An integrity check method for remote network service
A technology for integrity verification and network services, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve the problems of poor versatility, scalability and application compatibility, difficult and infeasible modification of network application protocols, etc. Achieve the effect of preventing malicious programs from stealing or power abuse
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
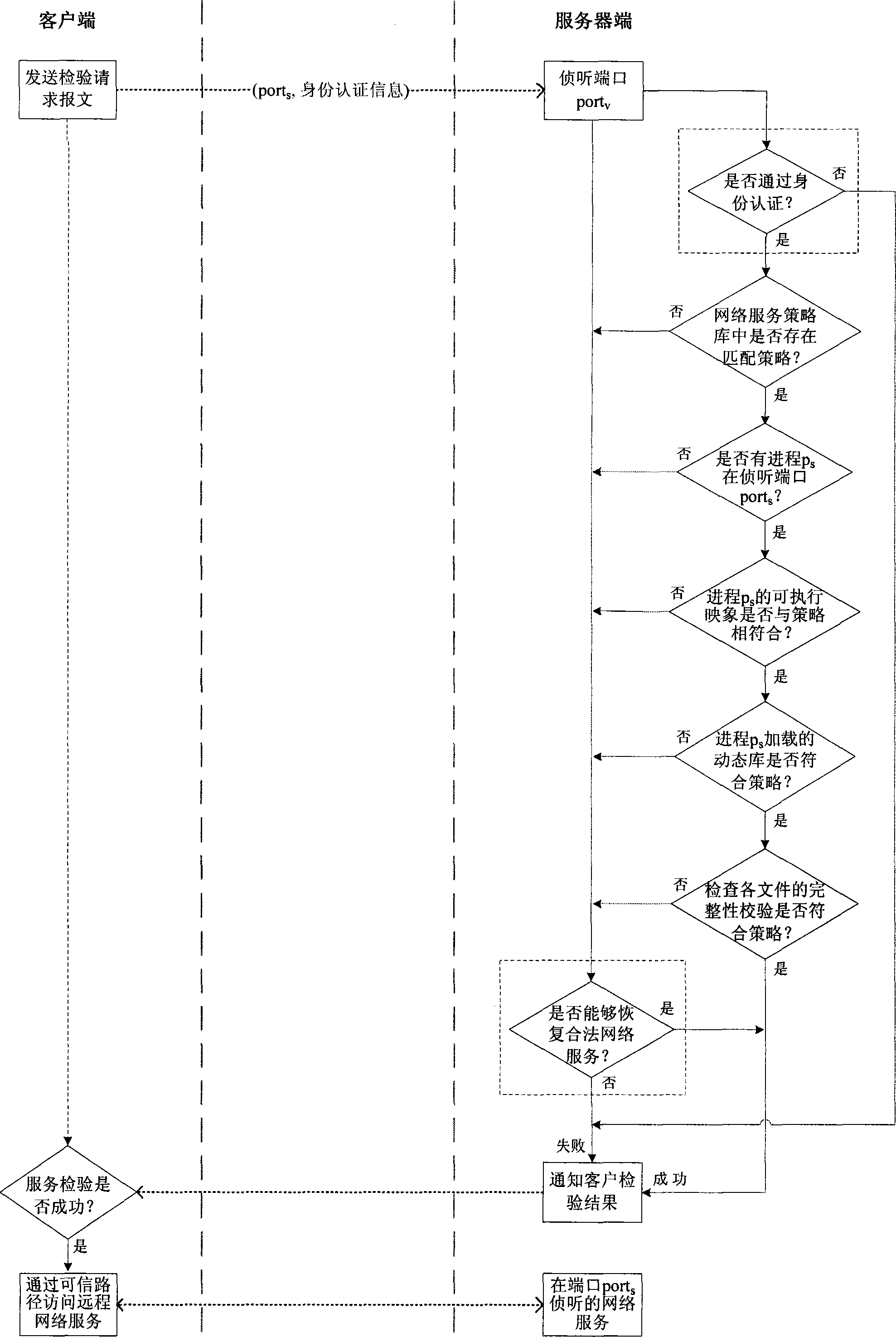
[0023] The process of a remote network service inspection is shown in the attached figure, wherein the steps in the dashed box are unnecessary steps. The entire process includes: the client sends a network service inspection request message to the remote server, and then waits for the server to reply; the server first authenticates the client's identity after receiving the inspection request, then processes the legal request to check the integrity of the specified network service, and tries to restore the service that failed the inspection , and finally reply the test result of the network service to the customer; the customer confirms whether the remote network service is currently complete and reliable by the server’s reply notification, and initiates service access if there is no problem.
[0024]The client program of the remote network service integrity inspection described in the present invention is easy to realize, and can be implemented as a common inspection client sof...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com