PKI (Public Key Infrastructure) implementation method based on safety certificate
An implementation method and technology for security certificates, which are applied in user identity/authority verification, electrical components, transmission systems, etc., can solve the problem of being vulnerable to external hacker attacks or snooping by internal management personnel, unable to meet the needs of network information security, and security risks. And other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
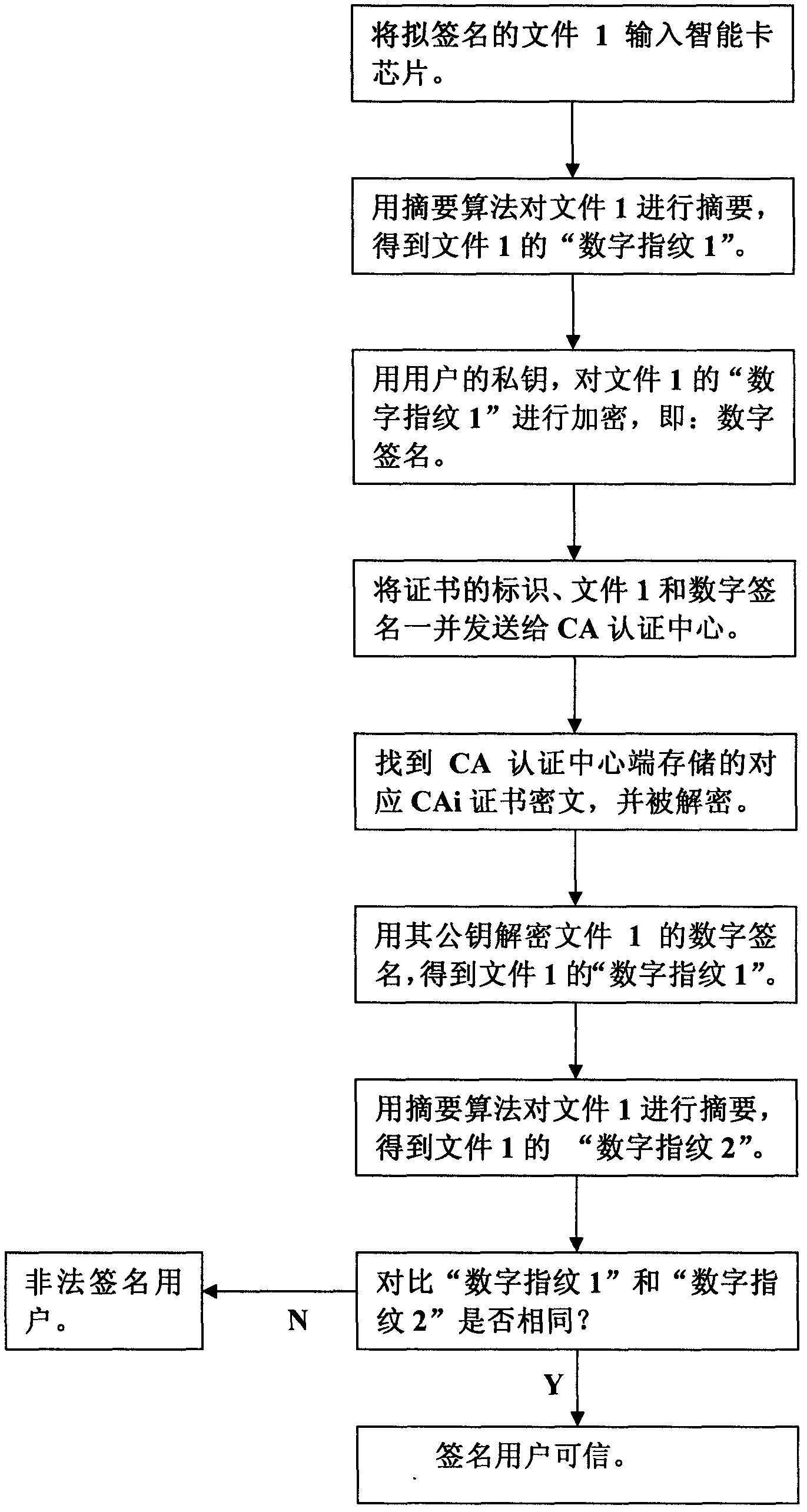
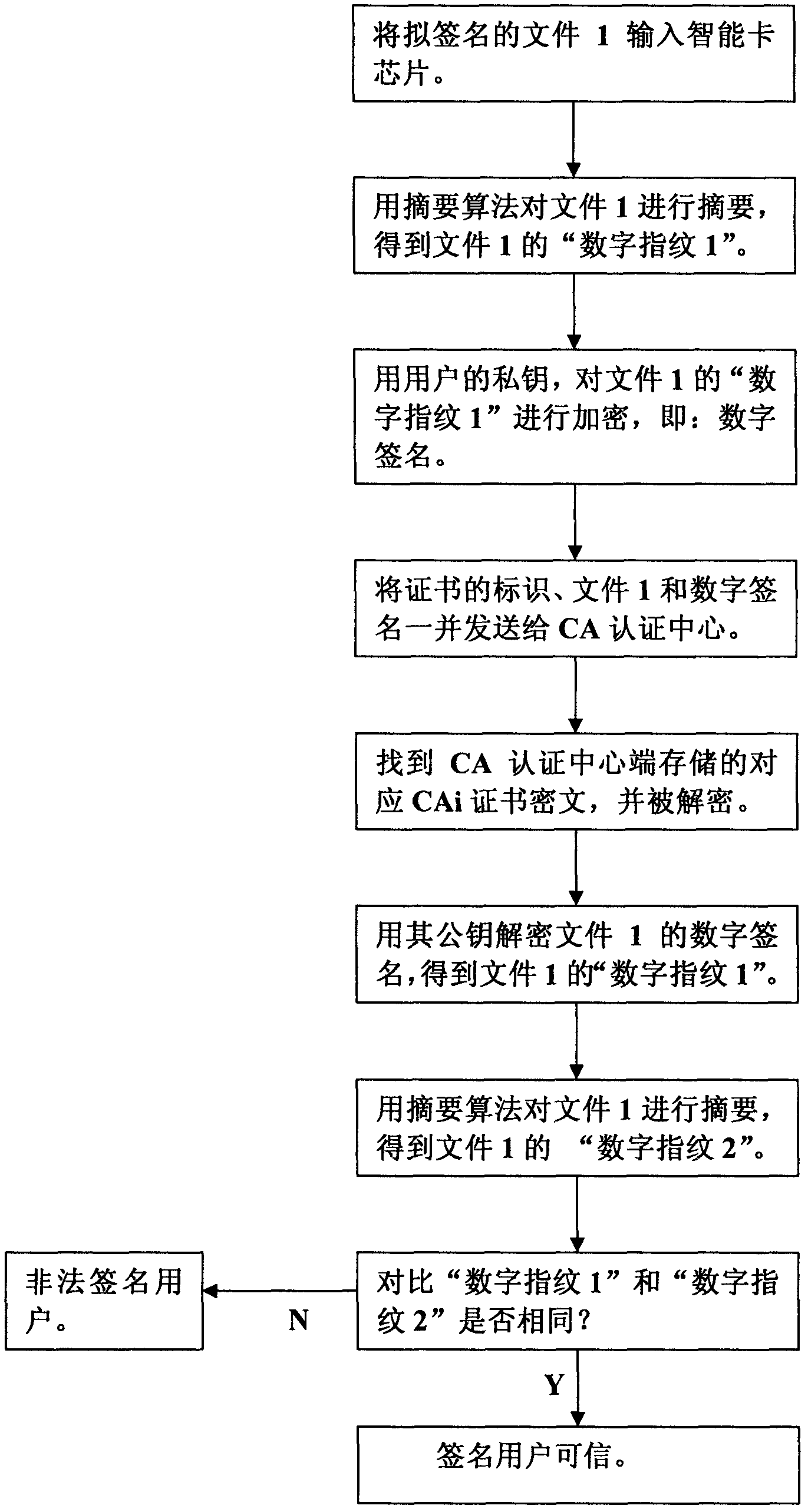
[0027] The following is attached figure 1 Explain the implementation steps of establishing a "chip-level" digital signature protocol between the client and the CA certification center:
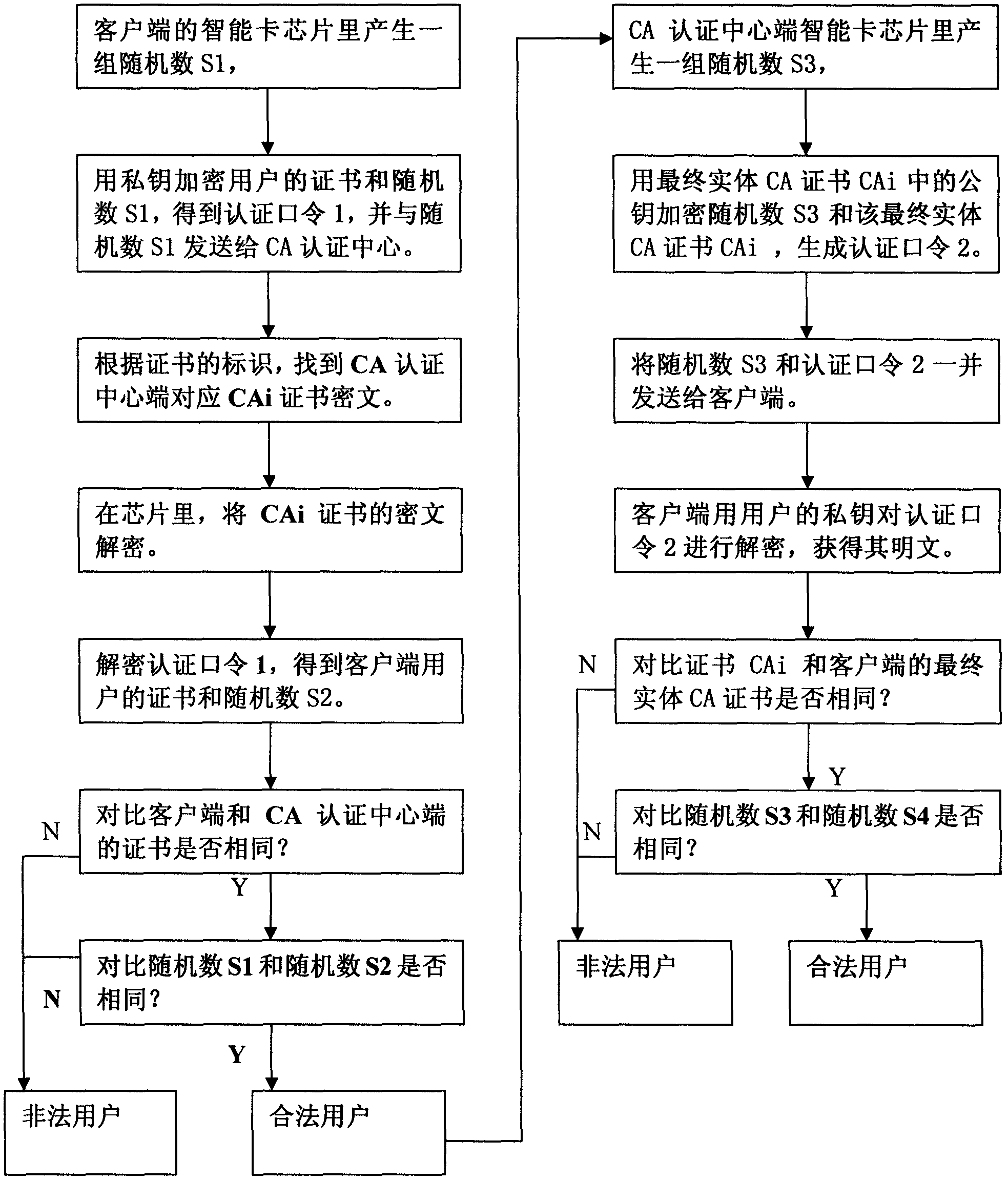
[0028] Firstly, the client input the file 1 to be signed into the smart card chip, and the encryption system of the client in the chip calls the digest algorithm to digest the file 1 to be signed to obtain the digest information of the file 1, that is, the "digital fingerprint" of the file 1 ", the client encryption system then invokes the user's private key to encrypt the "digital fingerprint 1" of file 1 to obtain the ciphertext of "digital fingerprint 1" of file 1, that is: digital signature, and the identification of the user's end-entity CA certificate , file 1 and the digital signature of the file are sent to the CA certification center together, and the CA certification center searches and locates the ciphertext of the corresponding user end-entity CA certificate CAi in the certificate ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com