A mail encryption system based on a domestic commercial cipher code chip and an implementation method thereof
An encryption system and commercial encryption technology, applied in the field of mail encryption systems based on domestic commercial encryption chips, can solve the problems of inability to eradicate privacy leakage, increase user cost, violate user privacy, etc., to ensure security and reliability, learning The effect of low cost and improved safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
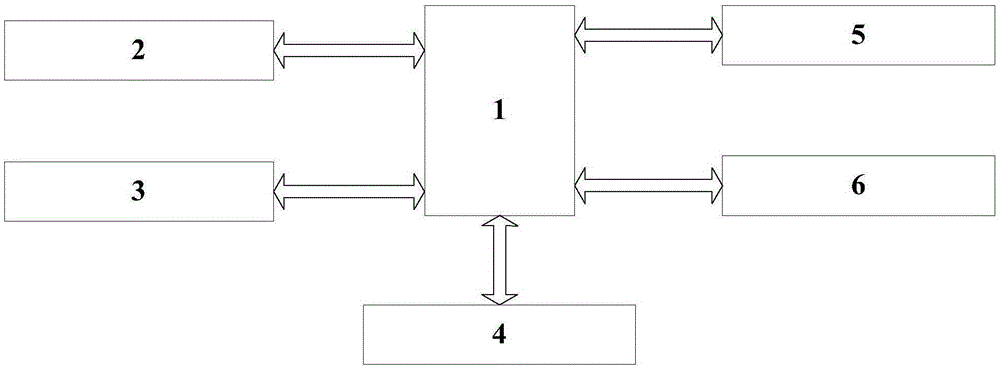
[0027] The embodiment of the present invention provides a mail encryption system based on a domestic commercial cryptographic chip, see figure 1 , the mail encryption system includes: a system control module 1, a user data input module 2, a mail content display module 3, a data encryption and decryption module 4, a key management module 5 and a mail server configuration module 6.
[0028] System control module 1 realizes data communication with user data input module 2; System control module 1 realizes data communication with mail content display module 3; System control module 1 realizes data communication with data encryption and decryption module 4 through a general interface; System control module 1 and The key management module 5 realizes data communication; the system control module 1 and the mail server configuration module 6 realize data communication.
[0029] When sending an encrypted mail, the system control module 1 realizes the input of the mail content by the use...
Embodiment 2
[0038] The embodiment of the present invention provides an implementation method of a mail encryption system based on a domestic commercial cryptographic chip, see the following description for details:
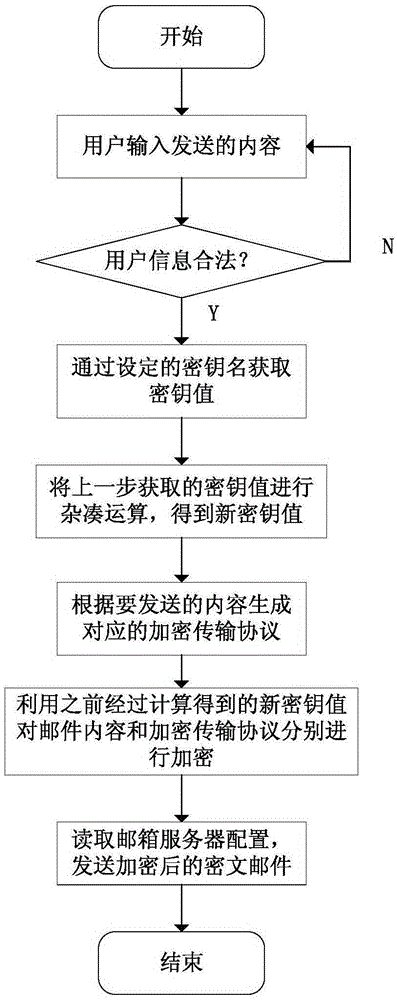
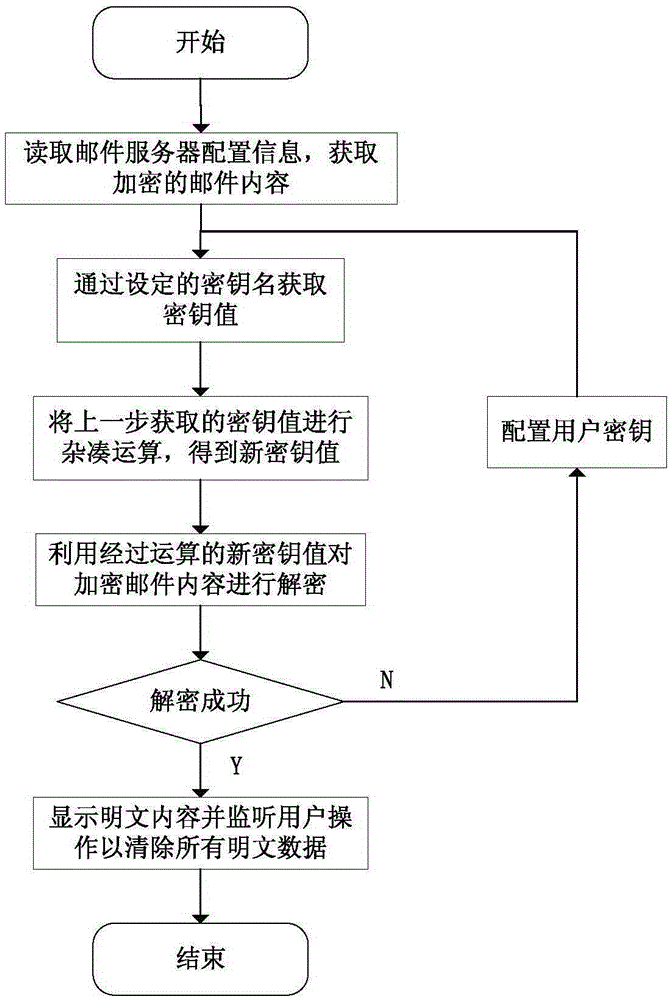
[0039] see figure 1 and figure 2 , the process of sending the encrypted mail of the mail encryption system in the present invention is:
[0040] System control module 1 realizes the input of mail content by user data input module 2, and wherein user data input module 2 determines the legitimacy of user data, and system control module 1 obtains by calling key management module 5 to encrypt according to the encrypted key name of input. key, the system control module 1 transmits the content of the email to be sent and the key to the data encryption and decryption module 4, and the data encryption and decryption module 4 performs calculations on the key through the SM3 algorithm, and the data encryption and decryption module 4 generates a corresponding encrypted transmission p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com