Digital content trusted usage control method based on cloud computing
A digital content and control method technology, applied in the Internet field, can solve the problems of terminal equipment confidential privacy data and platform configuration information leakage, cracking and tampering, and achieve the effect of guaranteeing two-way trust relationship and protecting confidential privacy data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
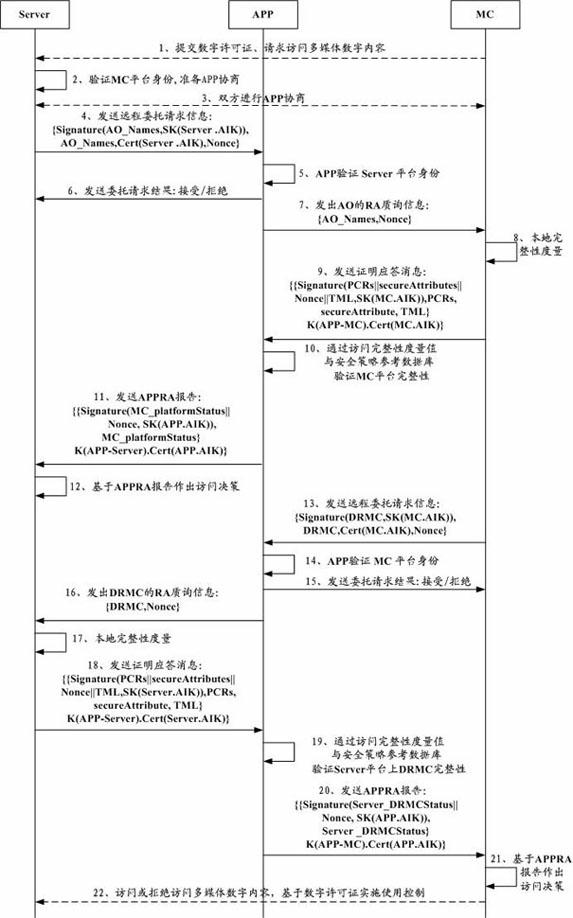
[0066] based on figure 2 Framework, the protocol flow of the technical solution of the present invention can be specifically implemented as follows:
[0067] Here, it mainly includes a cloud-based multimedia server (Server) and a mobile terminal (Mobile Client, MC), which are two-way verifiers (or verifiers) and verifiers (or verifiers) respectively. In addition, it also includes a trusted third party - the authentication agent (APP). Among them, the DRM controller (DRMC) is the verified object of the multimedia cloud server.
[0068] Before the start of this protocol process, it is assumed that entities such as Server, MC, and APP have obtained the certificate of the attestation identity key AIK (Attestation Identity Key, attestation identity key) from the certificate and license server, K (APP-Server) and K (APP -MC) are the shared secret keys generated between APP, Server, and MC before the RA session starts.
[0069] The two-way integrity verification security protoco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com