Reducing security protocol overhead in low data rate applications over a wireless link
A technology for wirelessly sending and securing data, applied in the security field of wireless communication networks, and can solve problems such as unauthorized use of resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In the following description of various example embodiments, reference is made to the accompanying drawings, which form a part hereof, and in which are shown by way of illustration various embodiments in which the invention may be practiced. It is to be understood that other embodiments may be utilized and structural and functional modifications may be made without departing from the scope of the present invention.
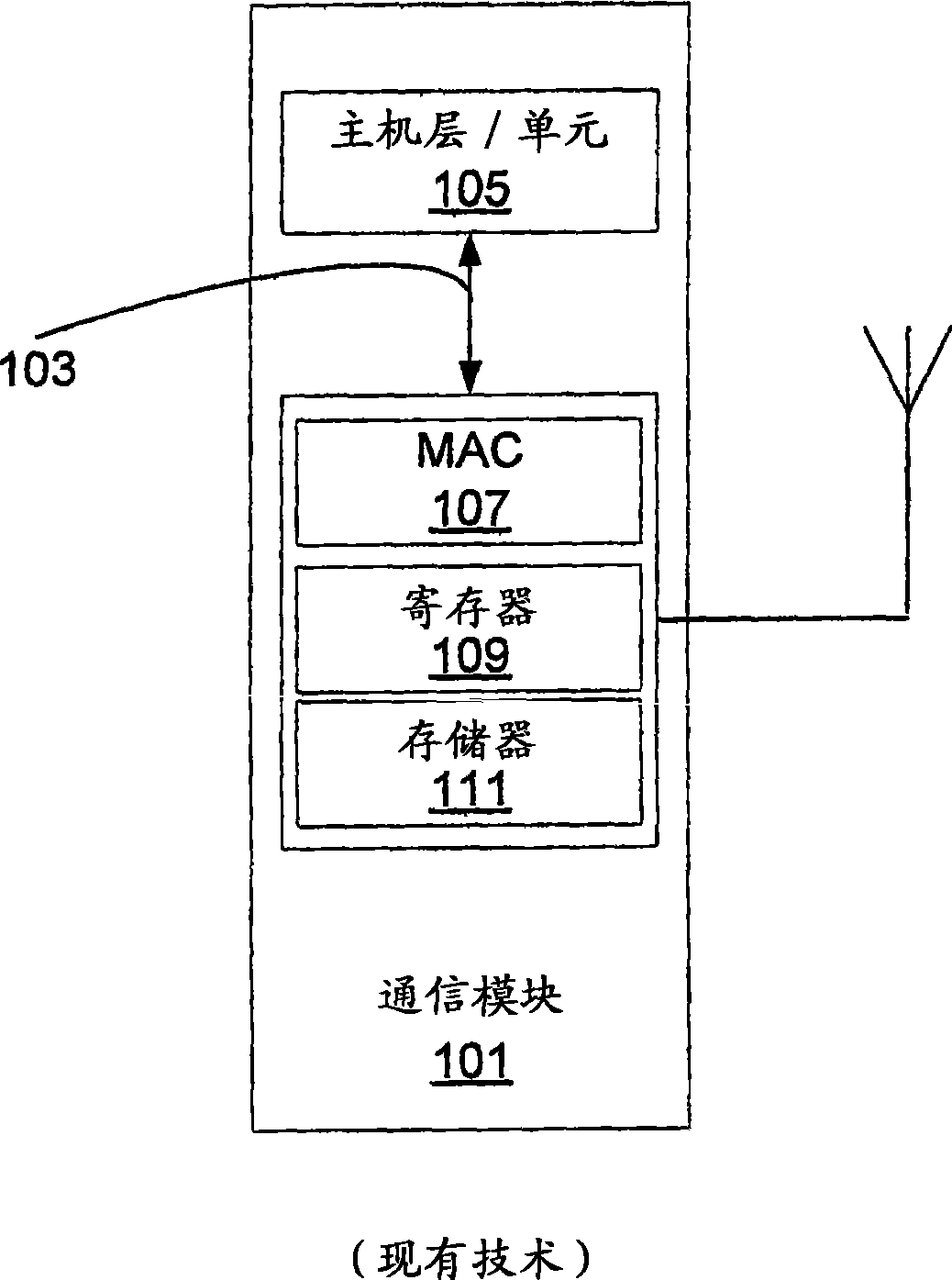
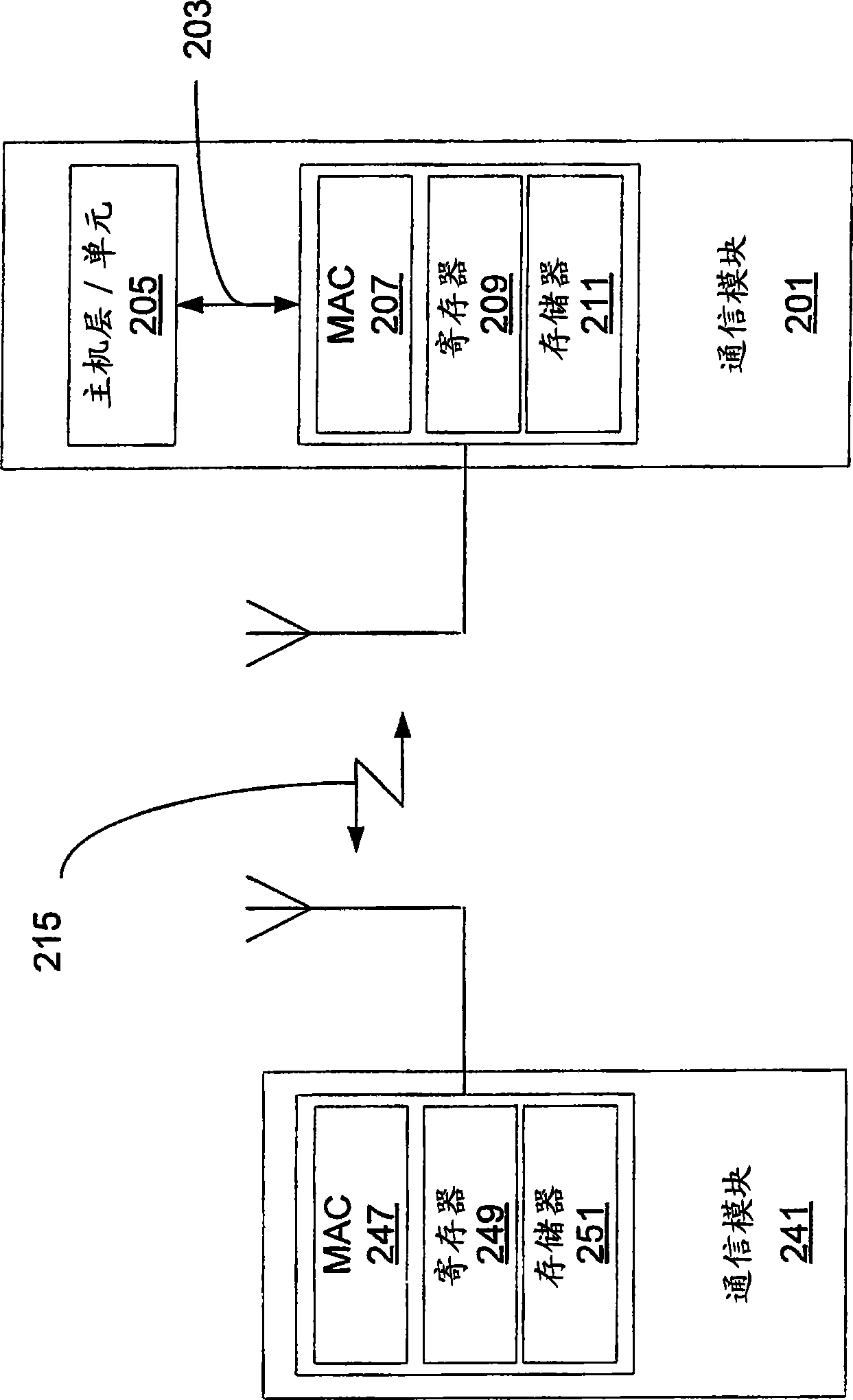
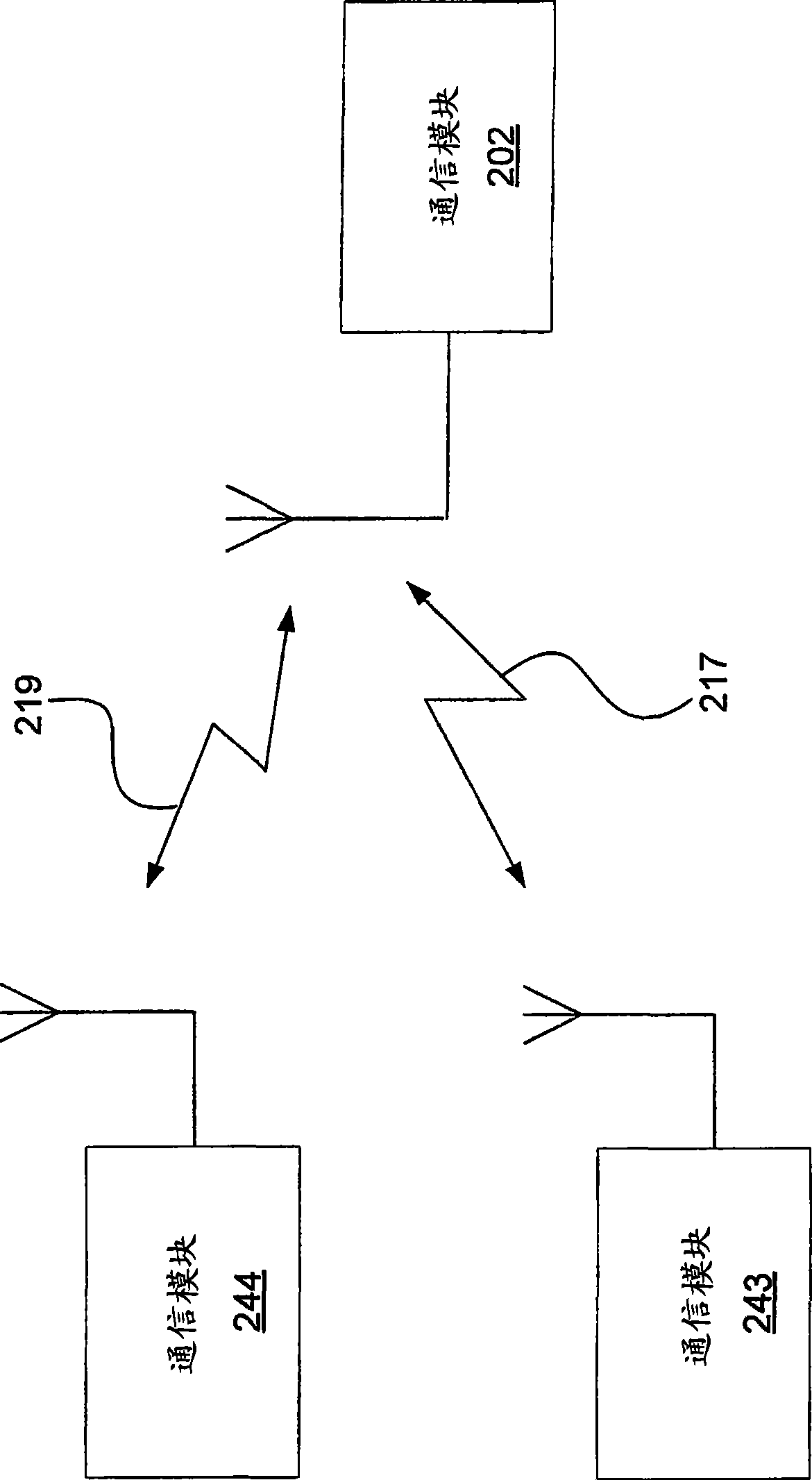
[0026] Such as figure 2 As shown in , the communication module 201 includes an interface 203 between a host layer or unit 205 and a MAC layer 207 . It is also shown that the communications module 201 includes registers 209 and a memory space 211 . In one embodiment, the registers 249 and memory 251 of the communications module 241 can be accessed through the air interface 215 without the presence or action of a host layer in the module. The host layer or unit 205 of the communication module 201 may handle the functions of the air interface 215 for the ho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com