Dynamic detection method of Shellcode
A dynamic detection and to-be-detected technology, applied in the field of information security, can solve problems such as easy to be found, and achieve the effect of reducing possibility and easy deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
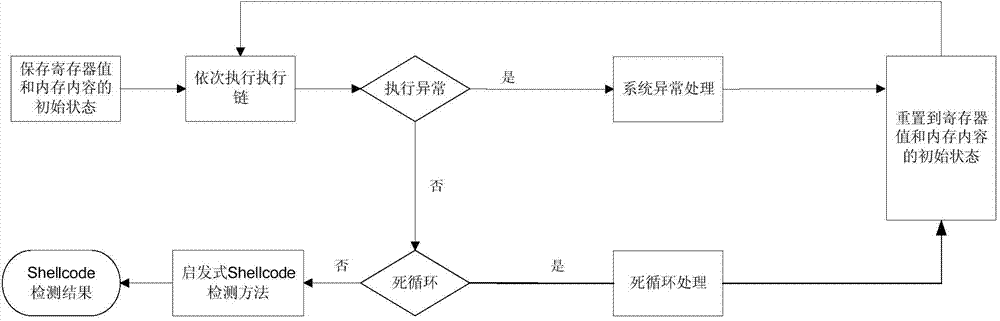
[0020] The invention proposes a dynamic detection method of Shellcode, without using any virtualization technology, so that the network data flow can be directly executed on the CPU, and the Shellcode can be effectively detected. The method of the present invention directly makes the network data flow execute on the CPU, and the general network data flow is mostly invalid or illegal instructions for the CPU, and directly executing it on the CPU will cause the operating system currently used to be abnormal or fall into an endless loop. Execution to Shellcode will not cause operating system exceptions. Therefore, in order to enable the network data flow to be executed smoothly and continuously, it is necessary to deal with the operating system exception and the system falling into an infinite loop.
[0021] To judge whether the execution chain is in an endless loop state, the core idea is to check the counter variables of the current operating system, and check the difference be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com