A cloud computing environment data security storage system and method
A technology for data security storage and cloud computing environment, applied in the field of information security systems, it can solve the problems of protection and the lack of user data, so as to ensure data security, prevent malicious tampering or leakage, and save key generation and management. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be described below in conjunction with the accompanying drawings.
[0037] In the following description, some specific details are provided to provide those skilled in the computer arts with a general understanding of the present invention. In the embodiments, elements for realizing specific functions are shown in the form of schematic diagrams or block diagrams, so as to highlight technical points without obscuring the present invention in unnecessary details. For example, since those of ordinary skill in the art can understand the details disclosed in this field about network communication, electromagnetic signal command technology, user interface or input / output technology, etc., the maximum degree of The above technical details are omitted above, and these details are not considered to be the necessary features to obtain the complete technical solution of the present invention.
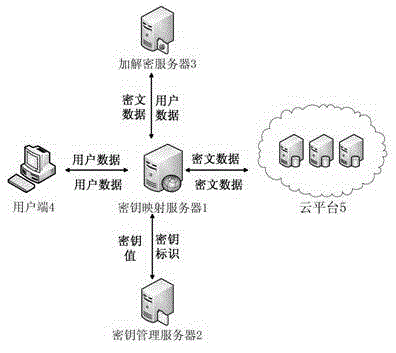
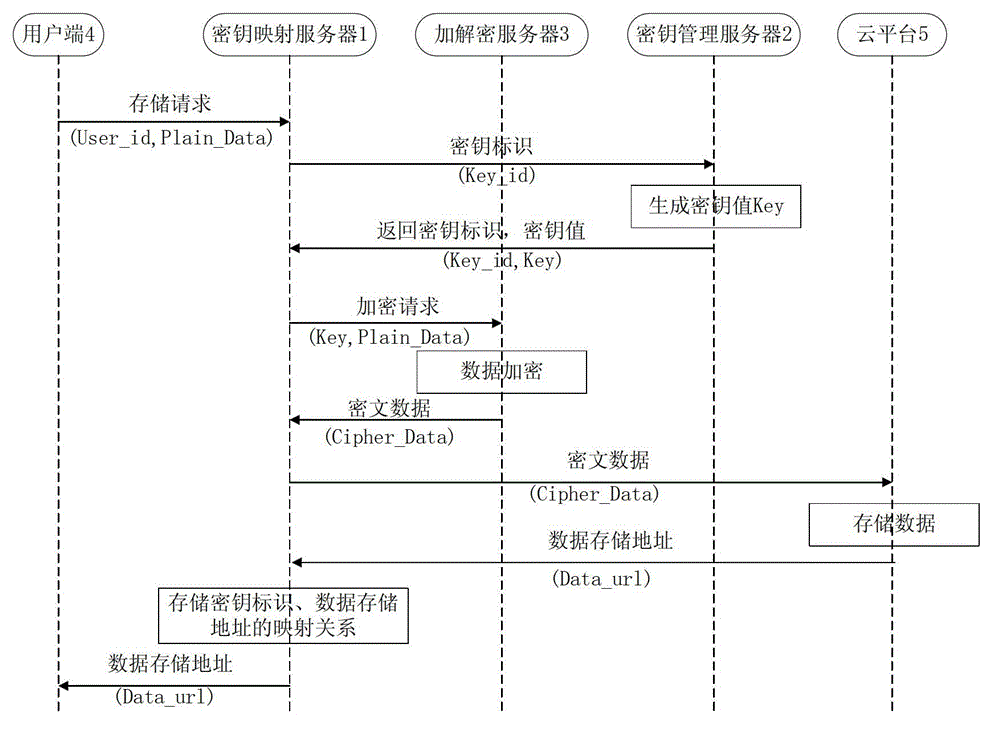
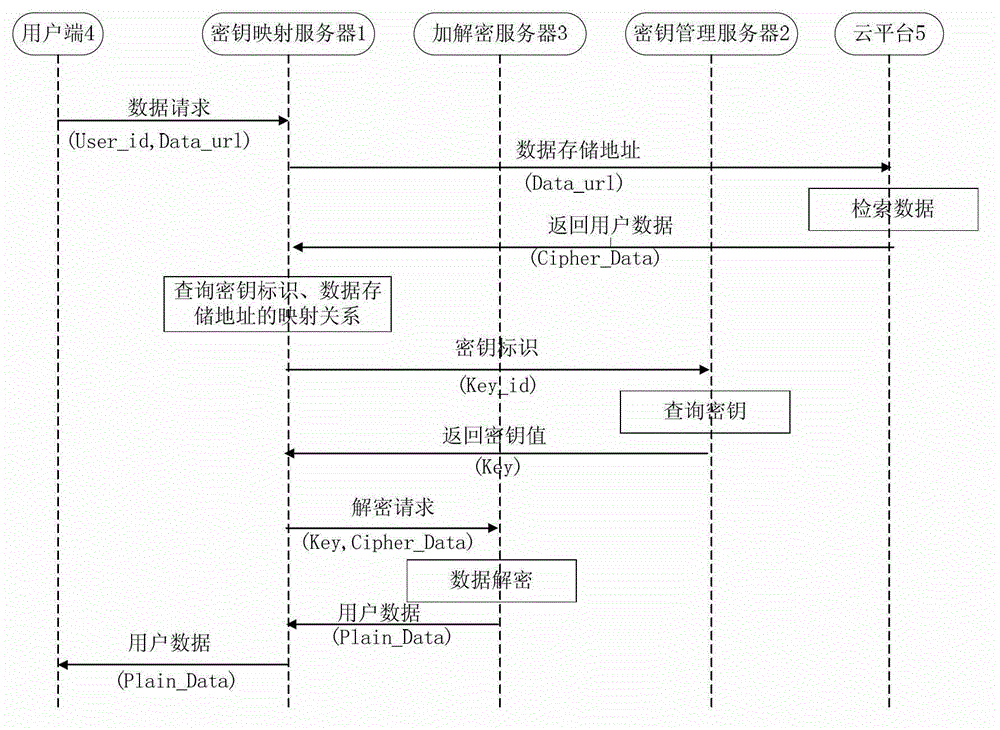
[0038] Such as figure 1 As shown, the cloud computing envi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com