Authentication methods for common authentication mechanisms
A general authentication mechanism and authentication method technology, applied in the authentication field of the general authentication mechanism, can solve the problem of large network resource occupation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0096] The embodiment of the present invention discloses an authentication method of a general authentication mechanism. In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and examples.
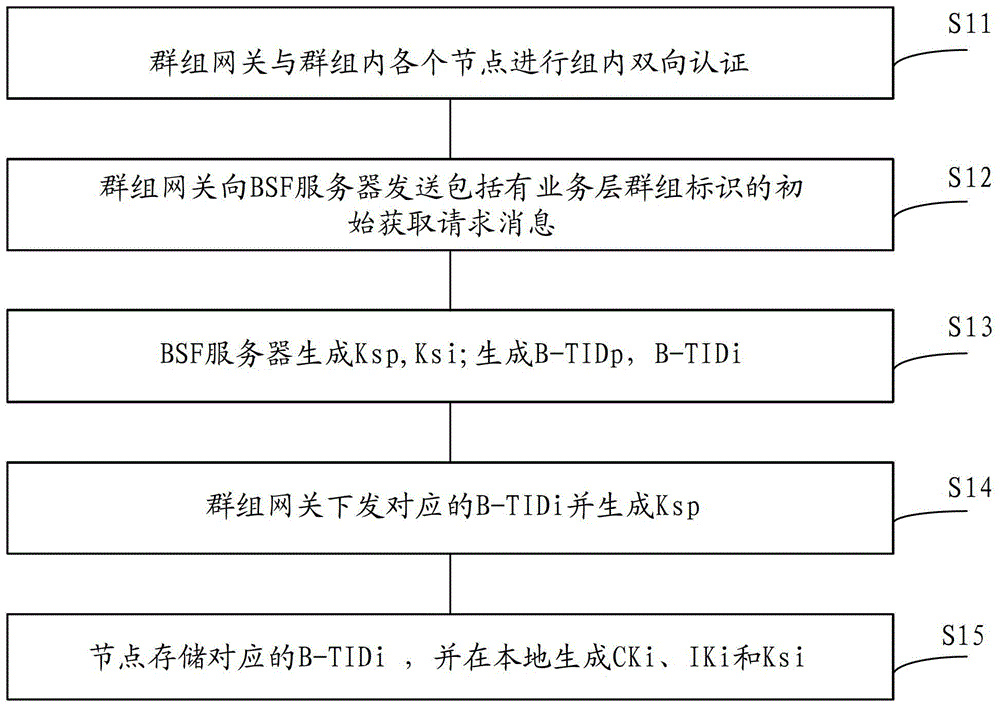
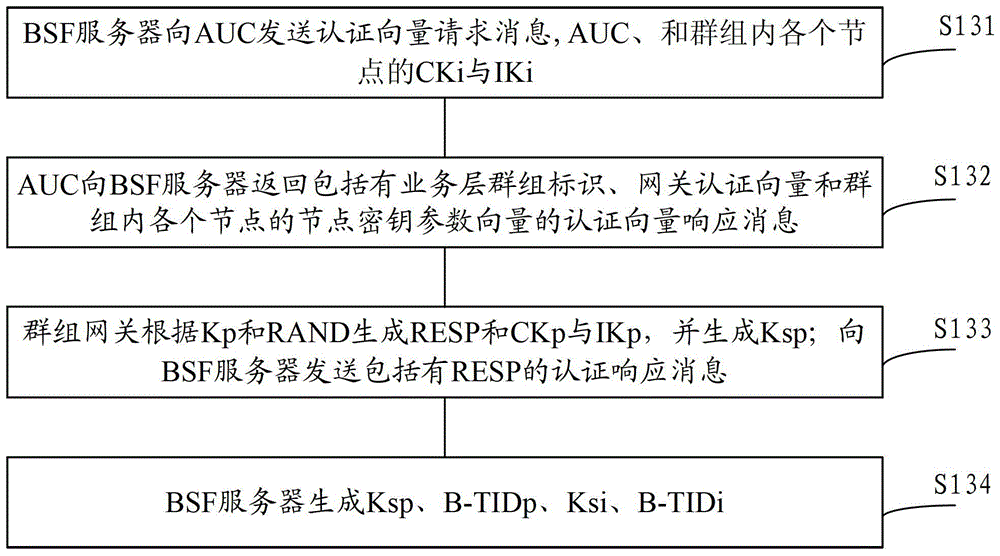
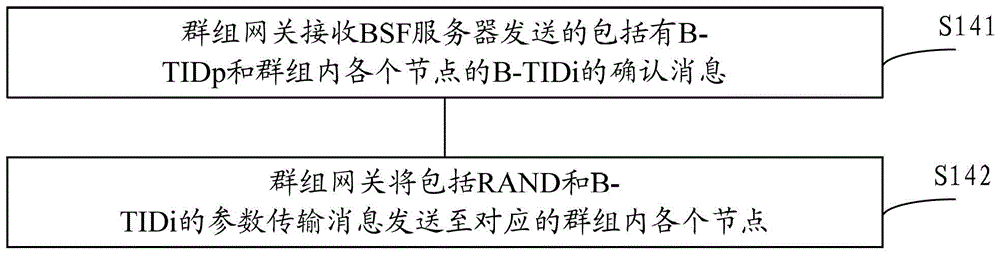
[0097] refer to figure 1 , in the embodiment of the present invention, the GBA-based authentication method, when the general authentication mechanism authentication is initialized, includes the steps:
[0098] S11. The group gateway and each node in the group perform two-way authentication in the group, so that the group gateway and each node in the group mutually recognize the validity of each other's identities;
[0099] One of the application scenarios of the embodiment of the present invention includes smart meter reading applications. Specifically, meters (such as water meters, electricity meters, and gas meters) in the same geographic ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com