Software authorization and protection device and method based on asymmetric encryption algorithm
An asymmetric encryption, software authorization technology, applied in computer security devices, digital data protection, program/content distribution protection, etc., can solve the problems of weak protection, easy to crack, low database security, etc., to reduce costs and security. high sex effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be further described in conjunction with the accompanying drawings and specific embodiments.
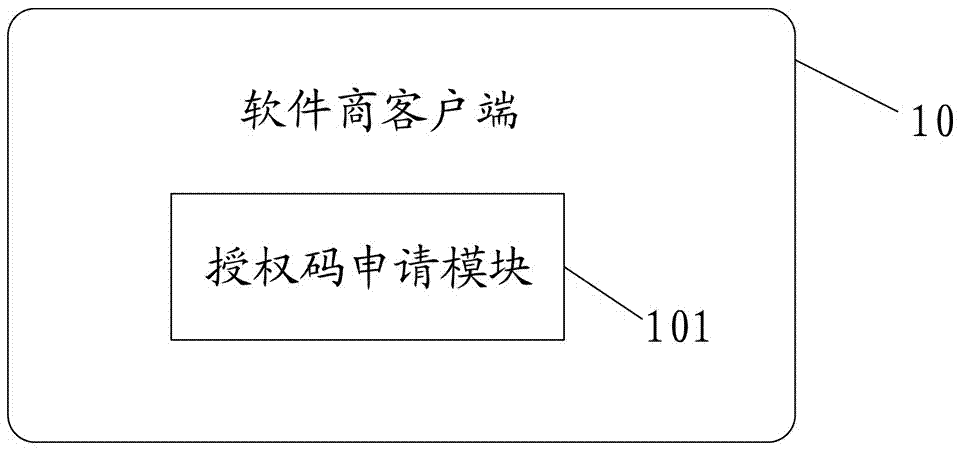
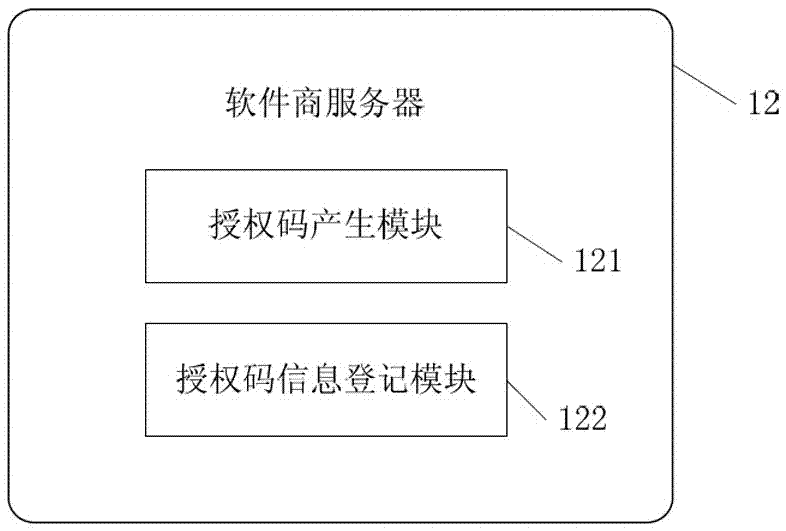
[0041] As a specific example, such as figure 1 As shown, a software authorization and protection device based on an asymmetric encryption algorithm of the present invention includes a software vendor client, multiple user clients, a software vendor server, a database, and a user server. The business client is connected to the software business server through a wireless and / or wired network, the software business server is connected to the database through the internal security network of the first local area network, the user server is connected to the database through the internal security network of the second local area network, and the plurality of users The client connects to the user server through the Internet,
[0042] The software vendor client includes an authorization code application module, which applies for an authorization code from t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com