Method and system for assessing wireless local area network
A wireless local area network and access point technology, which is applied in the field of wireless local area network access methods and systems, can solve the problems of denial of service attacks, potential safety hazards, hidden dangers, etc., and solve the security problems of mutual identity authentication and communication link encryption Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
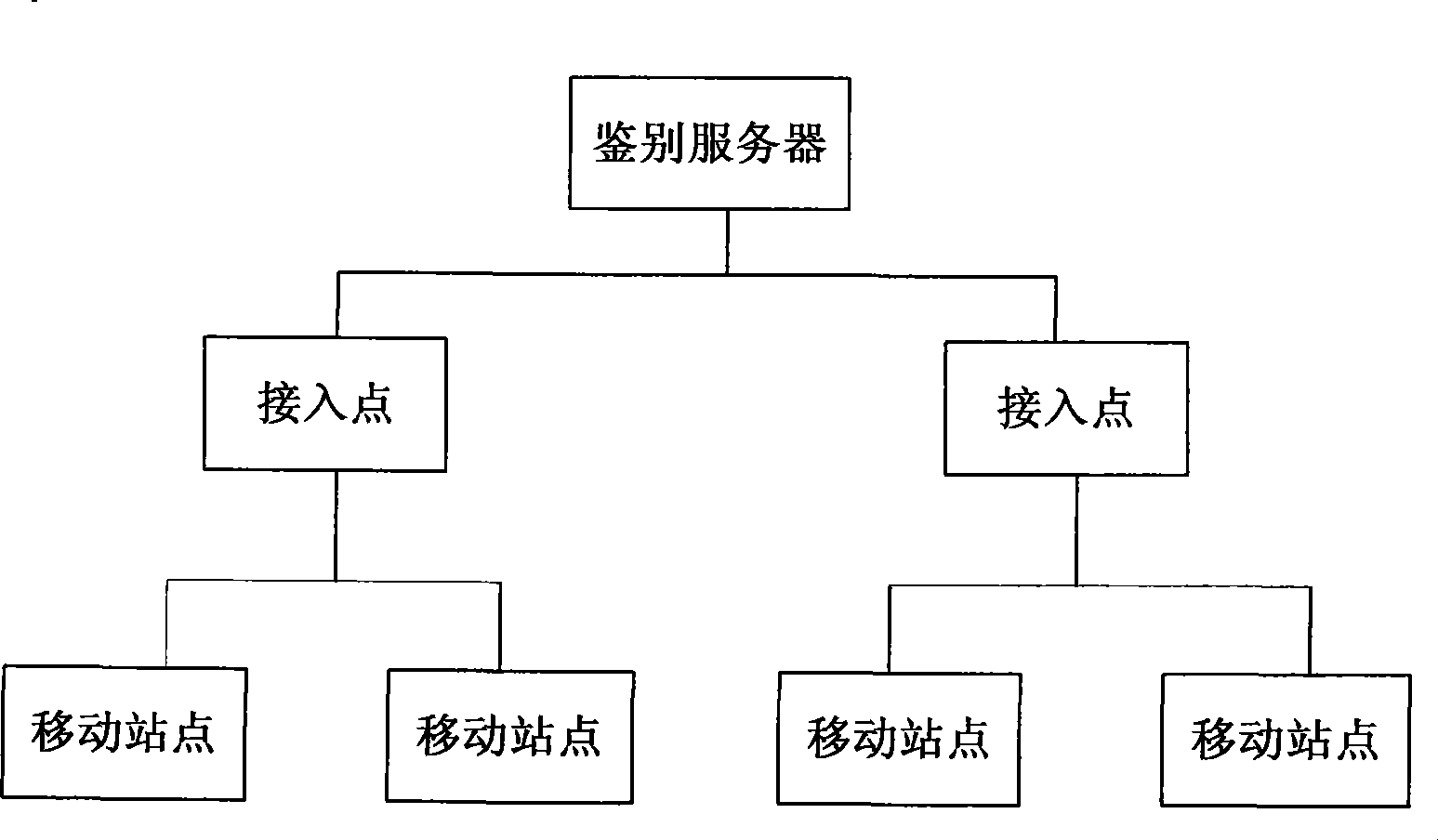
[0043] The invention provides a method for using public key encryption technology in a wireless local area network to enable an authentication server to perform identity authentication on a mobile station in a certificate authentication mode. Only when the authentication is successful, the mobile station can associate with the access point.
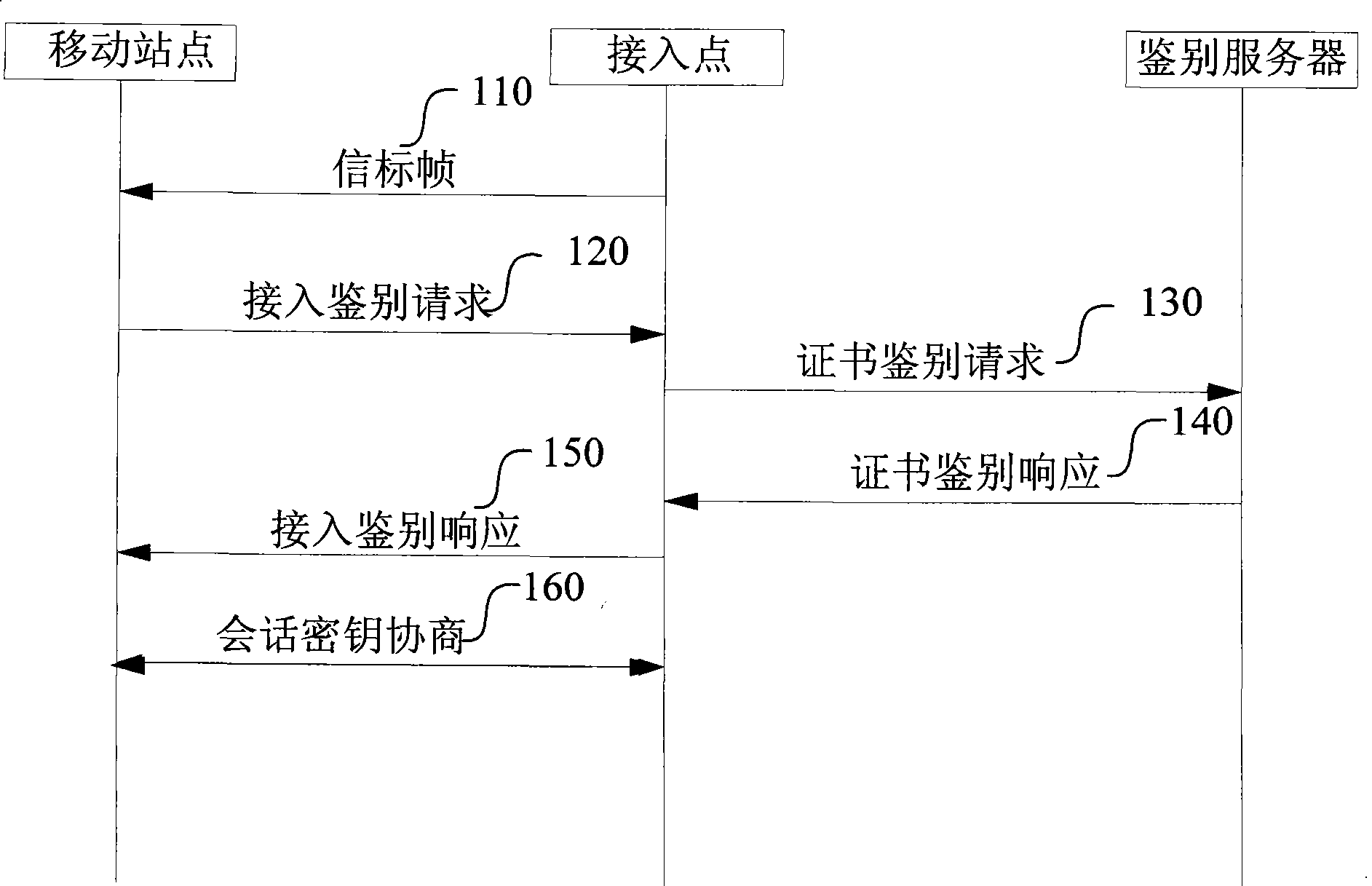
[0044] The access authentication process in the embodiment of the present invention includes an authentication process based on certificate authentication and a session key negotiation process in the certificate authentication process; wherein:
[0045] The authentication server distributes digital certificates to users of each mobile site, and generates asymmetric key pairs for users. Asymmetric key pairs include public keys (referred to as public keys) and private keys (referred to as private keys). The public key is stored in the digital certificate, and the private key is distributed to the mobile site through other safe means. In add...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com