Virtualization based power and function isolating method for loading module of monolithic kernel operation system
An operating system and core module technology, applied in the field of computer security, can solve the problems of large losses, dilemmas, and low monitoring accuracy of the client system, and achieve the effect of avoiding frequent intervention, avoiding page table switching, and improving overall performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described below in conjunction with the examples, but not as a limitation of the present invention.
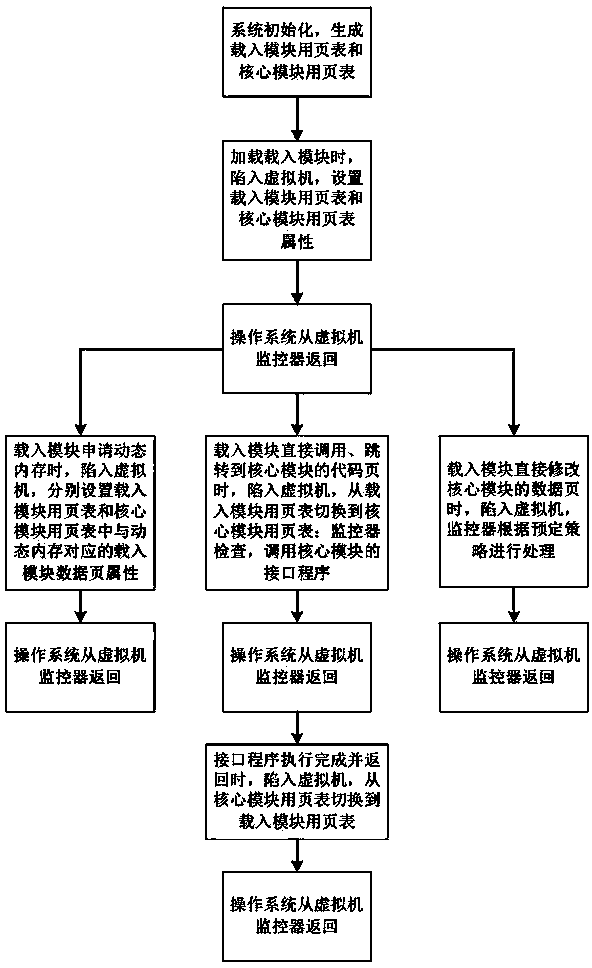
[0024] According to the virtualization-based macrokernel operating system loading module power isolation method proposed by the present invention, the scenarios where the macrokernel is attacked include: 1) the attacker obtains superuser authority, and then loads malicious programs into the kernel space of the operating system; 2) Attackers use existing system vulnerabilities to load malicious software such as Rootkit; 3) Careless users load unauthenticated load modules containing malicious codes, etc.
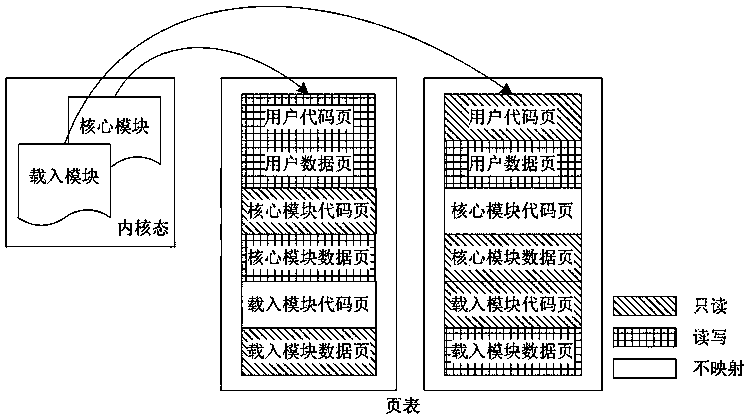
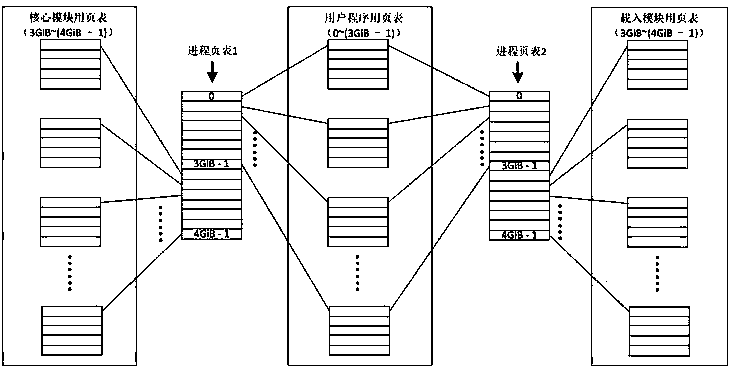
[0025] In the macrokernel operating system, the load module is in the same address space as the kernel during operation, and can see all memory views of each other. The virtualization-based macrokernel operating system loading module power isolation method proposed by the present invention, compared with the attached figure 1 , to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com