Kernel integrity detection method based on Xen virtualization
An integrity detection and virtualization technology, applied in platform integrity maintenance, software simulation/interpretation/simulation, memory address/allocation/relocation, etc., can solve the problem that security software does not have privileged advantages, and achieve the goal of ensuring security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below in conjunction with the accompanying drawings.
[0037] 1. Overall structure design
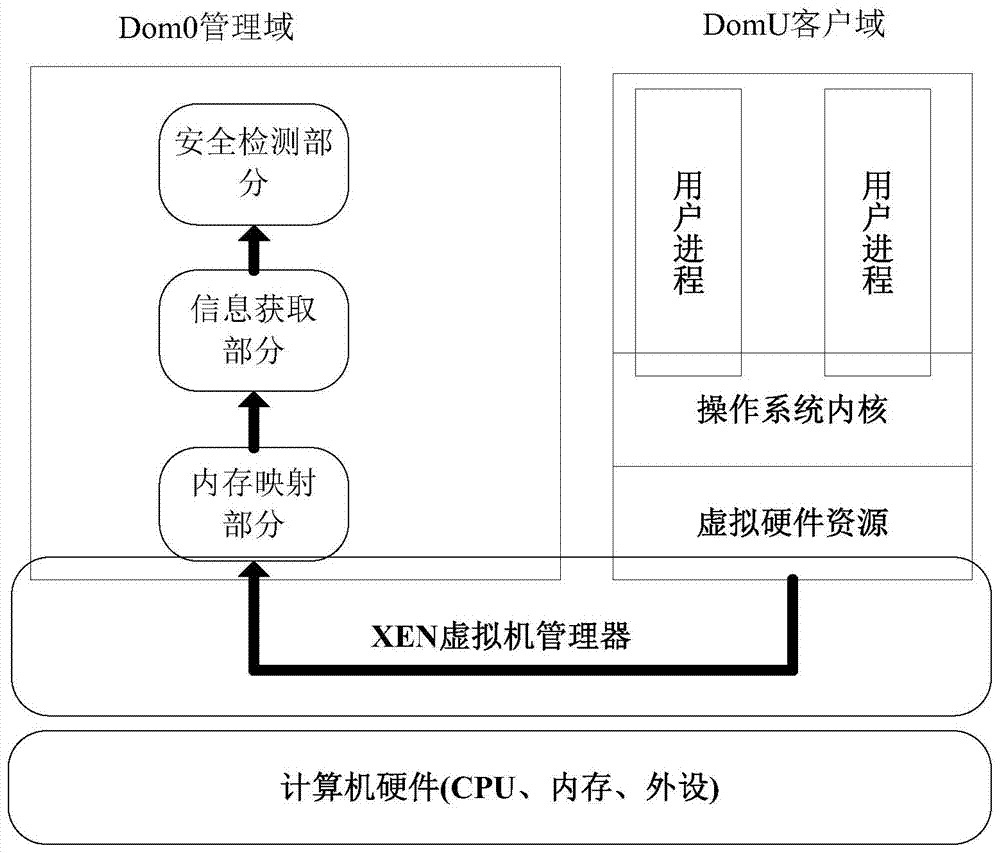
[0038] The kernel integrity detection system based on Xen virtualization consists of three basic parts, which are memory mapping part, information acquisition part and security detection part. The system of the present invention is deployed in the management domain Dom0, effectively utilizes the isolation provided by Xen, and prevents the system of the present invention from being attacked by malicious software in the customer domain DomU. The overall system architecture diagram is as follows figure 1 shown.
[0039] The functions of the above parts are as follows:
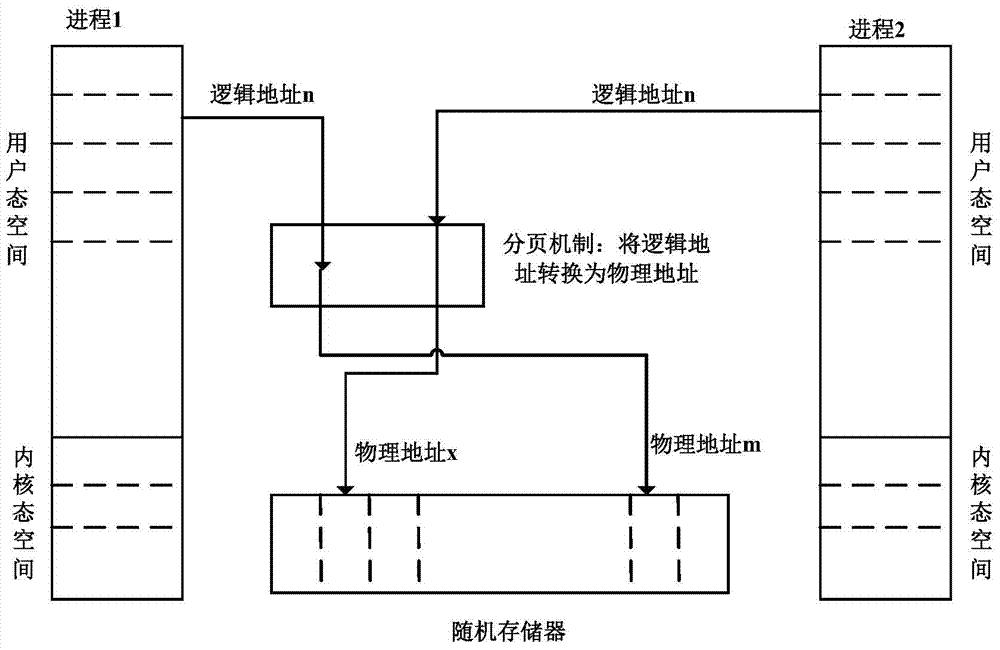
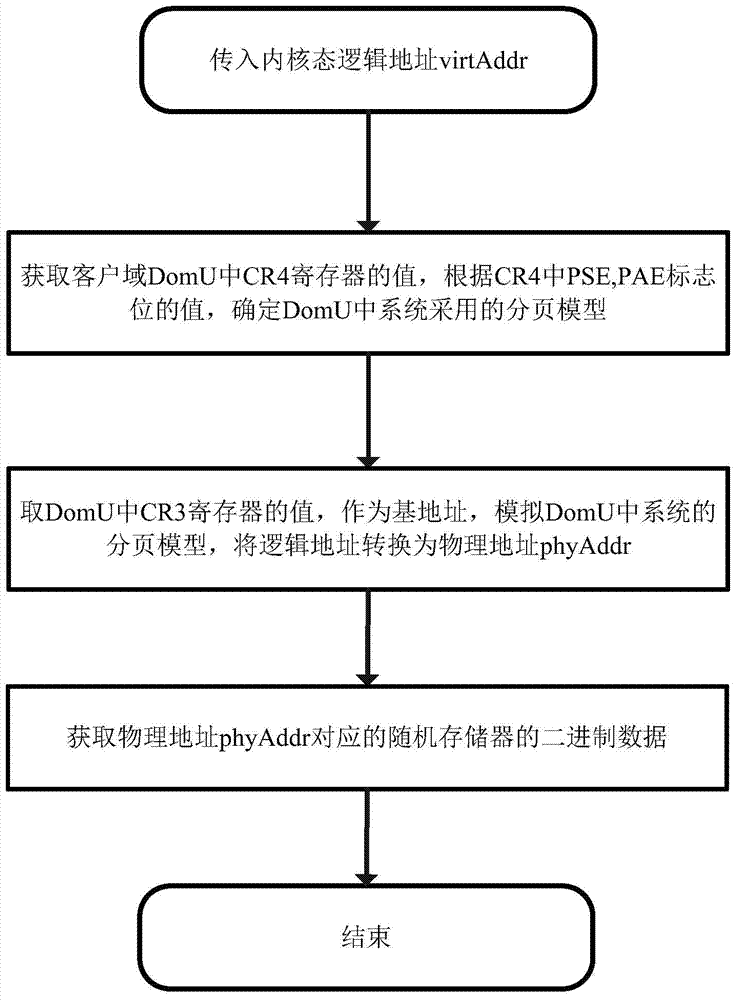
[0040] The memory mapping part simulates the paging mechanism in the customer domain DomU in the management domain Dom0, and provides an interface to obtain the machine byte data at the hardware level in the customer domain DomU, including obtaining the binary data o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com