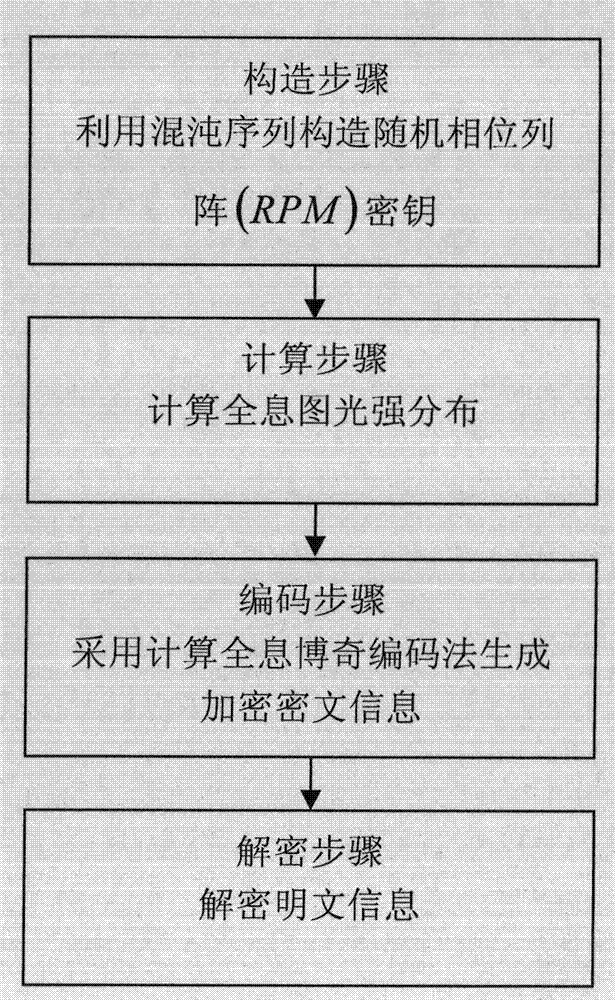
Optical encryption method based on chaos and computer-generated holography
A technology of computational holography and encryption method, applied in the field of information security, can solve the problems of large amount of key data, difficult transmission, difficult Internet real-time transmission and remote display, etc., to achieve high security performance, improve security, and be beneficial to Effects of saving and transferring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] Below in conjunction with accompanying drawing of description and invention is further described:
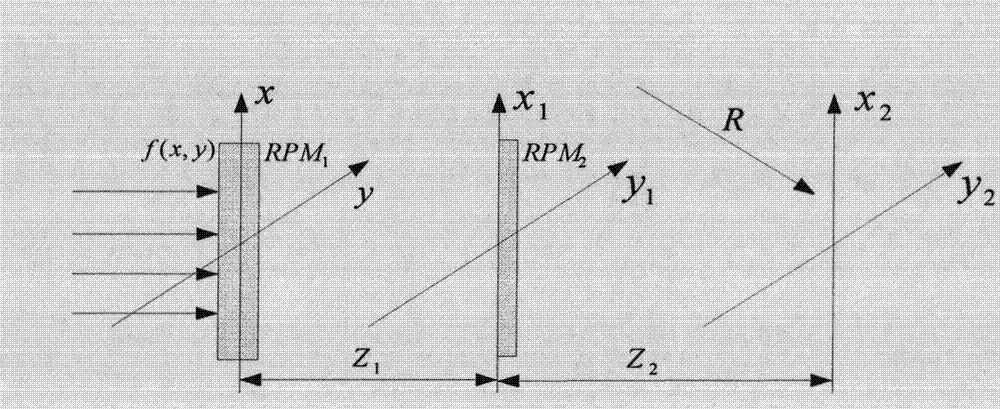
[0042] The schematic diagram of the optical encryption principle of the present invention is as follows figure 1 As shown, the three planes from left to right are the input plane (x, y), the transformation plane (x 1 ,y 1 ) and the output surface (x 2 ,y 2 ). f(x, y) is the plaintext information to be encrypted on the input side, f(x 1 ,y 1 ) is the wavefront distribution of the transformation plane, f(x 2 ,y 2 ) is the wavefront distribution of the output surface, RPM 1 and RPM 2 are two random phase array keys constructed from chaotic sequences, z 1 for RPM 1 distance to the transformation plane, z 2 for RPM 2 Distance to output face. R is the reference light introduced by computational holography.
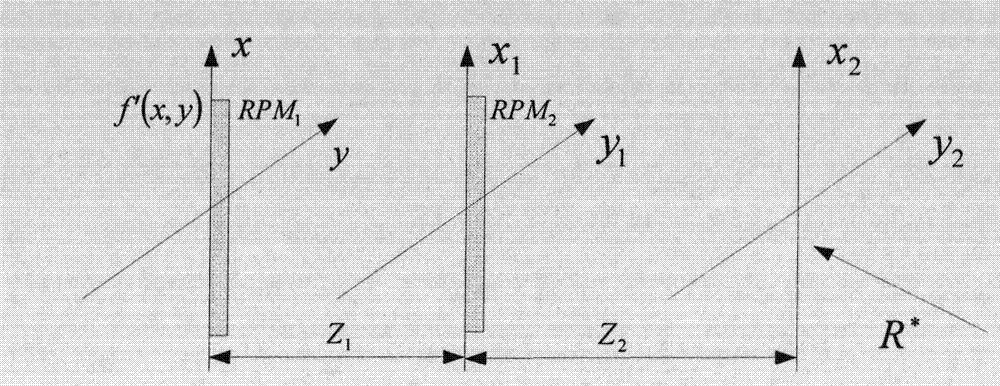
[0043] The schematic diagram of the optical decryption principle of the present invention is as follows: figure 2 As shown, the schematic diagram of the de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com