Voice encryption and decryption method for conversion parties on basis of voice print
An encryption, decryption, and voice technology, which is applied in the field of voice encryption and decryption based on voiceprint, can solve the problems of increasing the complexity of voice processing and methods, and achieve the effects of reducing system resource overhead, good security, and fast encryption speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with accompanying drawing.
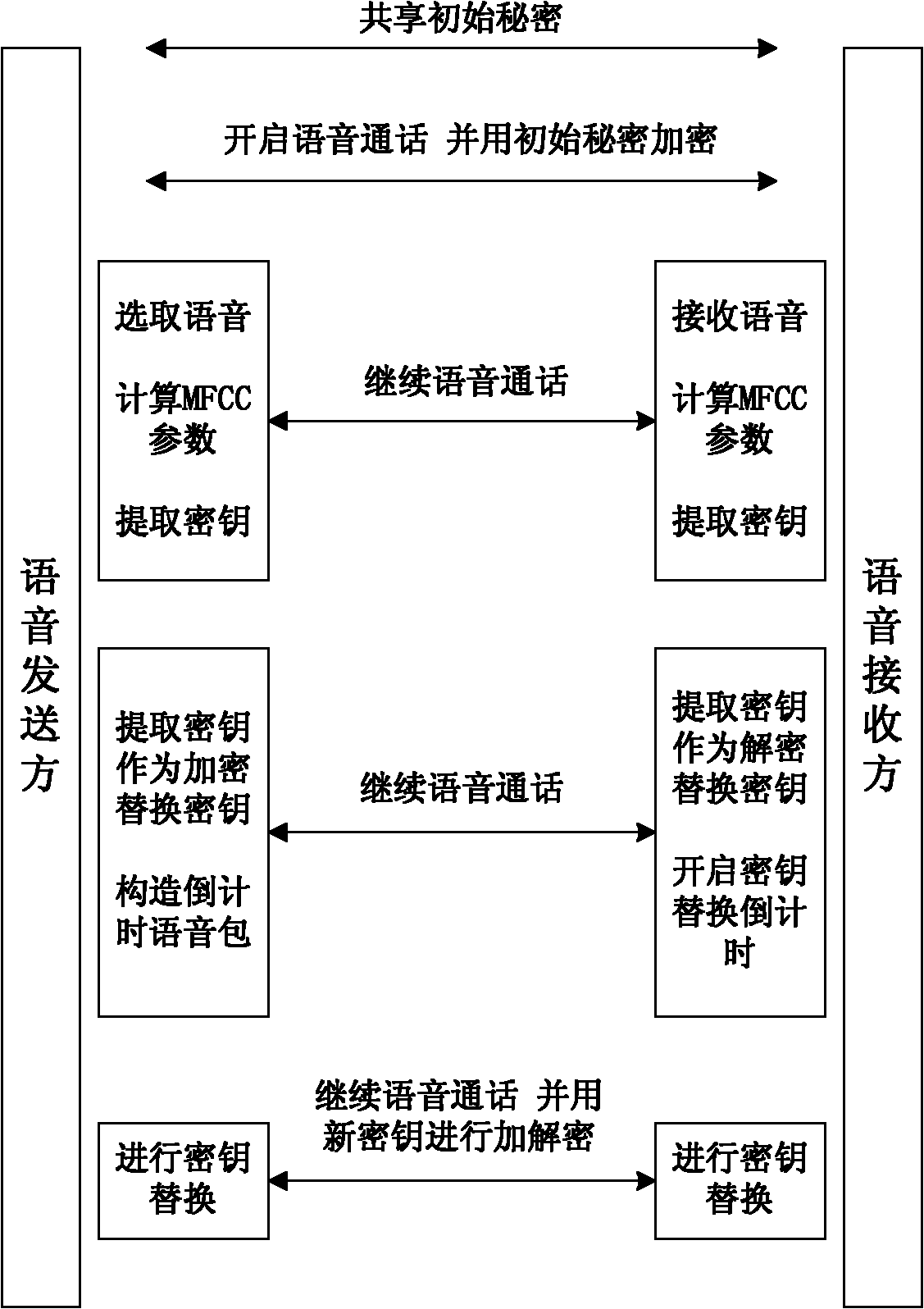
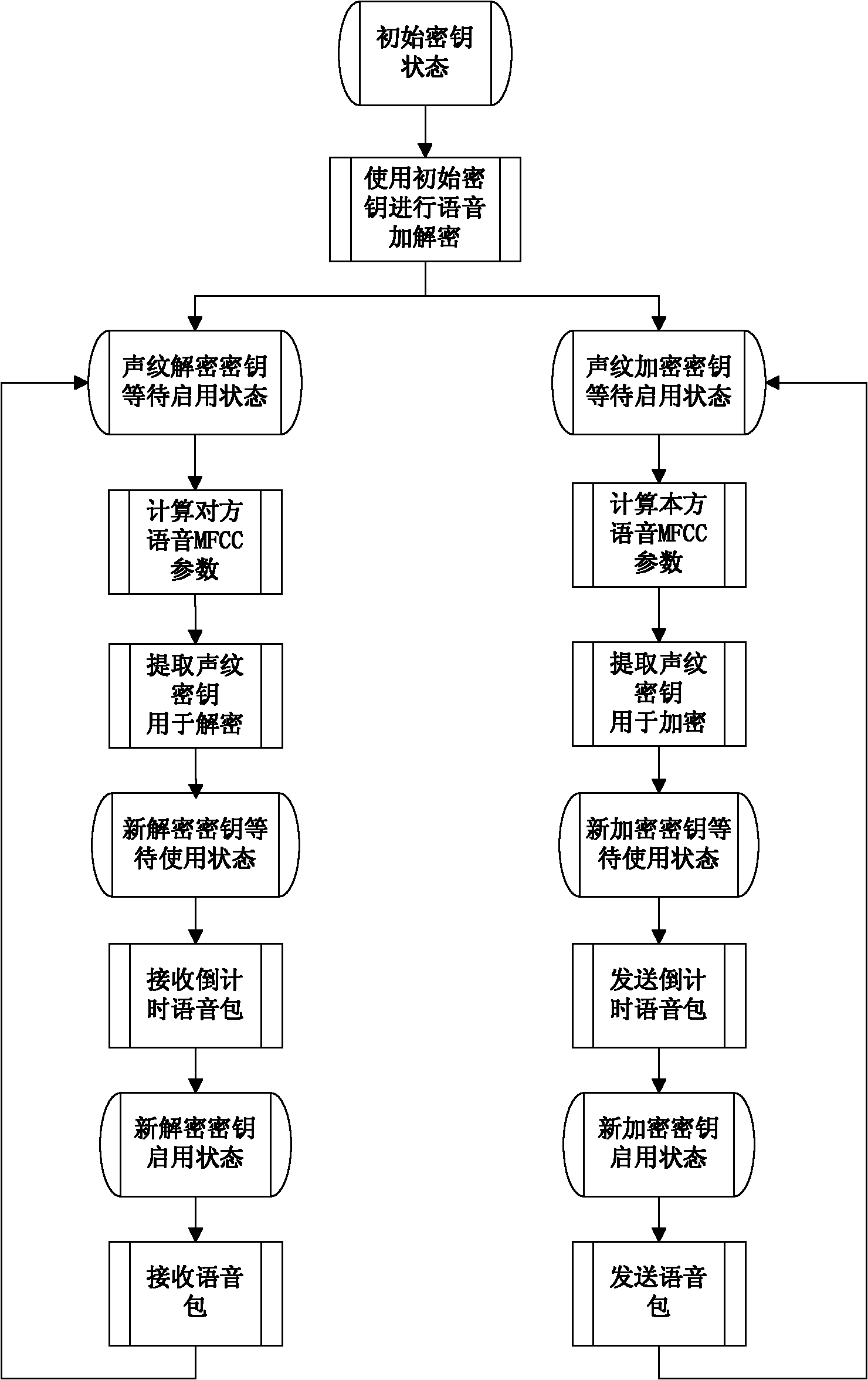
[0025] 1) Both parties in the call exchange voice streams, and this process is repeated;
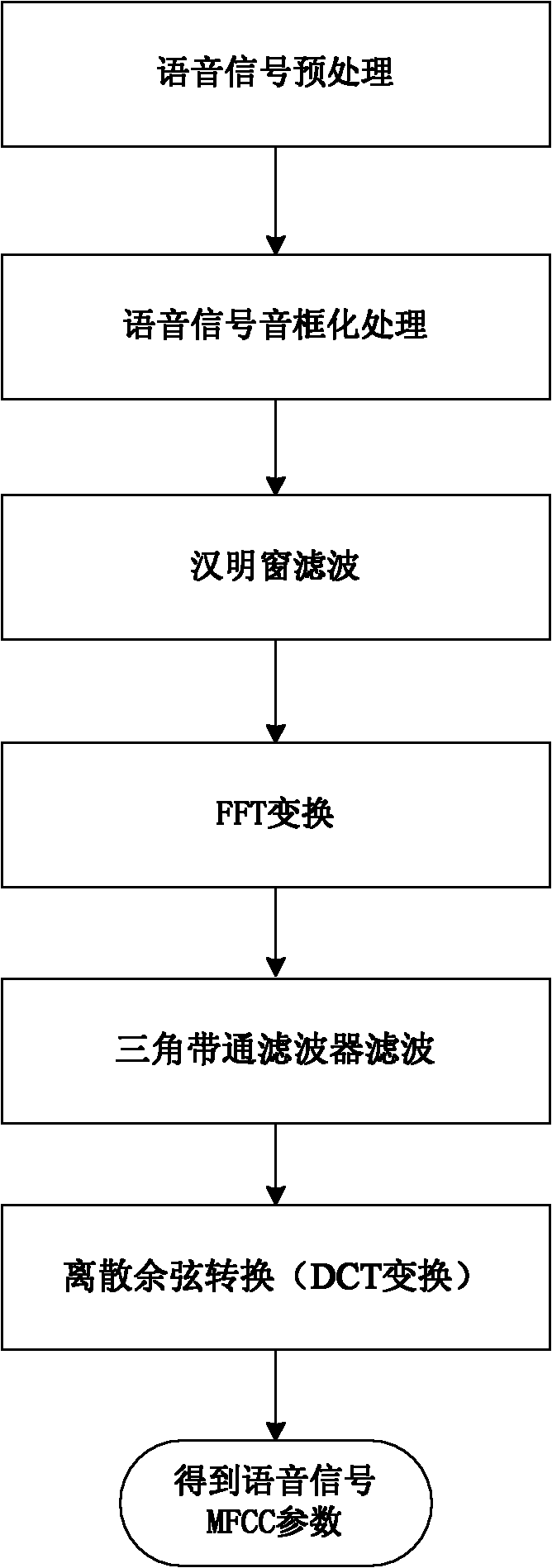
[0026] 2) The speech signal flow presents randomness according to the dialogue content and physiological state of the talker, and on this basis, the speech feature parameters (MFCC parameters) extracted after speech signal processing also present randomness. (MFCC parameters vary with the speaker's tone, syllable, syllable context, glottal airflow model, and their own unique pronunciation.)
[0027] Based on the above facts, we can extract effective keys from the voice signals of both parties in the call and implement encryption and decryption. Due to the large volume of voice signals, a sufficiently long effective key can be extracted, and it has good randomness. Therefore, the present invention uses the XOR encryption method to encrypt and decrypt the voice stream. In practice, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com