Sensor characteristic sub-area modeling-based monitor method for user identity of touch screen equipment
A device user and sensor technology, applied in instruments, digital data authentication, electrical digital data processing, etc., can solve the problems of forgetting passwords, finger movement guessing attacks, easy to be stolen, etc., to improve robustness and fault tolerance, The effect of increasing practicality and ensuring stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
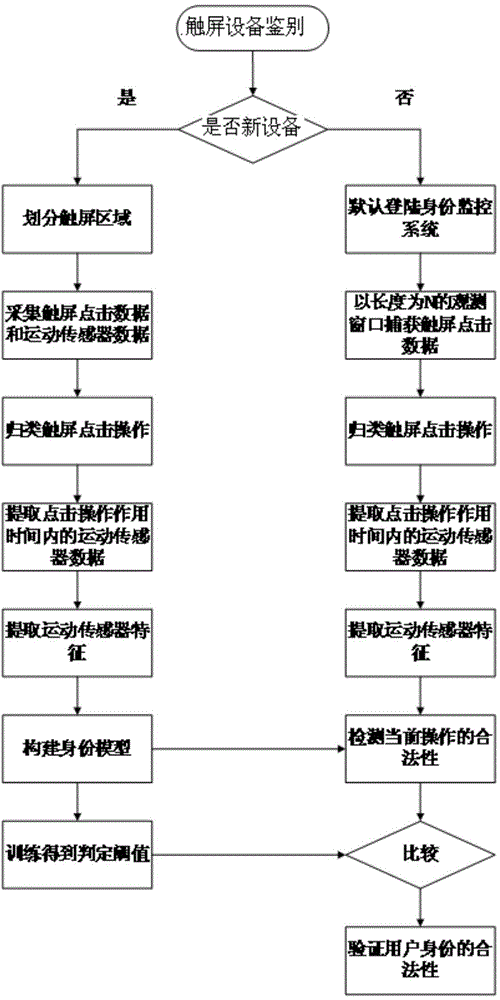
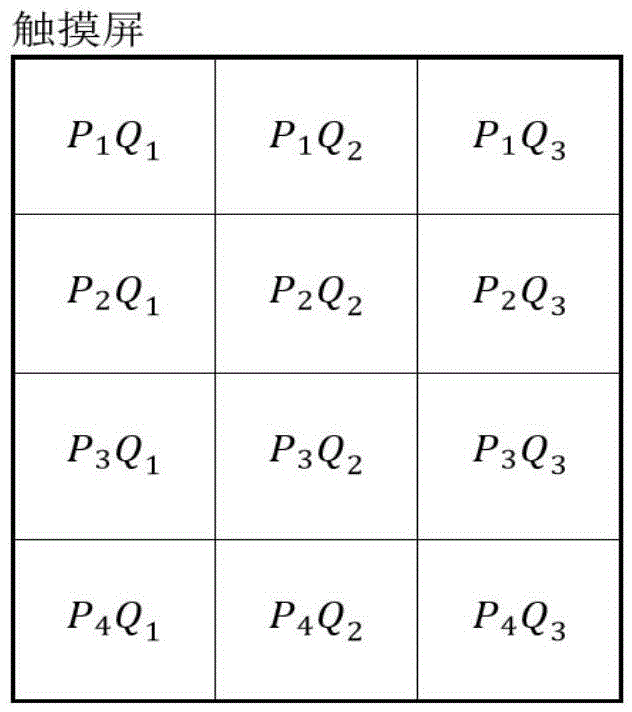
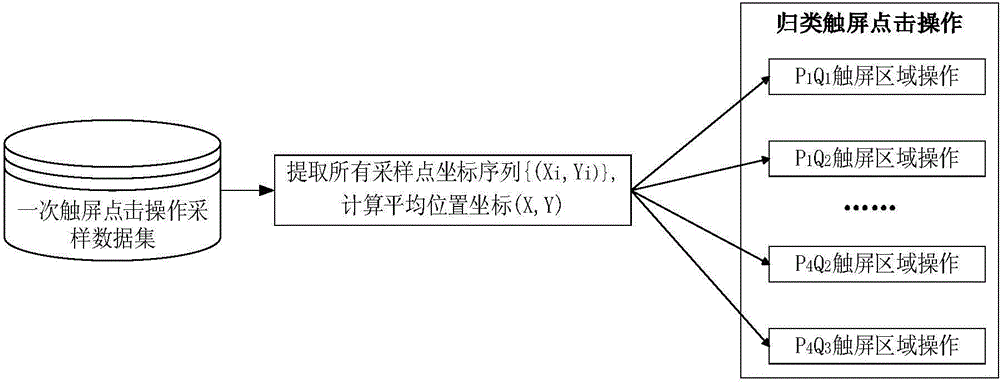
[0035] see figure 1 , the present invention proposes a touch-screen device user identity monitoring method based on sensor feature sub-area modeling, which can be used to judge the identity legitimacy of the touch-screen device user in real time, and then protect the sensitive information stored inside the touch-screen device. Concrete implementation steps of the present invention are as follows:
[0036] (1) When a touch screen device is used, the identity monitoring system judges whether the touch screen device is a new device; if it is a new device, enter step (2) to build an identity monitoring model; if the touch screen device is a used device, enter Step (3) Turn on the identity monitoring mode; for example, select a touch-screen smart phone as an experimental machine, and the software implemented by this method is embedded in the mobile phone system. When the mobile phone is turned on and the screen is lit, first read the system activation information. If If the mobile...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com