Method, system and entity for authenticating notes in network service
A network service and authentication method technology, applied in transmission systems, digital transmission systems, payment systems, etc., can solve the problems of complex service logic functions and centralized management and maintenance of bills, and achieve the effect of simplifying logic functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
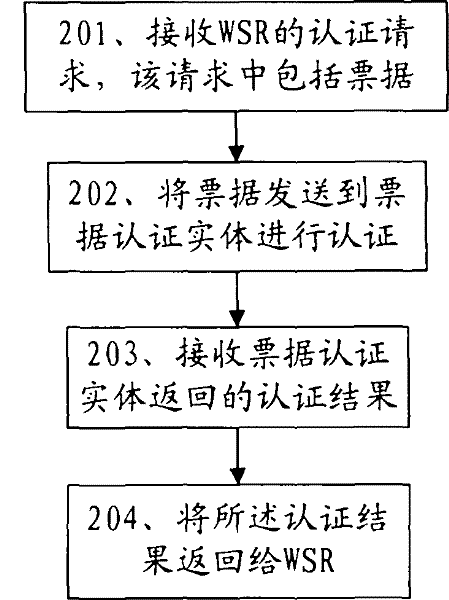
[0067] This embodiment provides a bill authentication method in network services, such as figure 2 As shown, the ticket authentication method includes the following steps:
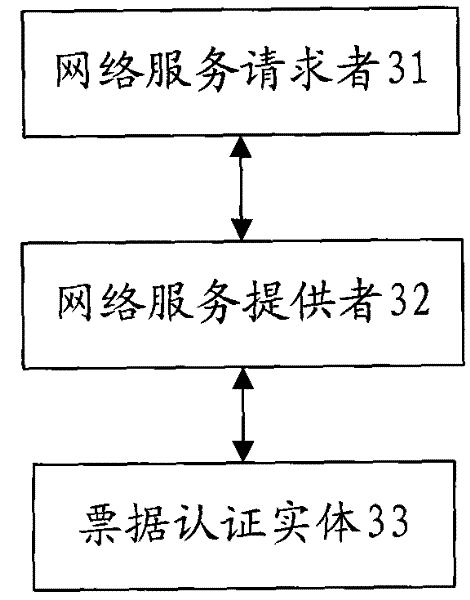
[0068] 201. If the user requests the service provider to provide corresponding services, and the service requires the network service provider to authenticate the user, the service provider will send an authentication request to the network service provider as the network service requester, and the authentication request includes the network A ticket provided by the service requester.
[0069] 202. The network service provider sends the ticket to a ticket authentication entity, so that the ticket authentication entity can authenticate the ticket.
[0070] 203. After completing the authentication, the ticket authentication entity returns an authentication result to the network service provider.
[0071] 204. After receiving the authentication result returned by the ticket authentication entity, the netwo...
Embodiment 2
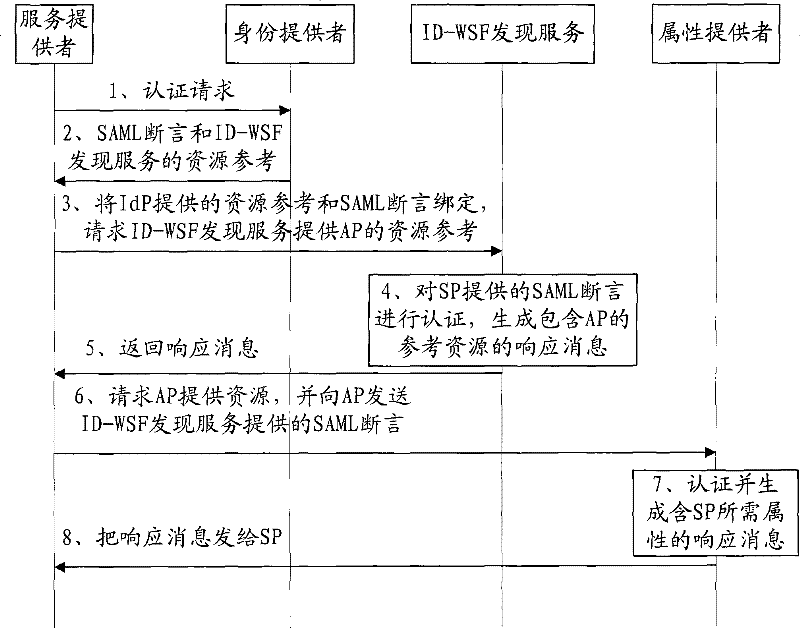
[0078] This embodiment takes figure 1 The acquisition of user identity attributes in the application scenario is used as the application scenario. In this application scenario, the SP acts as the network service requester, and the IdP, ID-WSF discovery service, and AP all act as the network service provider. Since the IdP itself has the authentication function, this implementation For example, the IdP is used as the ticket authentication entity at the same time. Such as Image 6 As shown, in this application scenario, the ticket authentication method in the network service is as follows:
[0079] 601. The SP, as a network service requester, initiates an authentication request to the IdP, requesting authentication of the user's SAMLAssertion (assertion), where the SAML assertion is equivalent to a ticket provided by the user.
[0080] 602. The IdP authenticates the user's SAML assertion, and sends the authentication result to the SP. If the authentication result is passed, it...
Embodiment 3
[0099] This embodiment is also based on figure 1 Obtaining user identity attributes in is used as an application scenario. In this application scenario, the SP is also used as the network service requester, the IdP, ID-WSF discovery service, and AP are all used as the network service provider, and the IdP is used as the ticket authentication entity. Such as Figure 7 As shown, in this application scenario, the ticket authentication method in the network service is as follows:
[0100] 701. The SP, as a network service requester, initiates an authentication request to the IdP, requesting authentication of the user's SAML assertion, where the SAML assertion is equivalent to a ticket provided by the user.
[0101] 702. The IdP authenticates the user's SAML assertion, and sends the authentication result to the SP. If the authentication result is passed, the resource reference of the user's ID-WSF discovery service and the ticket allocated by the IdP to the SP need to be returned ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com