Method, device and medium for storing third-party connection information and verifying connection validity
A technology that connects information and is effective. Applied in the computer field, it can solve problems that affect users' experience in using software and reduce interface response speed, so as to achieve the effects of reducing authentication times, improving timeliness, and protecting data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
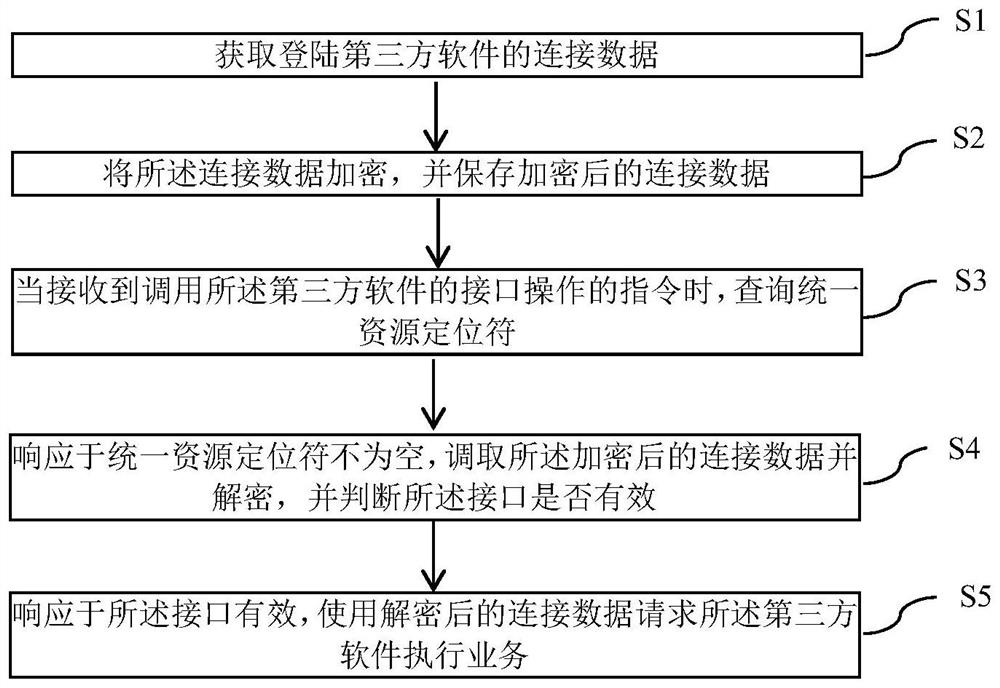
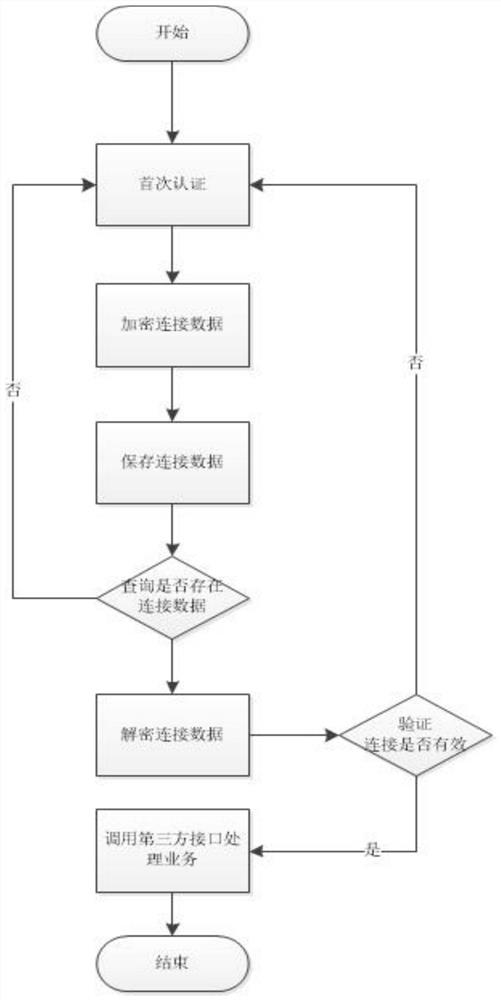
[0048] Below is an example of the method of saving third-party connection information and verifying connection validity, such as figure 1 Looking:
[0049] 1. First certification: Use data from the third-party software environment, log in to user name, password, language as parameters, request a third-party software login authentication interface to get the connection data after the successful login;
[0050] 2. Encrypted data: Encrypt the above connection data using the agreed public key;
[0051]3. Save the connection: Save the connection data encrypted in step 2 in the form of Key-Value, where Key is the connected URL, Value is encrypted connection data;
[0052] 4. Verify and use the connection: When you need to call a third-party interface query or operation data in the business logic:
[0053] 4.1 First querying the KEY value from the memory is the connection data of the third-party environment URL;
[0054] 4.2 If the result of the query in 4.1 is empty, the first authentic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com