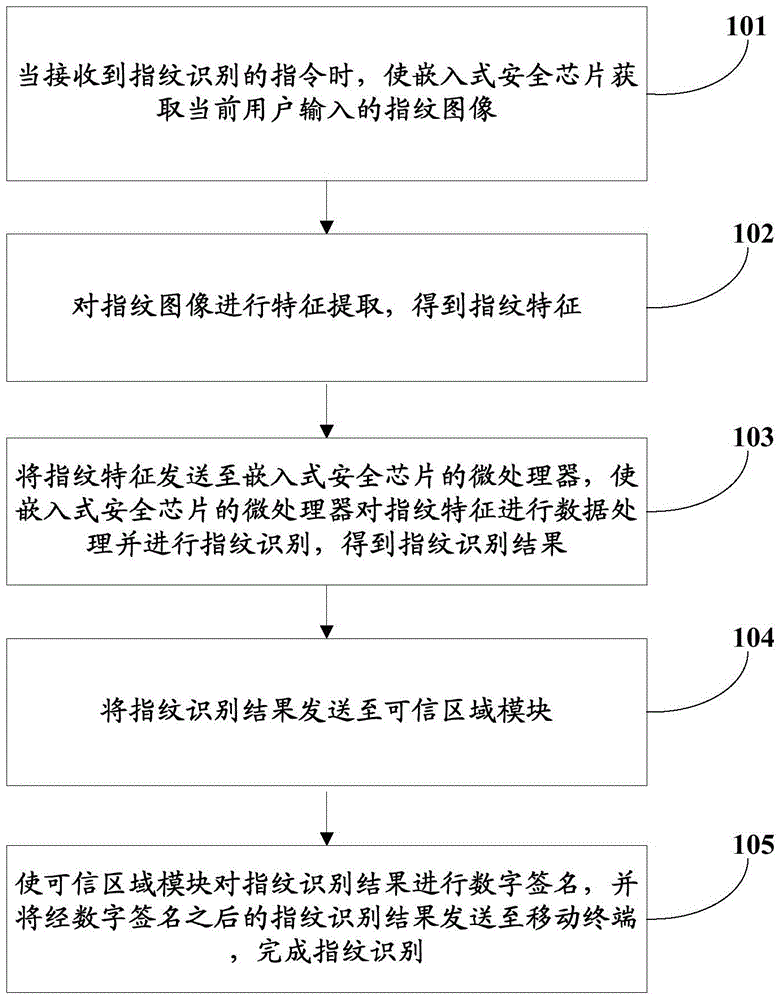
[0029] Specifically, see figure 1 , the first embodiment of the present invention provides a fingerprint identification method, the method comprising:
[0030] Step 101, when receiving an instruction for fingerprint identification, make the embedded security chip acquire the fingerprint image currently input by the user.
[0031] Among them, the acquisition of fingerprint images is carried out inside the embedded security chip, and remote attacks cannot invade the inside of the chip, and cannot obtain or tamper with fingerprint features.
[0032] Step 102, perform feature extraction on the fingerprint image to obtain fingerpr...
no. 2 example
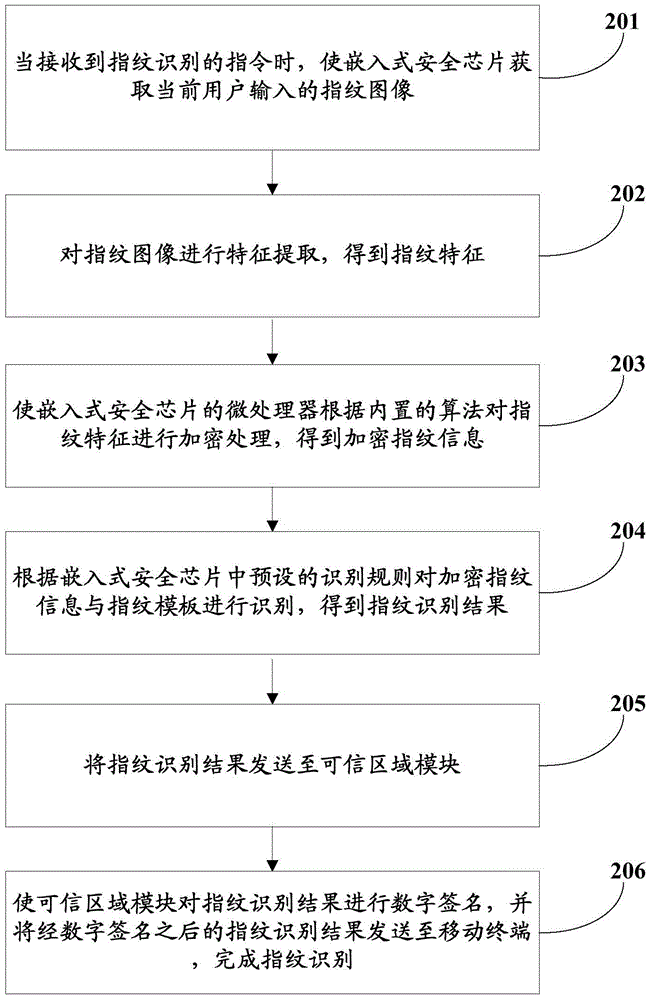
[0051] Such as figure 2 As shown, the second embodiment of the present invention provides a fingerprint identification method applied to a mobile terminal provided with an embedded security chip and a trusted area module, the method comprising:
[0052] Step 201 , when receiving an instruction for fingerprint identification, acquire the fingerprint image input by the current user so that the embedded security chip acquires the fingerprint image input by the current user.
[0053] In this step, the acquisition of the fingerprint image is carried out inside the embedded security chip, and remote attacks cannot invade the inside of the chip, and cannot obtain or tamper with fingerprint features.
[0054] Step 202, perform feature extraction on the fingerprint image to obtain fingerprint features.
[0055] In the embodiment of the present invention, the fingerprint identification technology does not directly store the fingerprint image, but extracts the features of the fingerpri...
no. 3 example
[0071] The first to second embodiments of the present invention described above are the content of the fingerprint identification method provided by the present invention, and the mobile terminal provided by the fourth embodiment of the present invention is introduced below.
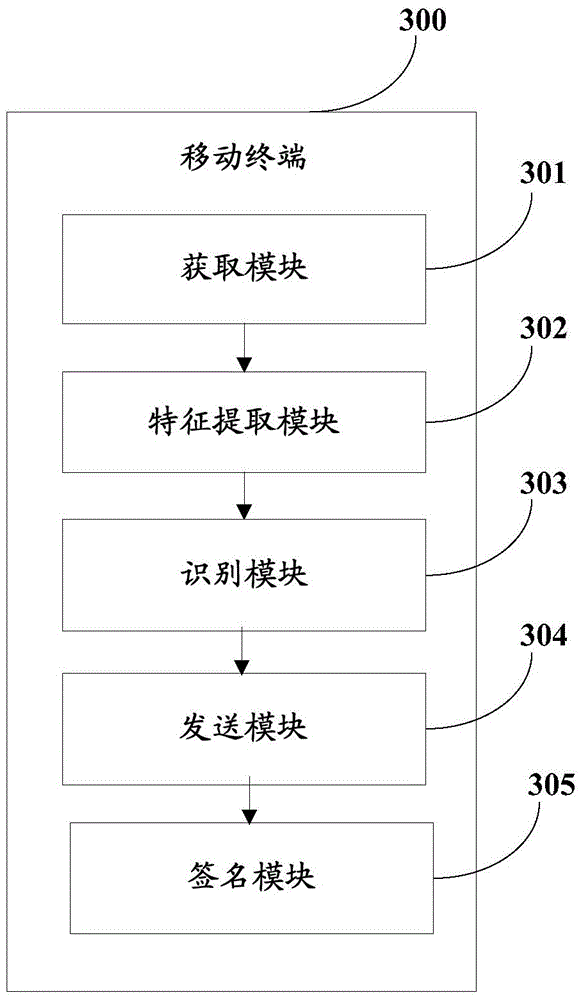
[0072] see image 3 , image 3 is a block diagram of the mobile terminal provided by the third embodiment of the present invention. image 3 The mobile terminal 300 shown includes: an acquisition module 301 , a feature extraction module 302 , an identification module 303 , a sending module 304 and a signature module 305 .
[0073] An acquisition module 301, configured to enable the embedded security chip to acquire the fingerprint image currently input by the user when receiving an instruction for fingerprint identification;
[0074] Among them, the acquisition of fingerprint images is carried out inside the embedded security chip, and remote attacks cannot invade the inside of the chip, and cannot obt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com