Anti-disclosure mail safe card and method for detecting disclosure mail
An anti-leakage, security card technology, applied in secure communication devices, electrical components, digital transmission systems, etc., can solve problems such as information leakage, loss, email security loopholes, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
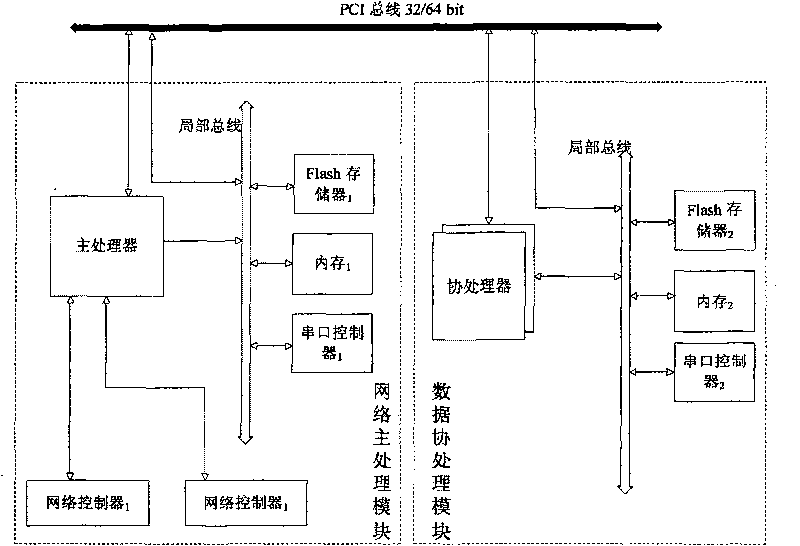
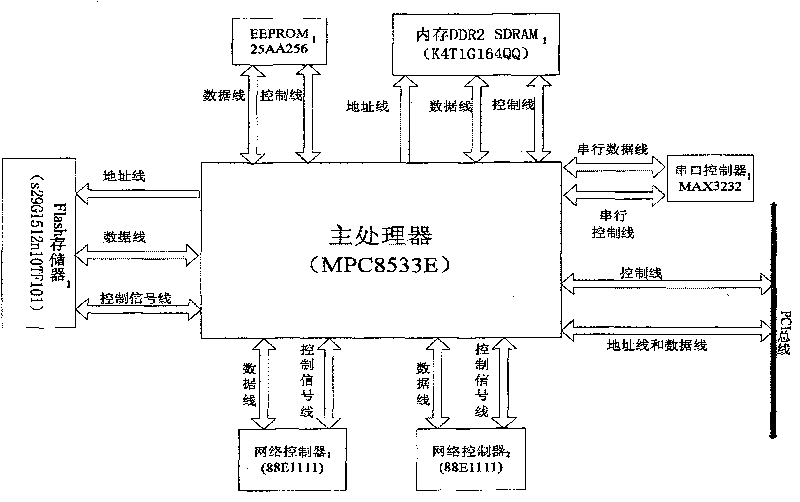
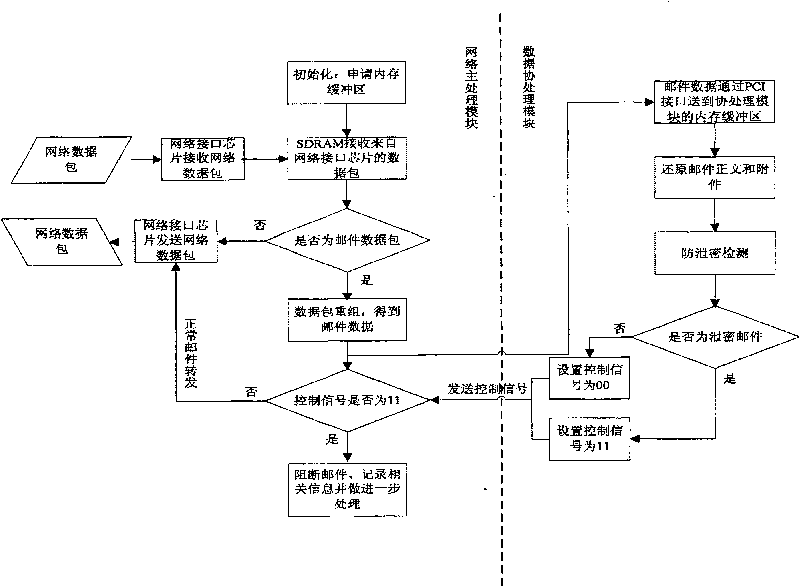
[0039] The anti-leakage email security card can be arranged in ordinary PCs or various servers supporting PCI interfaces, and can be plugged and played.
[0040] The recommended configuration is: CPU P4 2.0GHz memory 1G or more.
[0041] There are 2 configurations available for the anti-disclosure email security card:
[0042] (1) Integrated type: directly insert the card into the PCI card slot of the original gateway server, and connect the network cable of the original gateway server to the network interface of the card. In this configuration mode, the anti-leakage security card and the mail server are located in the same machine, which is very convenient for configuration and operation.
[0043] (2) Separate type: insert the anti-leakage security card into any PC, connect the PC in series to the original mail server network, and connect the network cable to the network controller of the anti-leakage security card 1 interface from the network controller at the same time 2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com