Intrusion defence system having active defence capability and method thereof
An intrusion prevention system and active defense technology, applied in the field of information security, can solve the problems of untimely update, timely accuracy, and speed limit of intrusion outbreak
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The implementation of the present invention will be described in detail below in conjunction with the accompanying drawings and examples, so as to fully understand and implement the process of how to apply technical means to solve technical problems and achieve technical effects in the present invention.
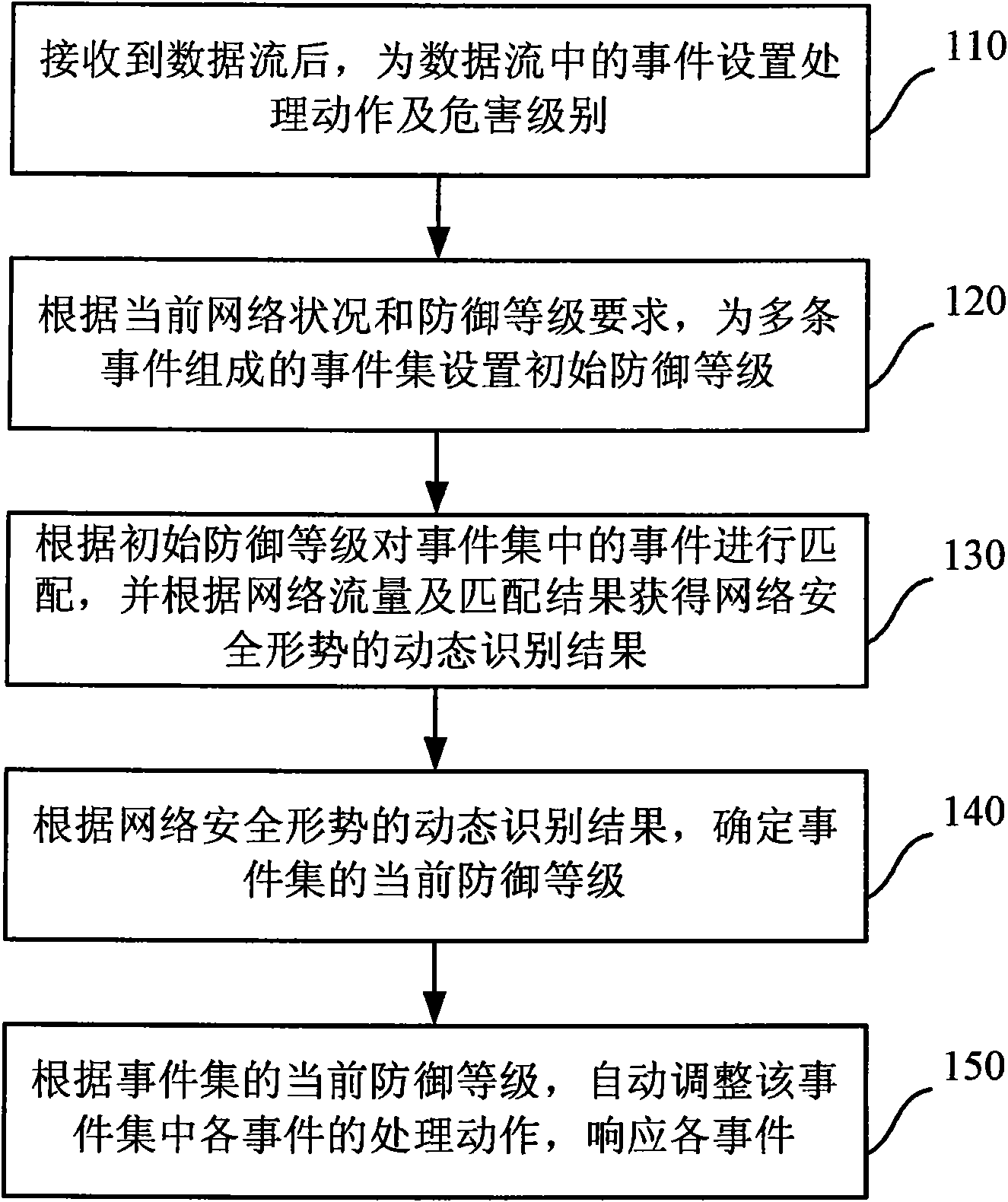
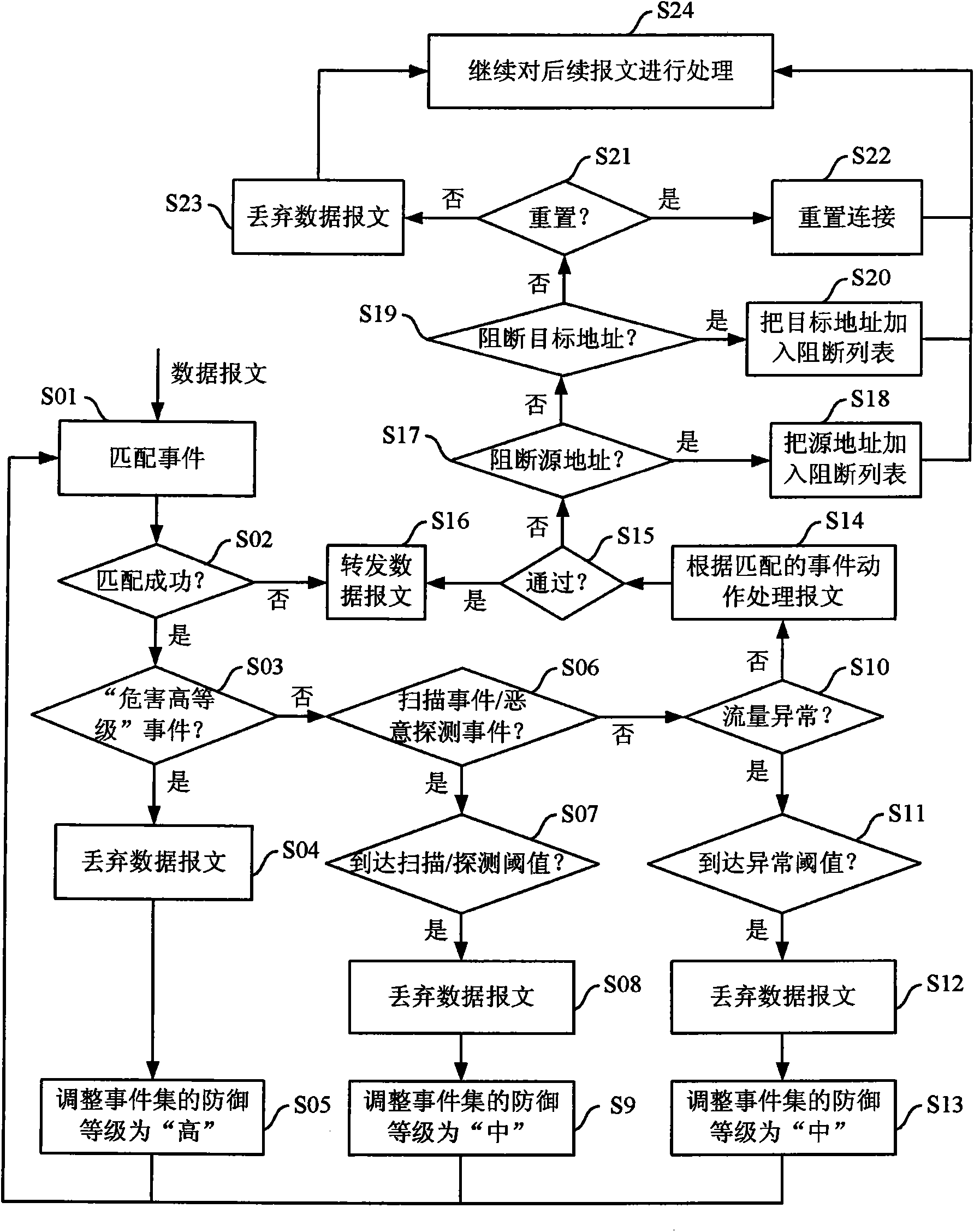
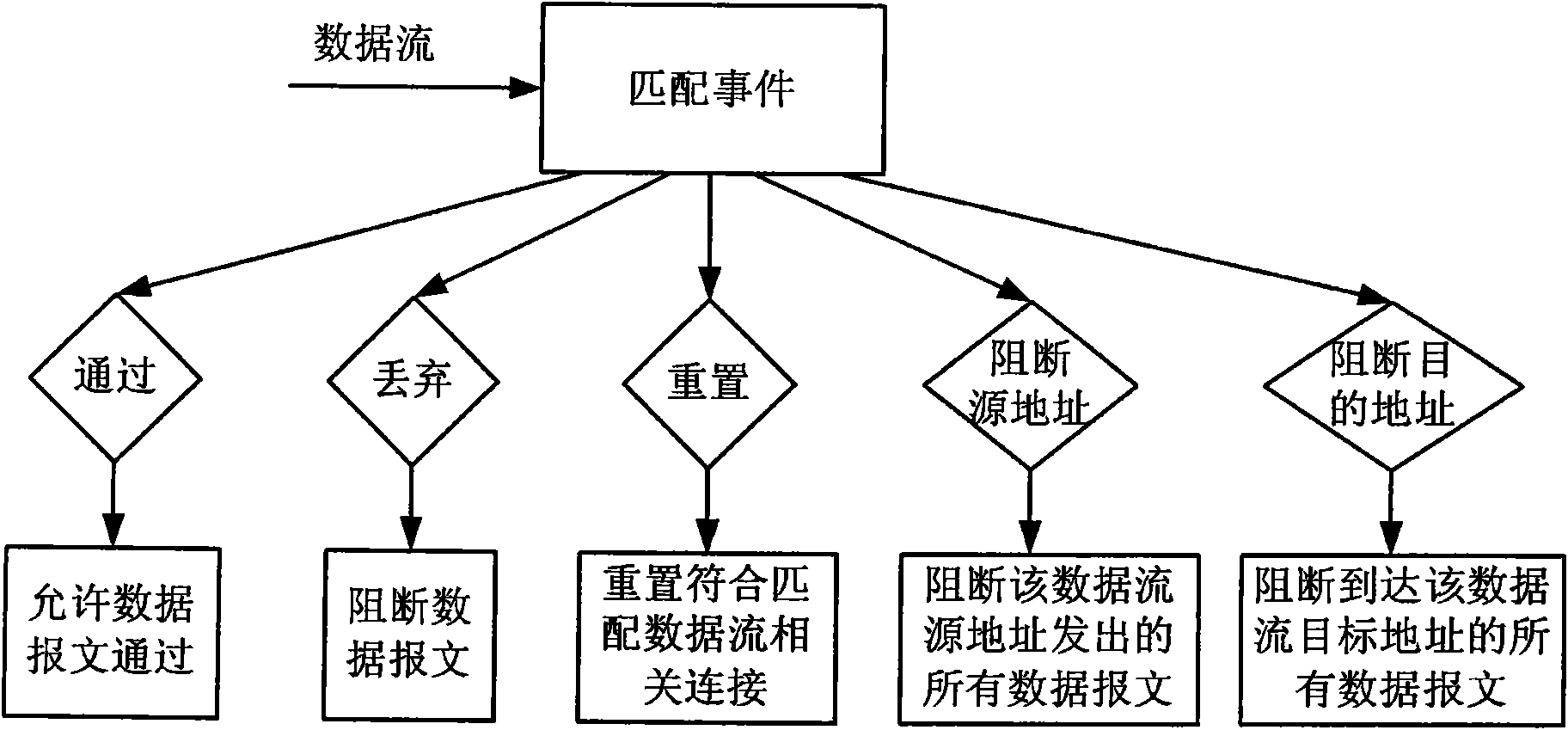
[0033] For a new attack method or technology that cannot be identified by the intrusion detection device, it is called an unknown attack. To effectively prevent unknown attacks, the current defense method must be changed from passive to active. The existing "passive" feature matching methods, or "active" push upgrade services, mainly rely on security vendors to provide security services, which are bound to be affected by security vendors' own security capabilities, geographical location, upgrade frequency and other factors. limit. Moreover, the update rate of the current attack methods generally exceeds the update frequency of the signature database, so the current t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com