A security monitoring method in a distributed network environment
A distributed network and security monitoring technology, applied in the field of information security, can solve problems such as relatively weak security in the physical environment, data security risks, and hidden dangers in the virtualized environment, and achieve the effect of solving real-time security problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] Attached below figure 1 and figure 2 The present invention is described in further detail.
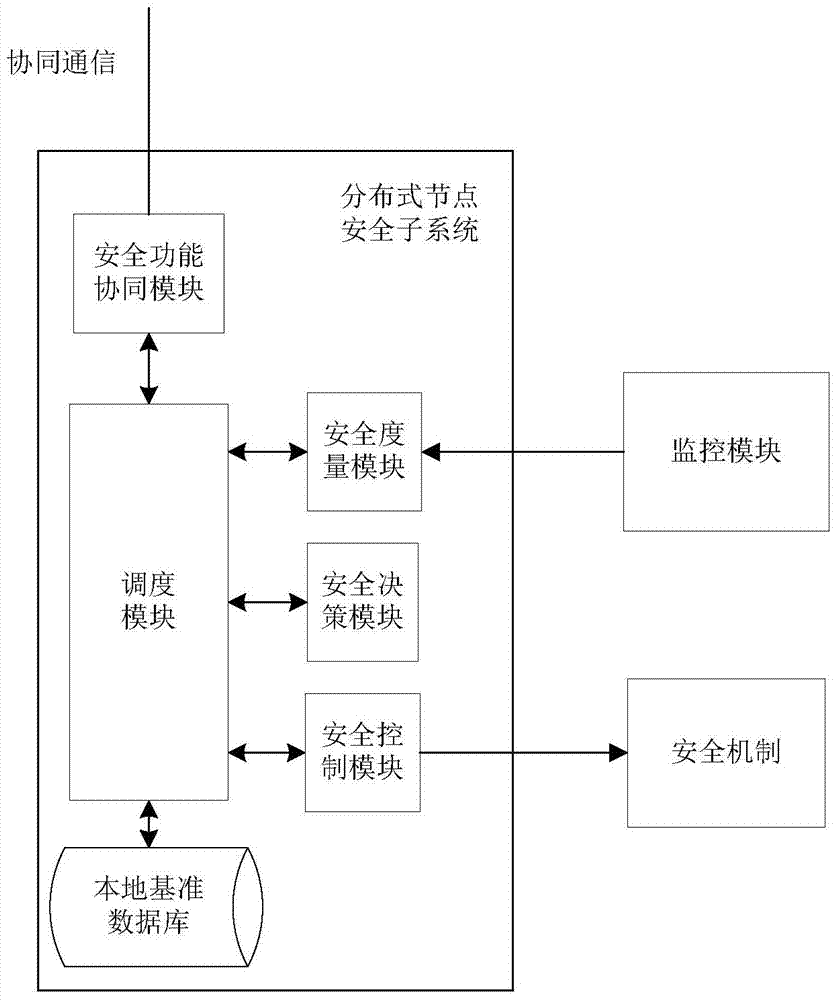
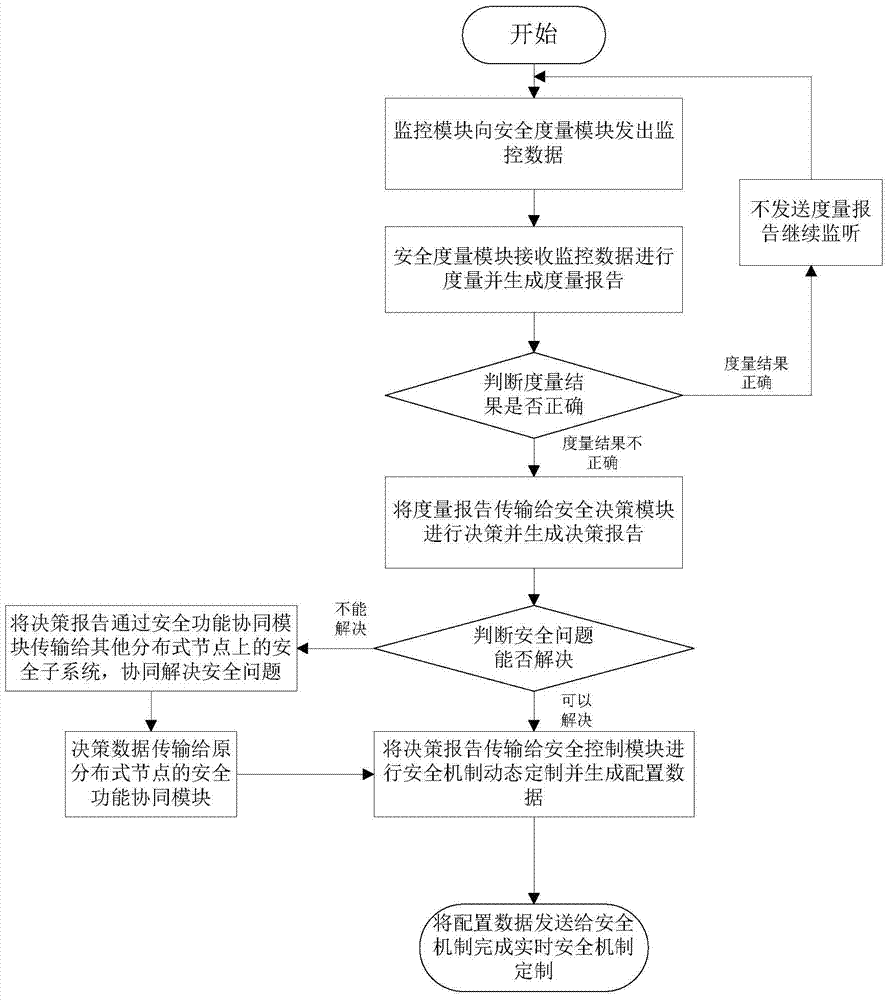
[0034] The present invention proposes a security monitoring method in a network environment, each distributed node is set as figure 1 A monitoring module, a distributed security subsystem and a monitoring system composed of local security mechanisms in a distributed environment. Through the collaboration among distributed node security subsystems, the security mechanism can be customized in real time to realize a security monitoring process in a distributed network environment.
[0035] like figure 1 As shown, the security module obtains the monitoring information through the monitoring module, and then sends the security custom policy to the security mechanism after processing, customizes the real-time security mechanism, and solves the real-time security problem. The security subsystem consists of a security function coordination module, a scheduling module, a security me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com