A WAPI authentication and secret key negotiation method and system
A key agreement and key technology, which is applied in the transmission system, user identity/authority verification, synchronous sending/receiving encryption equipment, etc. security issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
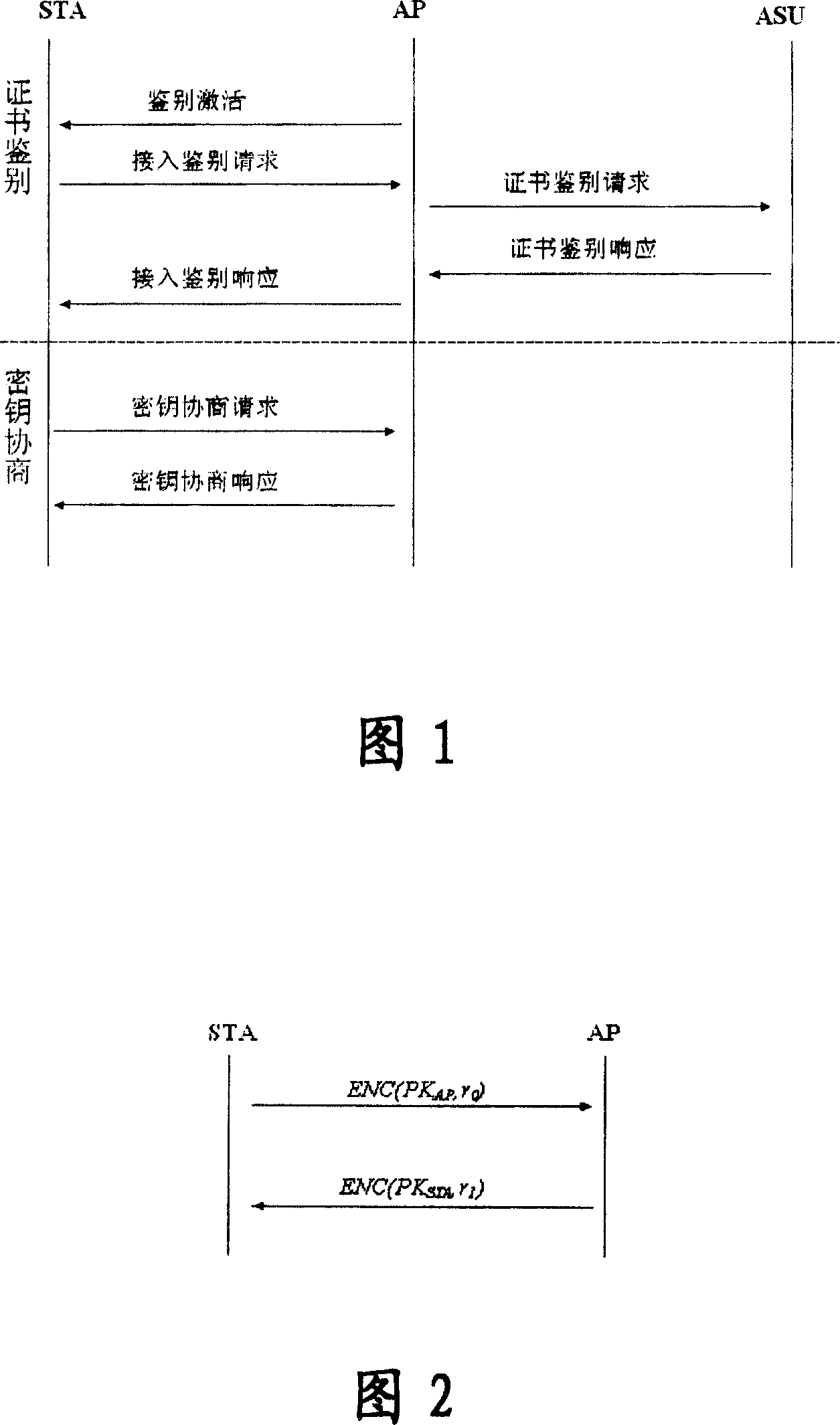
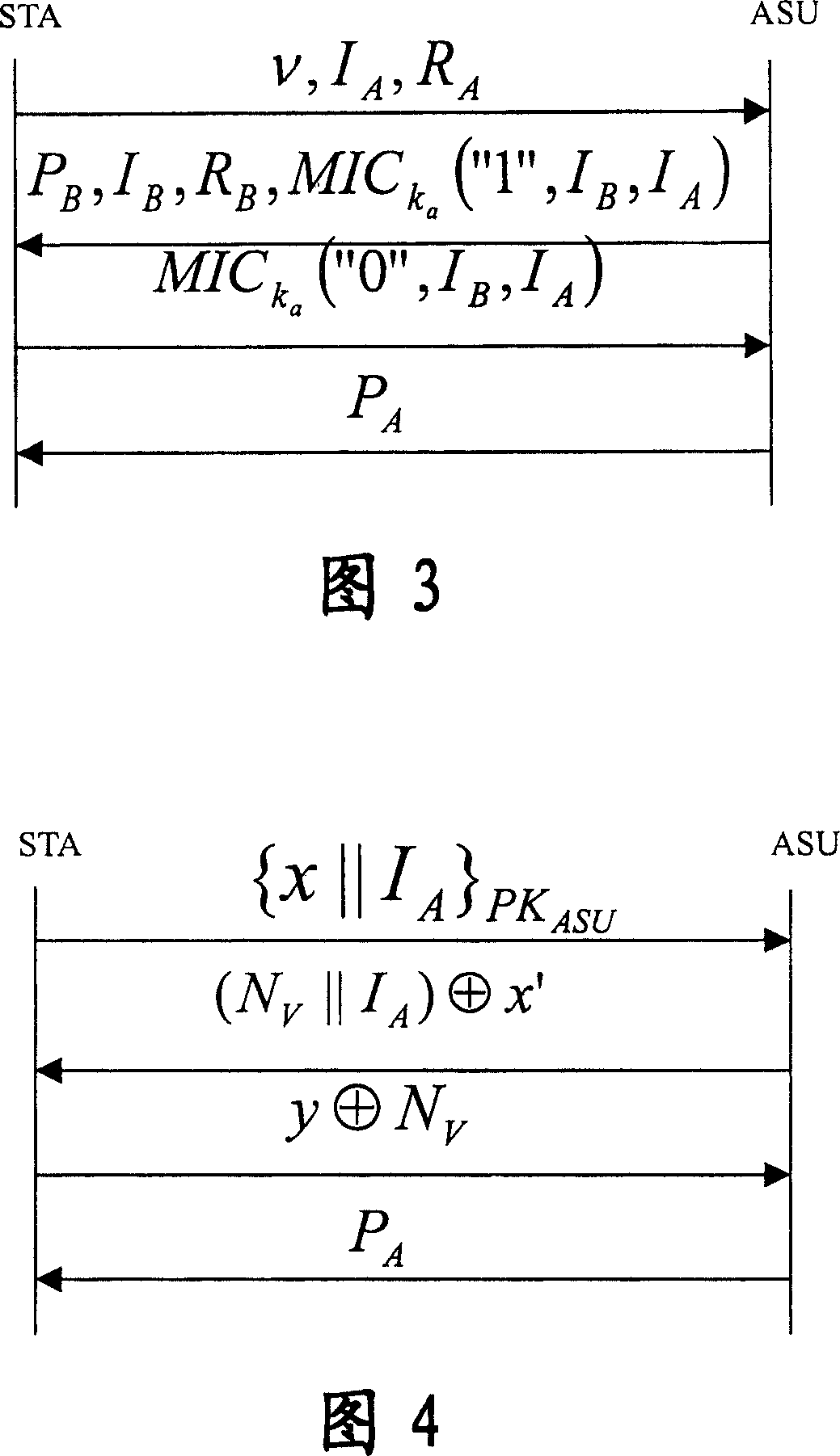
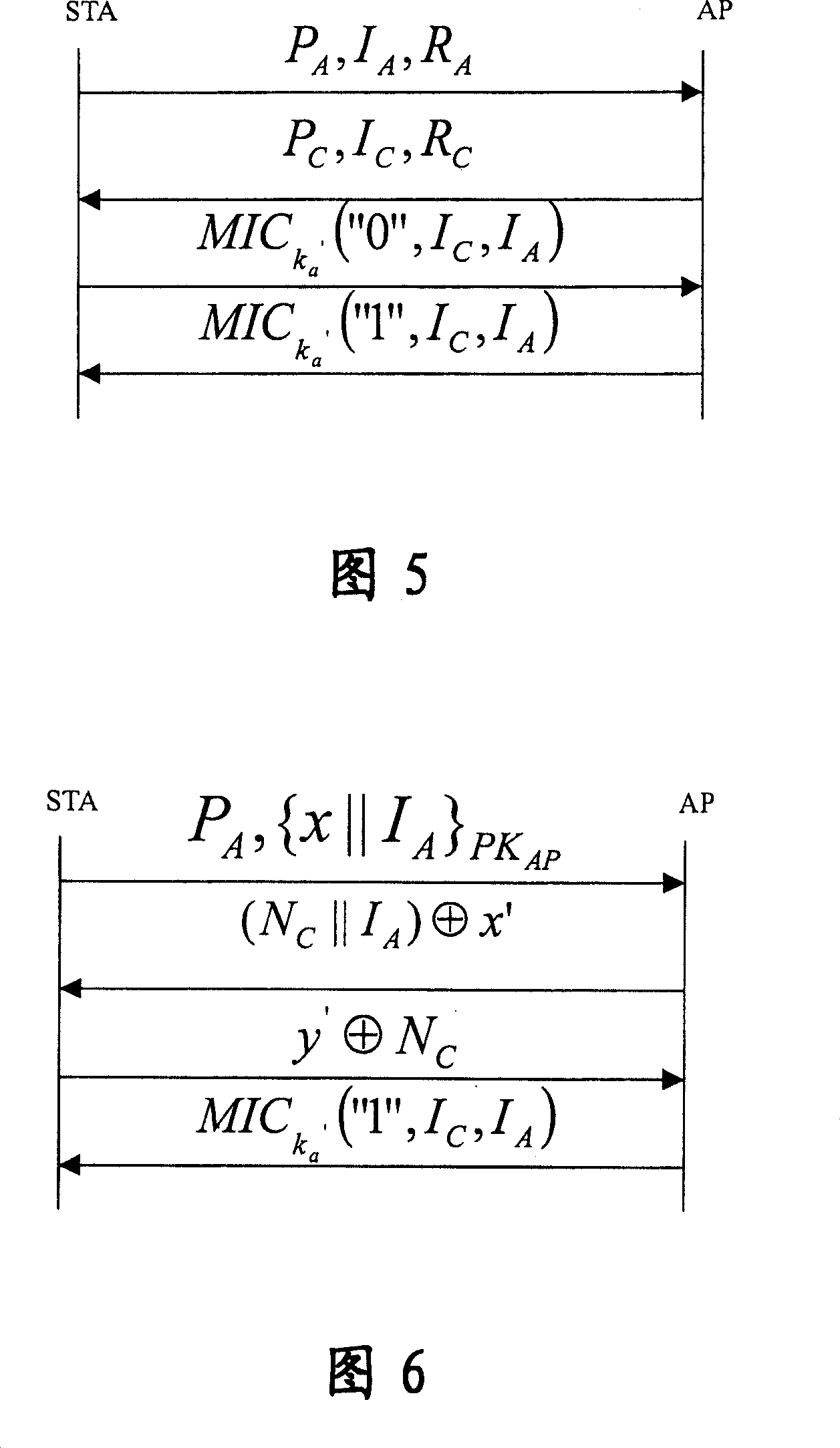
[0204] In this embodiment, both the client STA and the access point AP adopt the identity authentication and key agreement protocol of the self-verifying public key certificate.
[0205] At this time, the corresponding authentication and key agreement system in WAPI includes a client, an access point, and a certification authority; wherein, the certification authority is used to generate system key data, wherein the system key data includes system parameters and system private key; and disclose the system parameters, keep the system private key in secret; the client and access point are used to apply for a self-validating public key certificate from the certification authority, and use the system key data generated by the certification authority to establish a self-validating public key certificate , and use this self-validating public key certificate for authentication and key agreement. The authentication and key agreement method in the system will be described in detail bel...
Embodiment 2
[0269] For the identity authentication and key agreement protocol using the self-validating public key certificate only for the client STA, the access point AP has the traditional X.509 public key certificate.
[0270] At this time, the corresponding authentication and key agreement system in WAPI includes an authentication service unit, and also includes a client, a certification authority, and an access point; wherein, the certification authority is used to generate system key data, wherein the system key The data includes system parameters and system private key; and the system parameters are disclosed, and the system private key is kept secretly; the client is used to apply for a self-verifying public key certificate from the certification body, and uses the system key data generated by the certification body to establish a self-verifying public key certificate. key certificate, and use the self-validating public key certificate to perform identity verification and key nego...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com