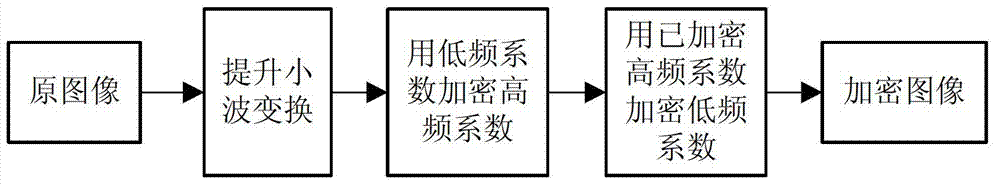
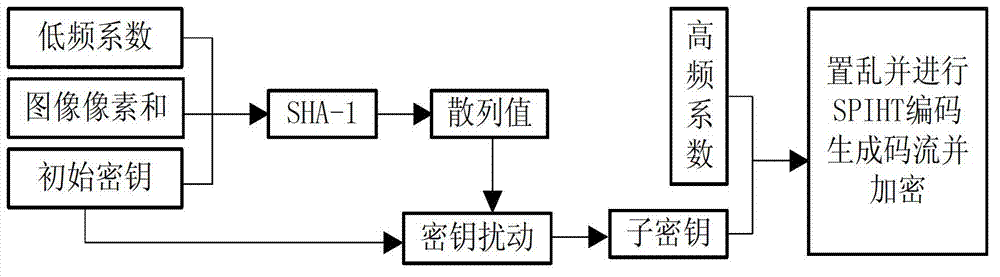
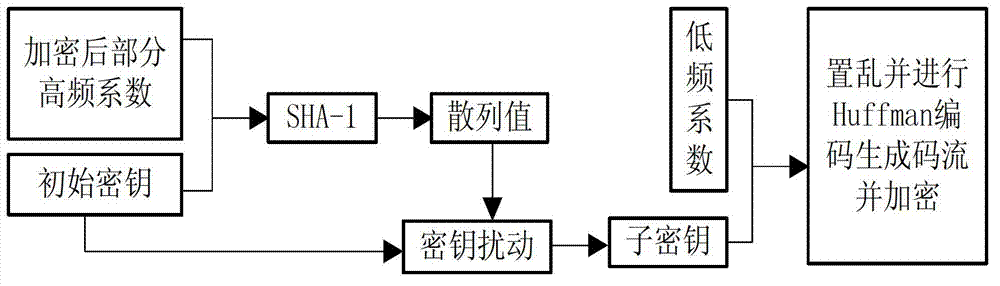
Image compression and encryption method based on wavelet transform and SHA-1 (secure has algorithm-1)
A technology of wavelet transform and image compression, applied in image communication, digital video signal modification, selective content distribution, etc., to achieve large key space, improve image storage and transmission efficiency, and resist exhaustive attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
[0064] Utilize general-purpose microcomputers, such as Intel Pentium 4 series microcomputers. Develop a compression encryption system in the MATLAB2009a programming environment. The program running platform is intel P43.0G CPU+2GB memory.
[0065] In the first step, set the initial key Key as [x 0H ,p 0H 、x 0L ,p 0L 、c 0 ], set the parameters to [0.405000869748940, 0.630979255024048, 0.421150774180423, 0.594355626412632, 3853080679] (subscript H means high frequency, L means low frequency). Calculate the sum of image pixel values, and its modulo 256 result is recorded as a=135. At the same time, 4 layers of lifting wavelet transform are performed on the original image, and the low sub-band LL 4 The coefficients are converted into a sequence L by column scanning, L and a form a sequence W, and the rest of the wavelet coefficients are divided into three parts: HL, LH, and HH according to the horizontal, vertical, and diagonal directions, and each part still maintains the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com