LDDoS attack detection method based on chaotic Dufing oscillators
An attack detection and vibrator technology, applied in digital transmission systems, electrical components, transmission systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
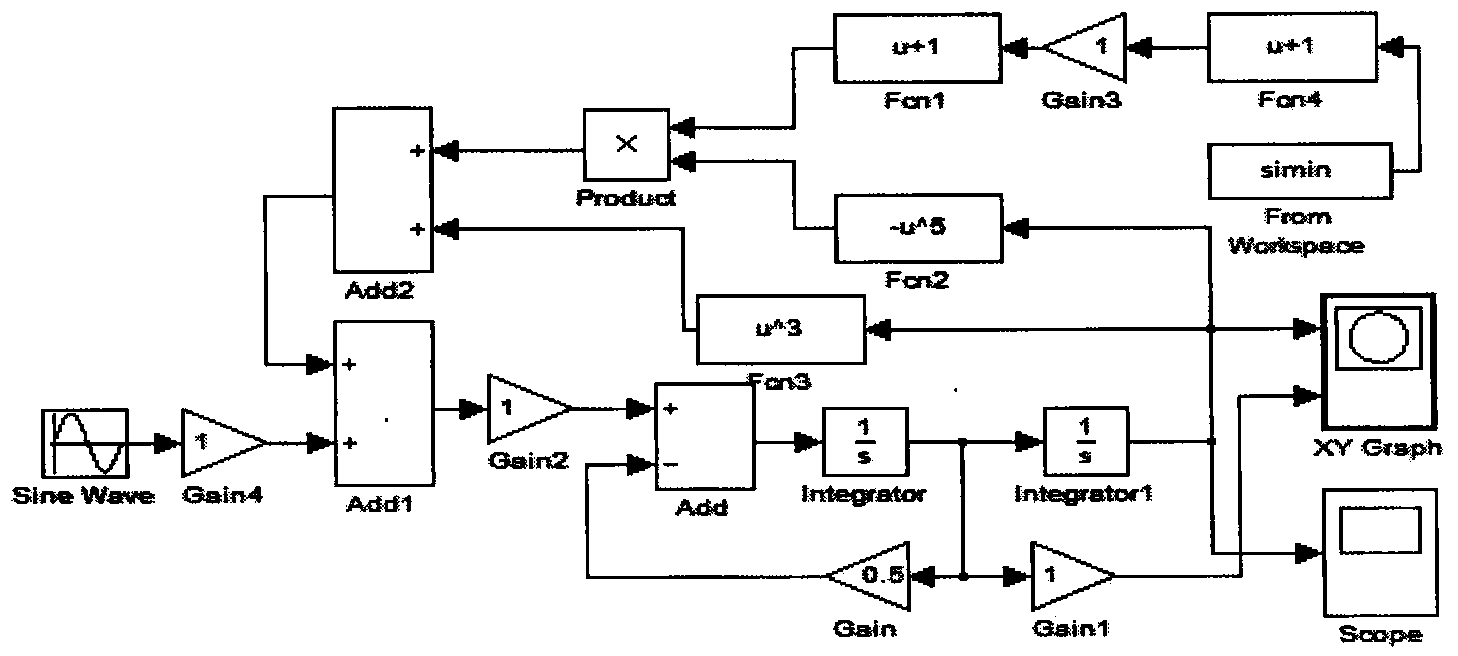
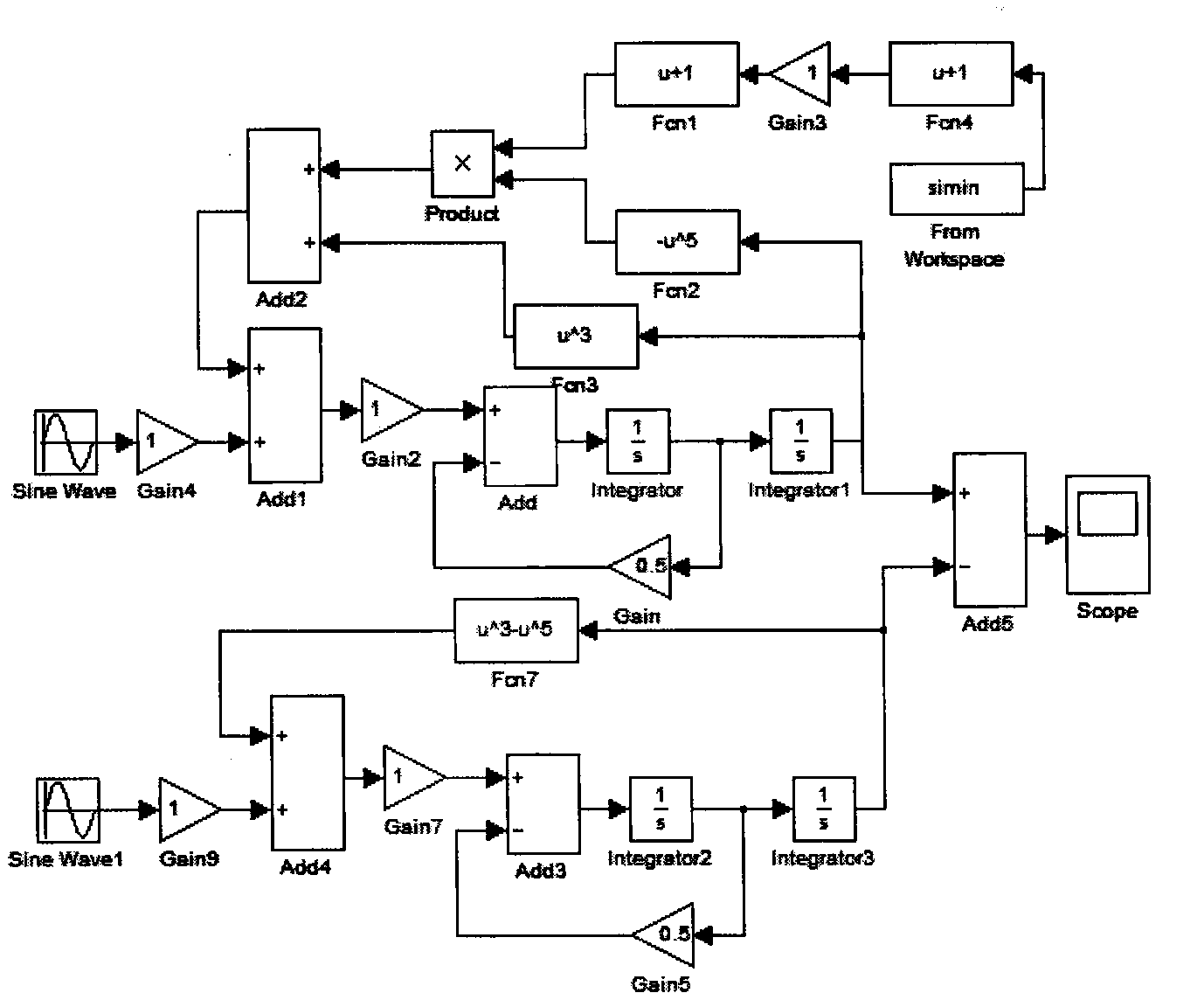
Embodiment Construction
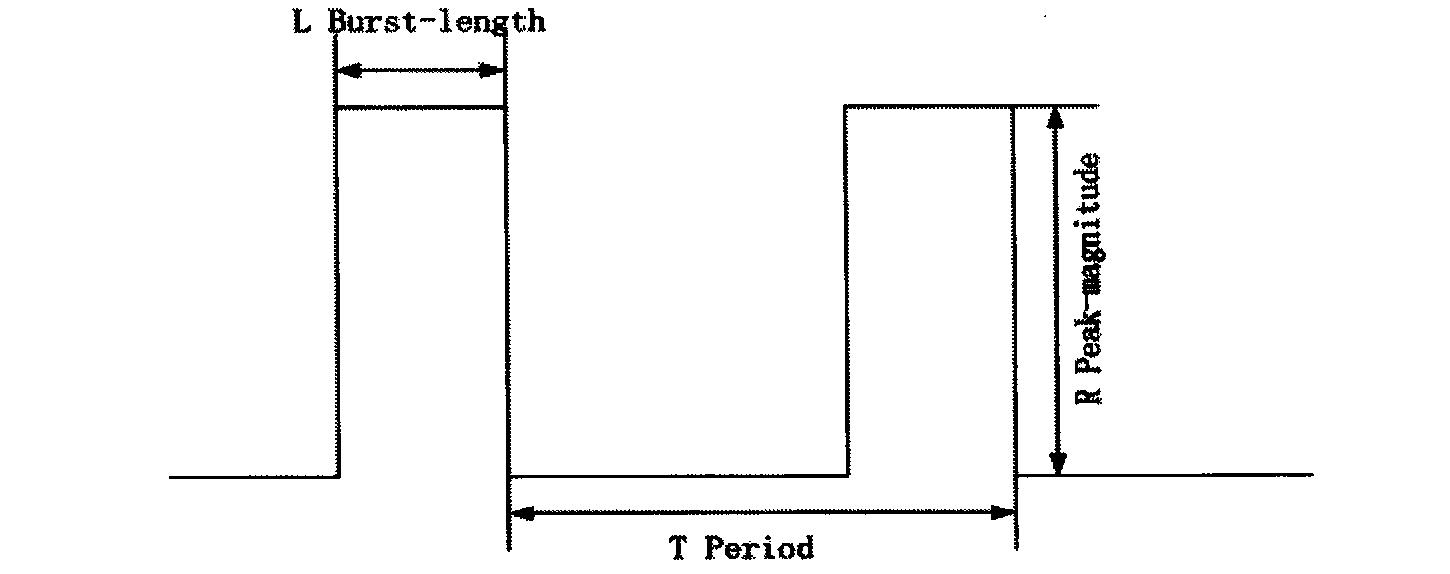
[0014] 1. The simulation scene used is as attached Figure 4 As shown, a dumbbell-shaped network topology is used. In the simulation environment, five normal sending nodes (2-6) are set up, black nodes 9 and 10 represent two attack sources, nodes 7 and 8 are TCP and UDP servers respectively, and two routers are represented by nodes 0 and 1 respectively. FTP transmission is enabled between the normal node and node 7 (TCP server), UDP attack traffic is transmitted between the attack source node and node 8 (UDP server), and the one-way delay of all links including the bottleneck link is 10 milliseconds . The congestion control protocol used by TCP normal nodes is TCP Reno. The detection node is located at the front end of router 1, and the sampling interval is 10 milliseconds.
[0015] The system starts at 0 seconds and ends at 121 seconds. Normal TCP traffic starts at some random time after 1 second and ends at 121 seconds; attack traffic (UDP) comes later at 20 seconds and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com