Information safety apparatus having multiple interface and capable of being automatically installed and controlling method therefor
An information security and automatic installation technology, applied in the field of information security, can solve the problems of high cost, single interface standard and low reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0064] In this embodiment, the information security device has two USB connectors. Referring to FIG. 1, the embodiment of the present invention provides a multi-interface and automatically installable information security device, specifically including:
[0065] (1) USB connector A101, used to establish a connection with the host;
[0066] (2) USB connector B102, used to establish a connection with the host;
[0067] (3) USB interface module 103, for establishing connection with host through USB connector A101 and or USB connector B102, analyzing and processing USB communication protocol; It is connected with USB connector A101 and USB connector B102 respectively;
[0068] (4) judging module 104, which is used to judge whether the information security device is connected to the host by USB connector A101 or USB connector B102; it is connected to USB connector A101 and USB connector B102 respectively;
[0069] (5) The control module 105 is used to control and manage informatio...
Embodiment 2
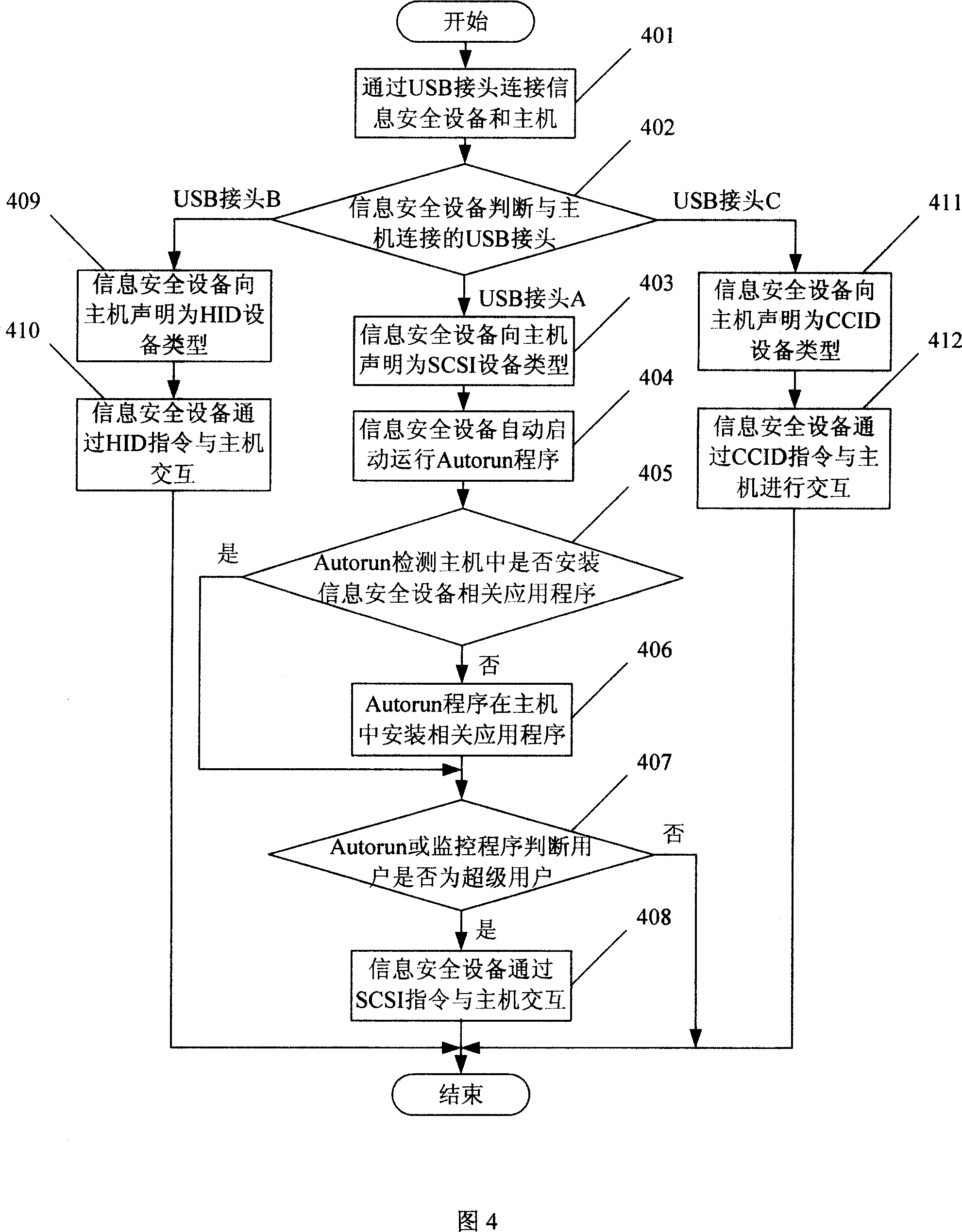
[0102] In this embodiment, the information security device has three USB connectors, USB connector A, USB connector B, and USB connector C, and the corresponding relationship between the above USB connectors and the application interface protocol is preset in the chip of the information security device as follows: When the device and the host are connected through USB connector A, the USB interface of the information security device uses the SCSI interface protocol to communicate with the host. When the information security device and the host establish a connection through USB connector B, the USB interface of the information security device uses the HID interface protocol To communicate with the host, when the information security device establishes a connection with the host through the USB connector C, the USB interface of the information security device uses the CCID interface protocol to communicate with the host.
[0103] Referring to Fig. 4, the embodiment of the presen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com