BIOS firmware Rootkit detection method based on behaviour characteristic
A detection method and behavior technology, applied in the field of computer security, can solve the problems of BIOS firmware code analysis and update conflicts, it is difficult to keep up with the rapid growth of malicious code, and the versatility cannot meet the needs, so as to prevent computer system security attack accidents, improve the Versatility and extensibility, resistance to code obfuscation effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
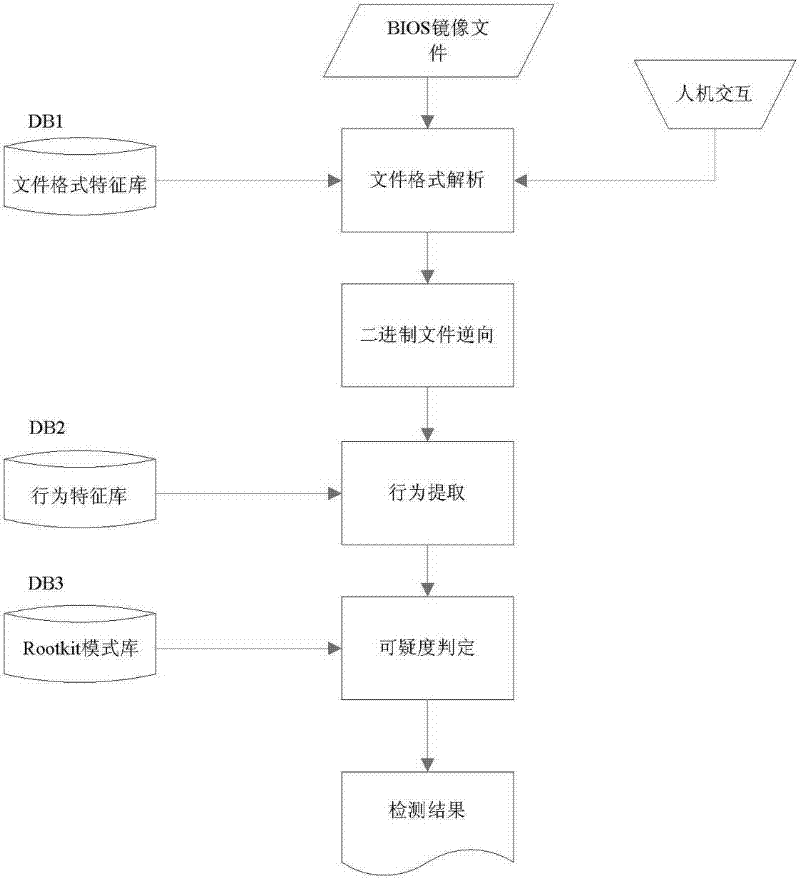
[0031] Embodiment one: see figure 1 , the specific implementation process of the BIOS firmware Rootkit detection method based on the behavioral characteristics of the present invention is as follows:
[0032] 1. File format analysis
[0033] File format analysis first extracts the firmware model and the version number field of the image file from the BIOS image file, and then reads the structure information, module features and specific compression algorithm of the corresponding image file from the database DB1 according to these information, according to these information to split the image file. Decompresses the compressed module to extract a structural view of the entire image file. For the key modules, through the analysis of the BIOS specification and structural characteristics, the information to guide the reverse analysis and the formalized function description information are established in advance and stored in DB1. The key module is identified through the feature ...
Embodiment 2
[0040] Embodiment two: see figure 1 , figure 2 . The present embodiment is based on the BIOS firmware Rootkit detection method of behavior characteristic, adopts the following steps to carry out Rootkit detection to BIOS image file:
[0041] a. Analyze the BIOS binary image file to be analyzed, according to the feature word of the BIOS image file
[0042] The BIOS model to which the image file belongs and the version number of the image file are read from the database DB1, and the extracted compression module is decompressed according to the compression algorithm and structural features used by the image file. Obtain a complete structural view of the image file to achieve preliminary separation of code and data.
[0043] b. Reverse the extracted binary code module, and make the semantics of the instructions in the code fragment equivalent
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com