Wireless channel access control method based on virtual token
An access control and wireless channel technology, applied in wireless communication, electrical components, etc., can solve the problems of wireless token ring network performance degradation, poor wireless channel transmission quality, increased token maintenance overhead, etc., to reduce difficulty and loss risk, reduce the number and number of times wireless data frames are sent and received, and improve the effect of token passing failures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
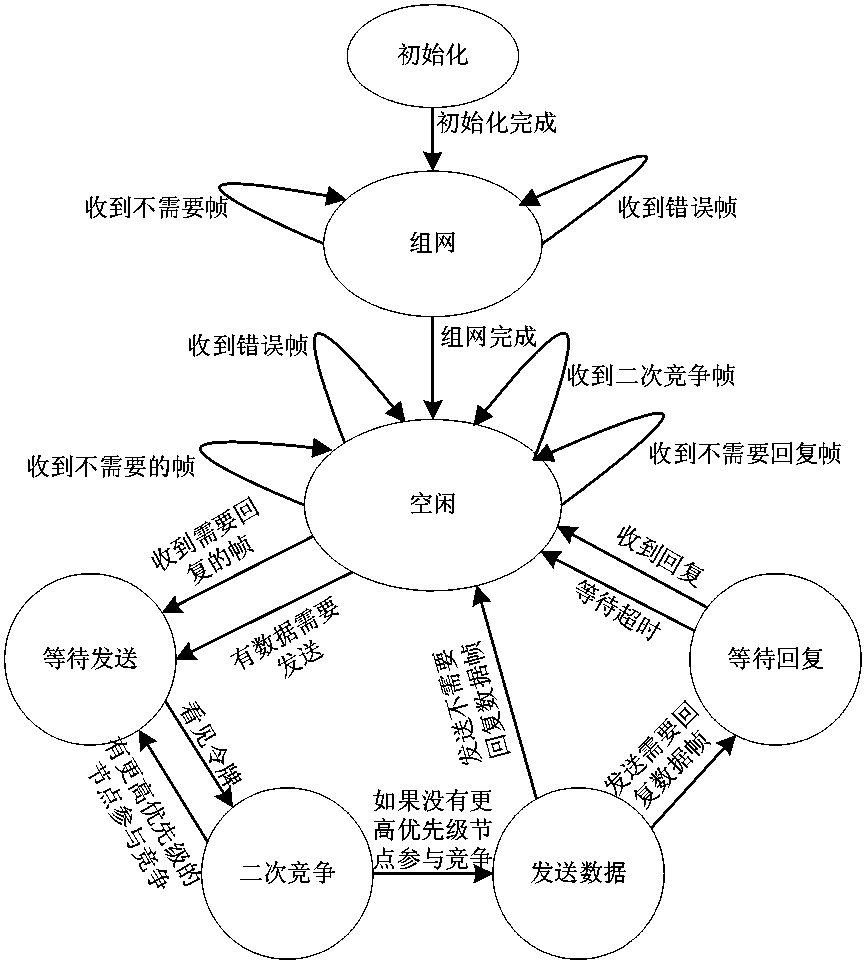
[0039] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
[0040] The wireless channel access control method based on virtual token of the present invention comprises the following steps:
[0041] A. Select several nodes in a certain area, specify the node with the smallest address as the central node (the token is always generated by the central node), and other nodes are called wireless nodes. The addresses of each wireless node are uniformly assigned by the central node in order and Keep the addresses of each wireless node and the central node continuous;
[0042] B. Set the address of the central node to 0, the central node first generates a token, and then broadcasts a data frame to designate a certain wireless node to hold the token and monitor the network;
[0043] C. Within a certain period of time, if the central node can monitor that the wireless node at a certain address is using the token, it mea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com