Compressed file data embedding method and device capable of resisting longest matching detection
A technology for longest matching and compressing files, which is applied in the field of data security, and can solve problems such as data embedding security risks, breaking algorithm matching rules, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
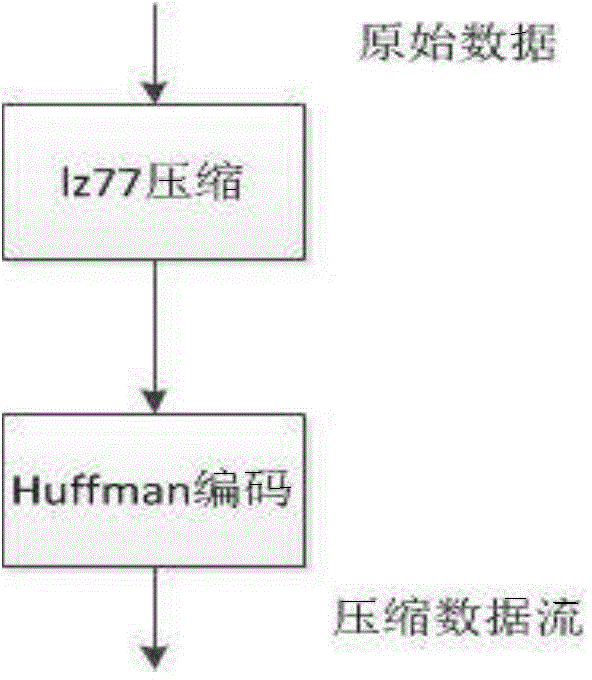
[0060] In this embodiment, the zlib compression and decompression library supporting the deflate algorithm is used to complete the data embedding of the deflate algorithm in the fast mode. zlib is a function library for data compression, developed by Jean-loup Gailly and Mark Adler, the first version 0.9 was published on May 1, 1995. zlib uses the abstract DEFLATE algorithm, which was originally written for the libpng library, and later it is generally used by many software. This library is free software, licensed with zlib. As of March 2007, zlib is an open source project included in Coverity's US Department of Homeland Security sponsor that has chosen to continue review. In this embodiment, version 1.2.8 of zlib is used as the instance object. The concrete steps of embodiment are as follows:
[0061] A. Obtain the zlib 1.2.8 source code
[0062] The source code for version 1.2.8 of zlib can be downloaded from the zlib Home Site (http: / / www.zlib.net / ). This embodiment us...
Embodiment 2
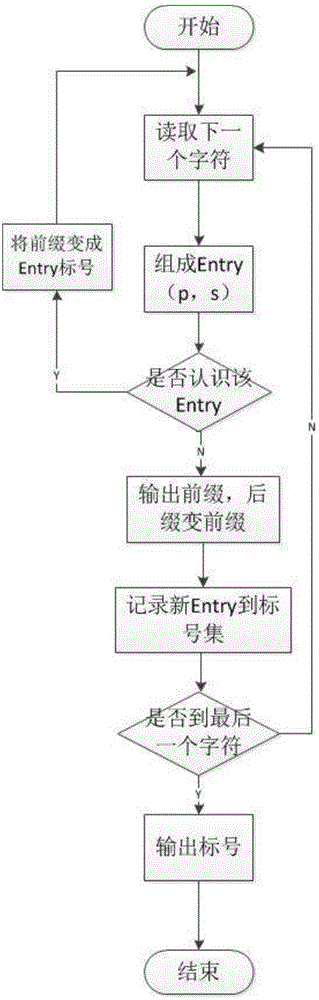
[0104] Such as Figure 4 Shown is a compressed file data embedding device resistant to longest matching detection, including an embedded data acquisition unit, a file data acquisition unit to be compressed, a linked list processing unit, a longest matching length calculation unit, and a longest matching length output unit; the file data to be compressed The acquisition unit is connected to the linked list processing unit, the linked list processing unit and the embedded data acquisition unit are respectively connected to the longest matching length calculation unit, and the longest matching length calculation unit is connected to the longest matching length output unit;
[0105] Embedded data acquisition unit: acquire the embedded data, convert the embedded data into a binary bit sequence and store it in the bitBuf array, define the bitBuf array as a global array, and directly access the bitBuf data during data embedding to obtain the data to be embedded;
[0106] Data acquisi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com