False data identification method based on digital watermarking technology
A false data, digital watermarking technology, applied in electrical components, wireless communication, network topology and other directions, can solve the problem of MAC code misleading base station, MAC value security problem, MAC code easily damaged and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] specific implementation plan
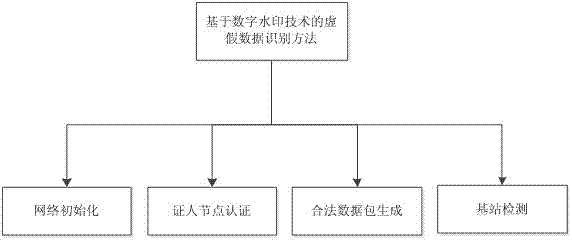
[0044] The specific implementation scheme of the false data identification method based on digital watermark is as follows:
[0045] 1. In the network layout stage, it enters the normal working state after initialization;
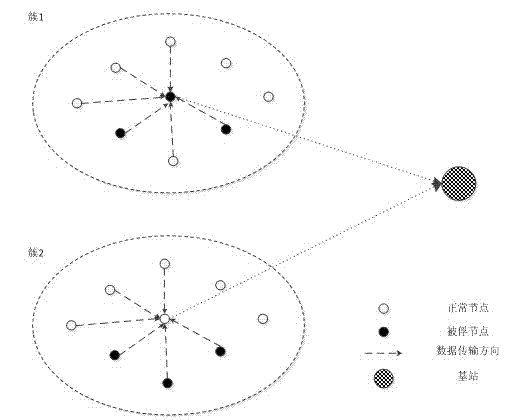
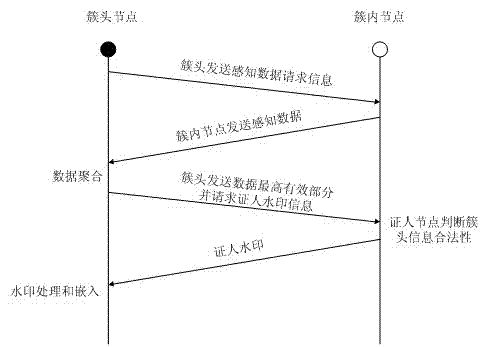
[0046] 2. After the time of interest occurs in the sensing area, each node collects data and sends it to the cluster head node, and the cluster head node processes to obtain the fusion data;
[0047] 3. The cluster head node extracts the most significant part (MSP) of the fusion data and sends it to the nodes in the cluster together with the witness information request;
[0048] 4. After the nodes in the cluster receive the MSP of the fused data, they compare it with the data collected by themselves. If they are not similar, they do not provide witness information; The own key number is sent to the cluster head together;
[0049] 5. The cluster head node generates legal data packets until it receives t witness inform...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com