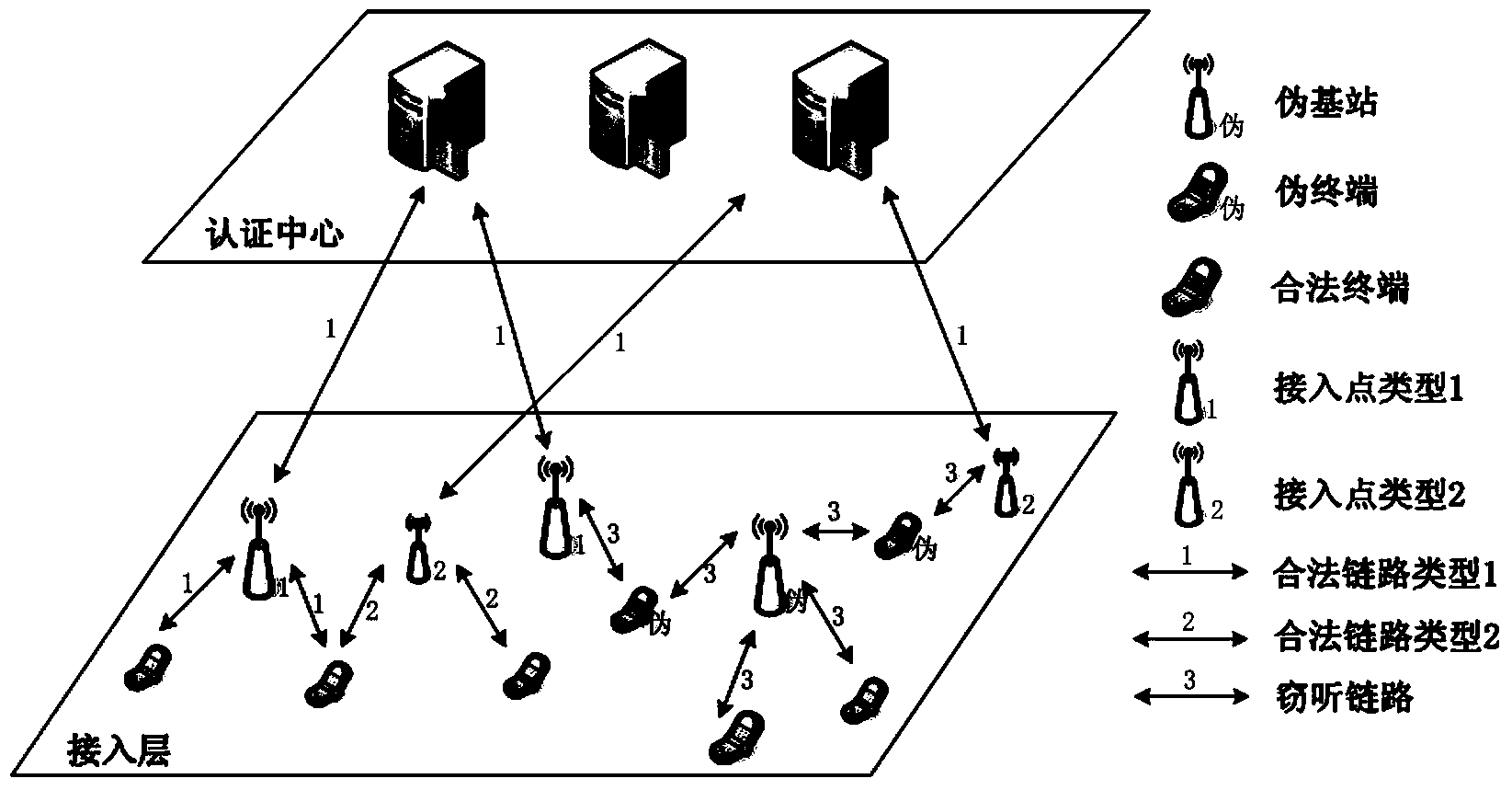
Heterogeneous network unified authentication method based on physical layer safety
A physical layer security, heterogeneous network technology, applied in the field of unified authentication of heterogeneous networks, can solve problems such as different security protection capabilities and inability to implement attack methods, achieve strong practical value, and ensure the effect of communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
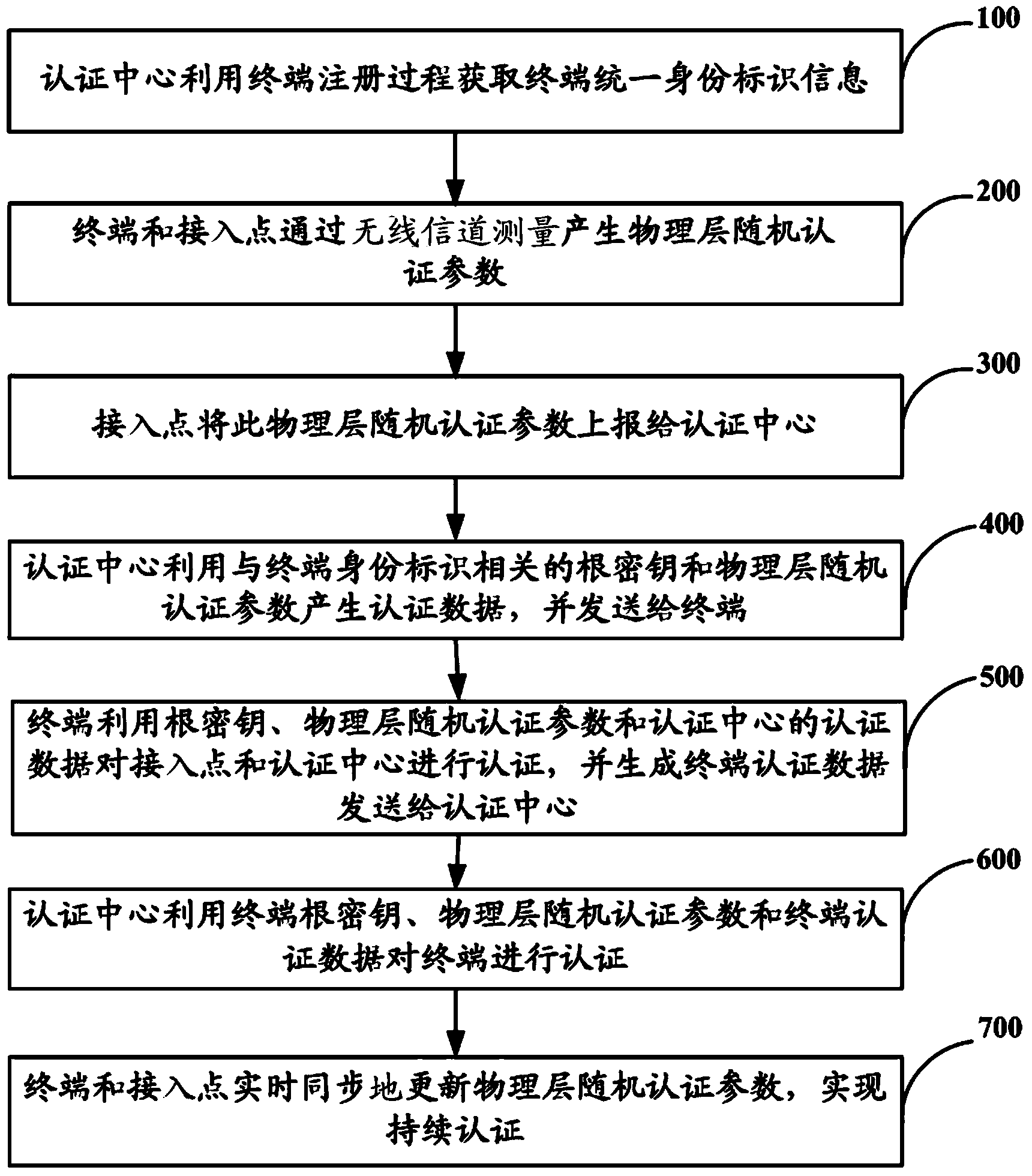
[0047] Embodiment one: if figure 1 and Image 6 As shown, a unified authentication method for heterogeneous networks based on physical layer security includes the following steps:
[0048] Step 100: the authentication center obtains terminal unified identity information through the terminal registration process;
[0049] Step 200: the terminal and the access point generate physical layer random authentication parameters through wireless channel measurement;
[0050] Step 300: the access point reports the physical layer random authentication parameter to the authentication center;
[0051] Step 400: the authentication center uses the root key related to the terminal identity and the random authentication parameters of the physical layer to generate authentication data and send it to the terminal;
[0052] Step 500: The terminal authenticates the access point and the authentication center by using the root key, the physical layer random authentication parameters, and the auth...
Embodiment 2
[0055] Embodiment 2: As a preference, on the basis of Embodiment 1, the above-mentioned unified authentication method for heterogeneous networks based on physical layer security, wherein in step 100, the specific steps for the authentication center to use the terminal registration process to obtain the unified identity information of the terminal are as follows: :
[0056] Step A1: Various terminals use a unified compilation method to identify identity information in the heterogeneous converged network, and the same user uses the same identity indicator in different networks;
[0057] Step A2: The terminal uses the unified identity information to initiate a registration request to the access point, and the access point forwards the identity to the authentication center;
[0058]Step A3: The authentication center obtains the terminal root key K bound to the terminal identity by using the unified identity reported by the terminal.
[0059] In step 200, the specific steps for th...
Embodiment 3
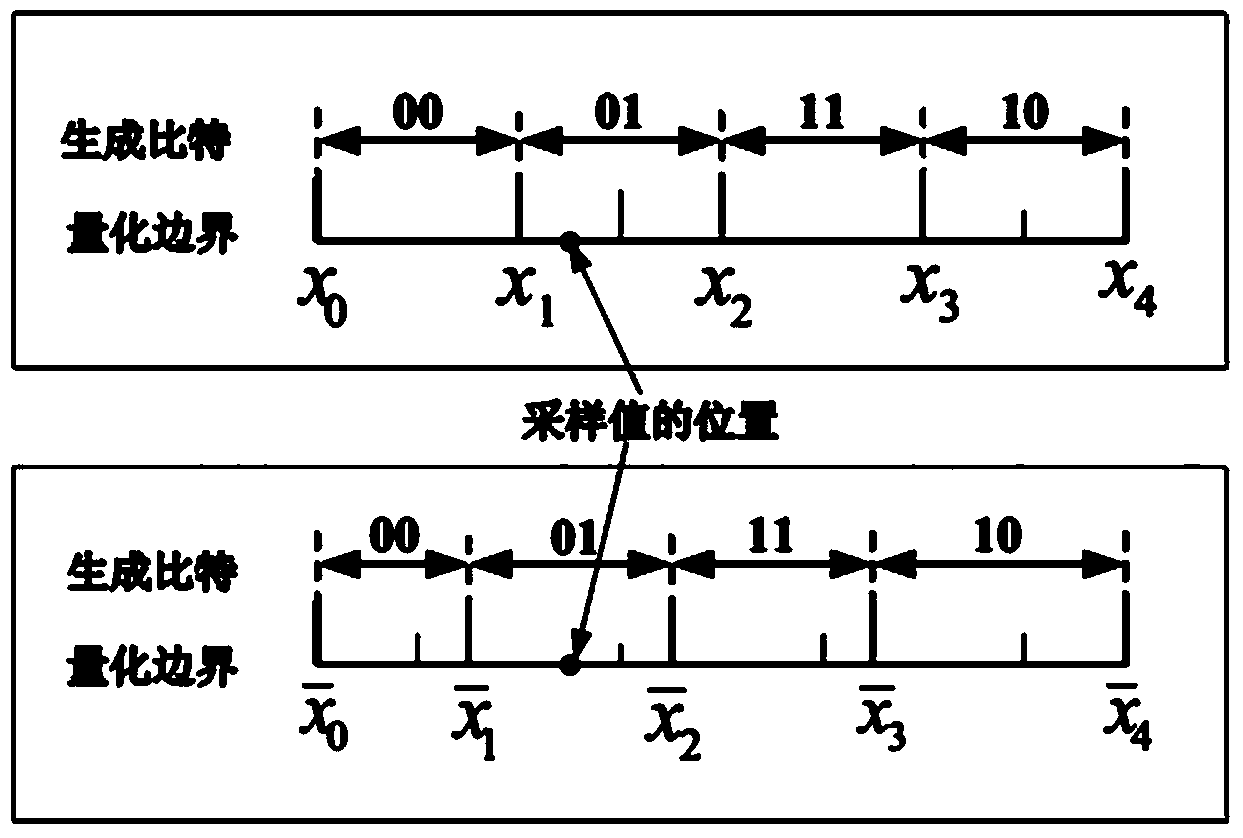
[0071] Embodiment 3: On the basis of Embodiment 2, the above-mentioned unified authentication method for a heterogeneous network based on physical layer security, wherein in step 400, the authentication center forwards the generated authentication data to the terminal through the access point, specifically: authentication After the center receives the authentication data request message, such as Figure 5 As shown, the root key K and the physical layer random authentication parameter Ka reported by the access point are used to generate the authentication data AV, and the AV is sent to the terminal through the user authentication request message.
[0072] In step 500, the specific steps for the terminal to authenticate the access point and the authentication center are:
[0073] Step E1: The terminal uses the terminal root key and random physical layer authentication parameters to generate local authentication data;
[0074] Step E2: The terminal compares the local authenticat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com