File unlocking and shredding method and device
A file unlocking and target file technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as lack of ability, weak resistance, weak resistance of driver-level malicious programs, etc., to achieve the effect of enhancing resistance and high success rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
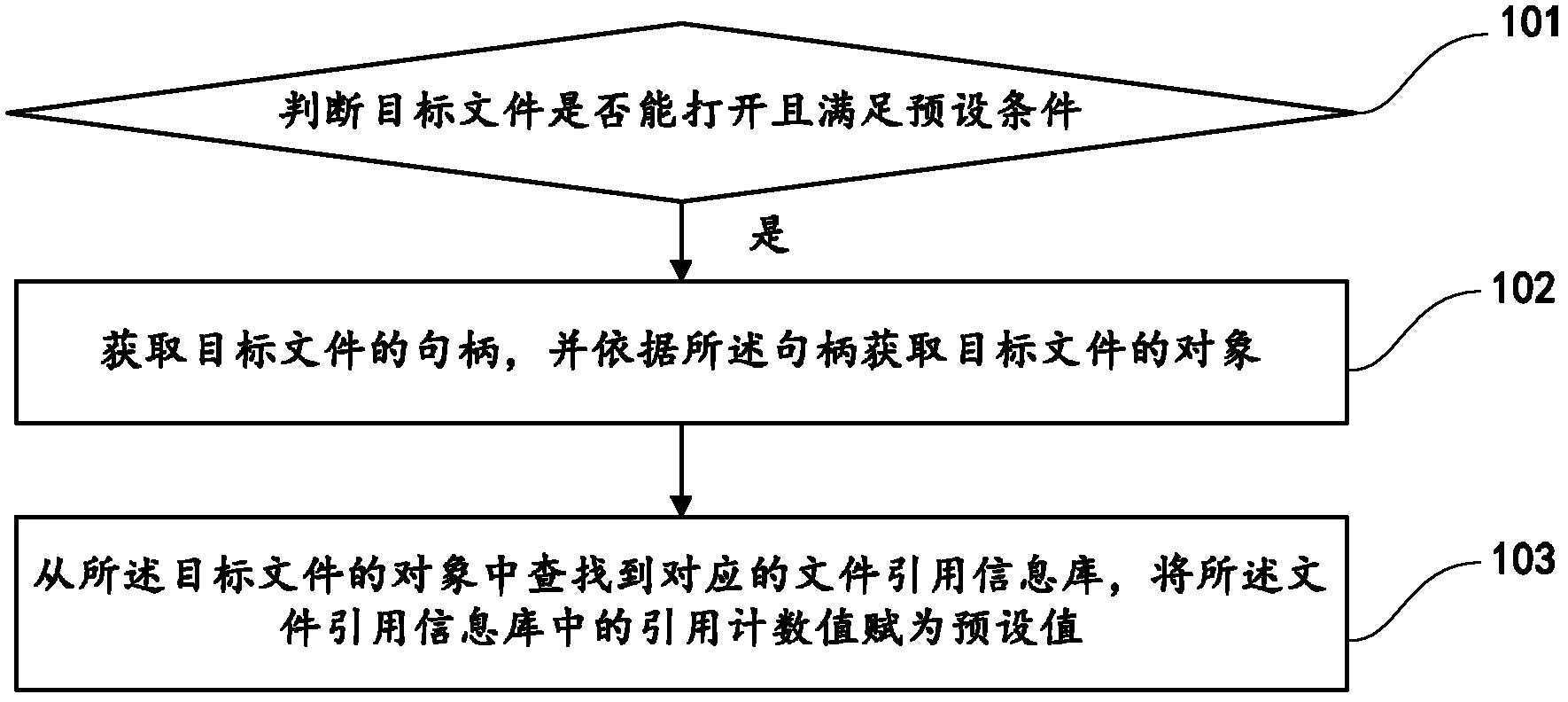
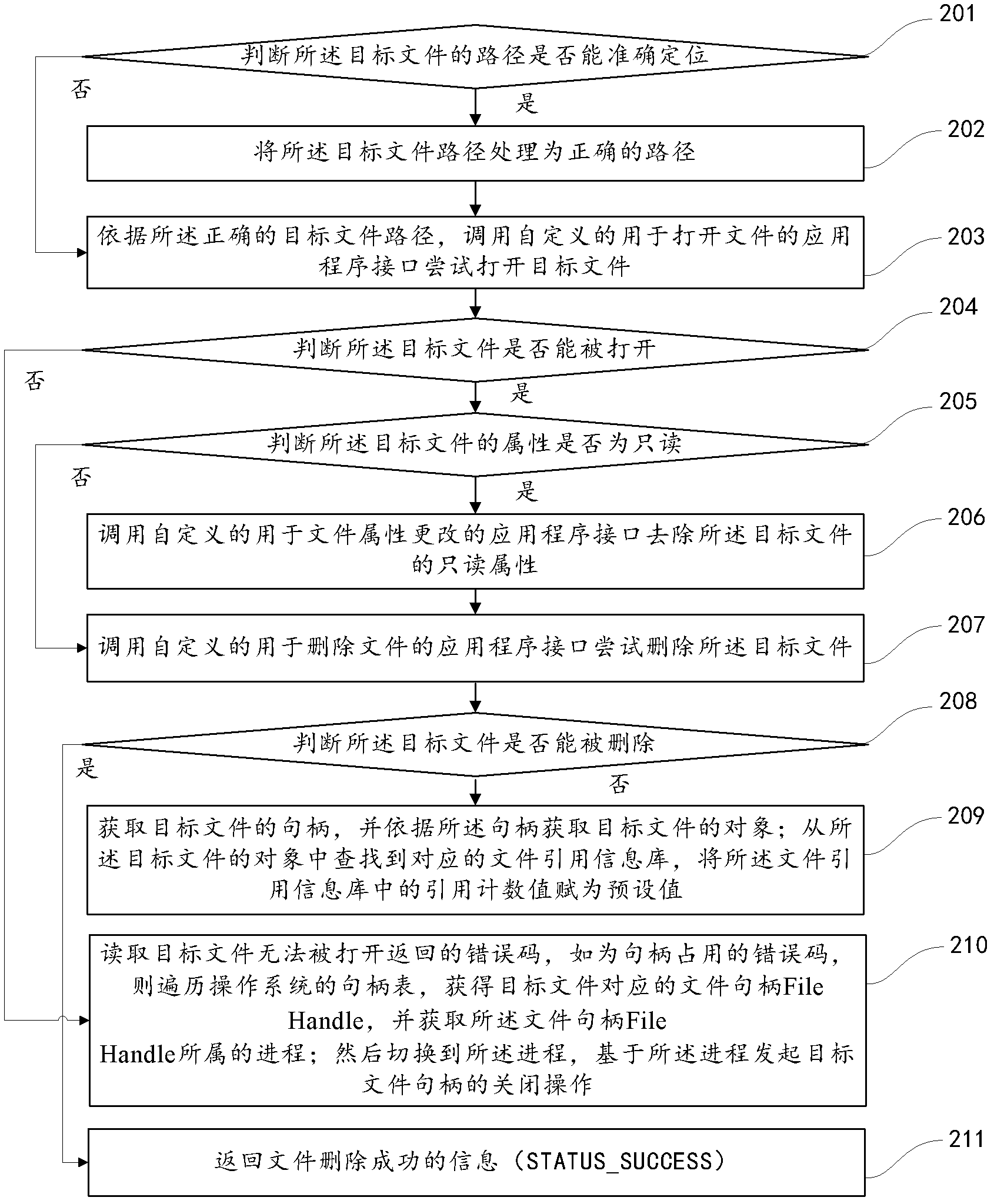
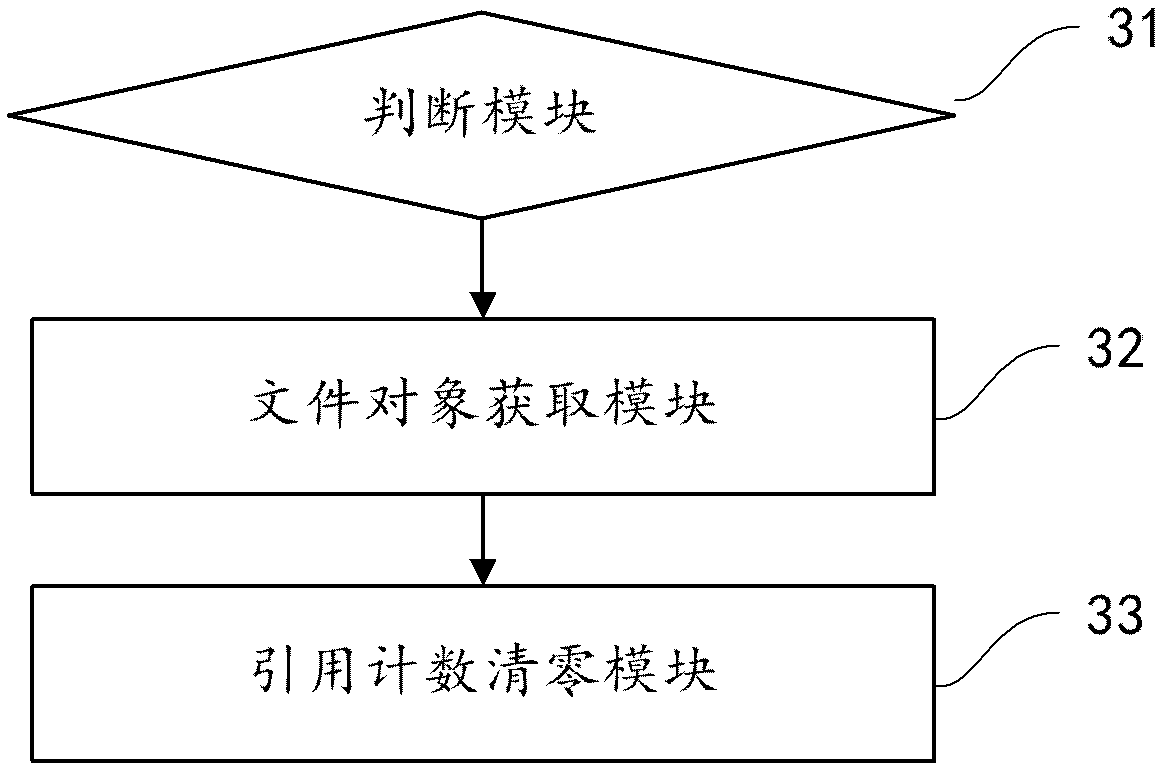
[0055] One of the core concepts of the embodiments of the present invention is to provide a mechanism for violently deleting files, that is, files that can be opened but cannot be deleted after some unlocking and shredding methods, such as file path preprocessing, read-only attribute removal, etc. Under such circumstances, through the internal data structure of the "direct operation" (DKOM term, Direct Kernel Object Manipulation) file system, enter the reference information database of the file, clear the reference count of the file, and realize the unlocking and shredding of the file.
[0056] refer to figure 1 , shows a flow chart of the steps of Embodiment 1 of a method for unlocking and shredding files of the present invention...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com