RFID (Radio Frequency Identification Device) inquiring-response safety certificate method based on grading key
A security authentication and key technology, applied in the field of RFID communication security, can solve the problems of denial of service, security risks, counterfeiting, etc., to achieve the effect of easy hardware implementation, improve system security, and save label cost and power consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
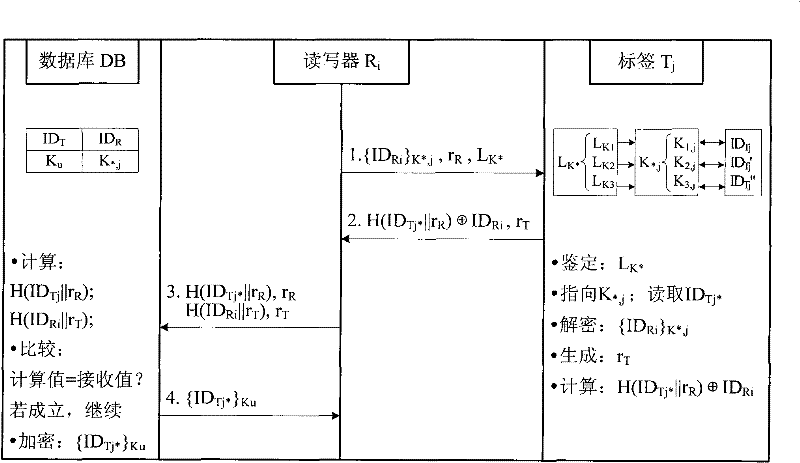
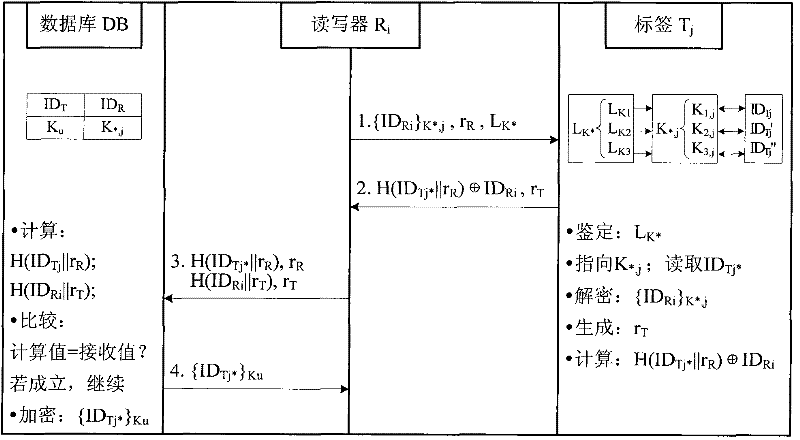
[0045] The security authentication protocol proposed by the present invention will be illustrated and described below in conjunction with the accompanying drawings and the application examples of the valuables traceability management system.
[0046] 1. System scene construction
[0047] In the terminal data acquisition system for the traceability management of RFID valuables, there are M legal readers R i (i=1, 2, ..., M), N tags T j (j=1, 2, . . . , N) and the background database DB. Among them, the reader can be divided into three access levels, authorized to access part or all of the data information of the specified tag. Tags store user data involved in the production, processing, circulation, and consumption of valuable materials (including relevant manufacturer information, material information, supply chain relationship information, storage and transportation information, etc.). Authorize the reader to read. There are designated authentication keys K between reader...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com