Method for controlling protocol message attack
A technology for controlling protocols and protocol messages, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as inability to perform attack control processing, inability to respond to abnormal conditions of the main control board, protocol message attacks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
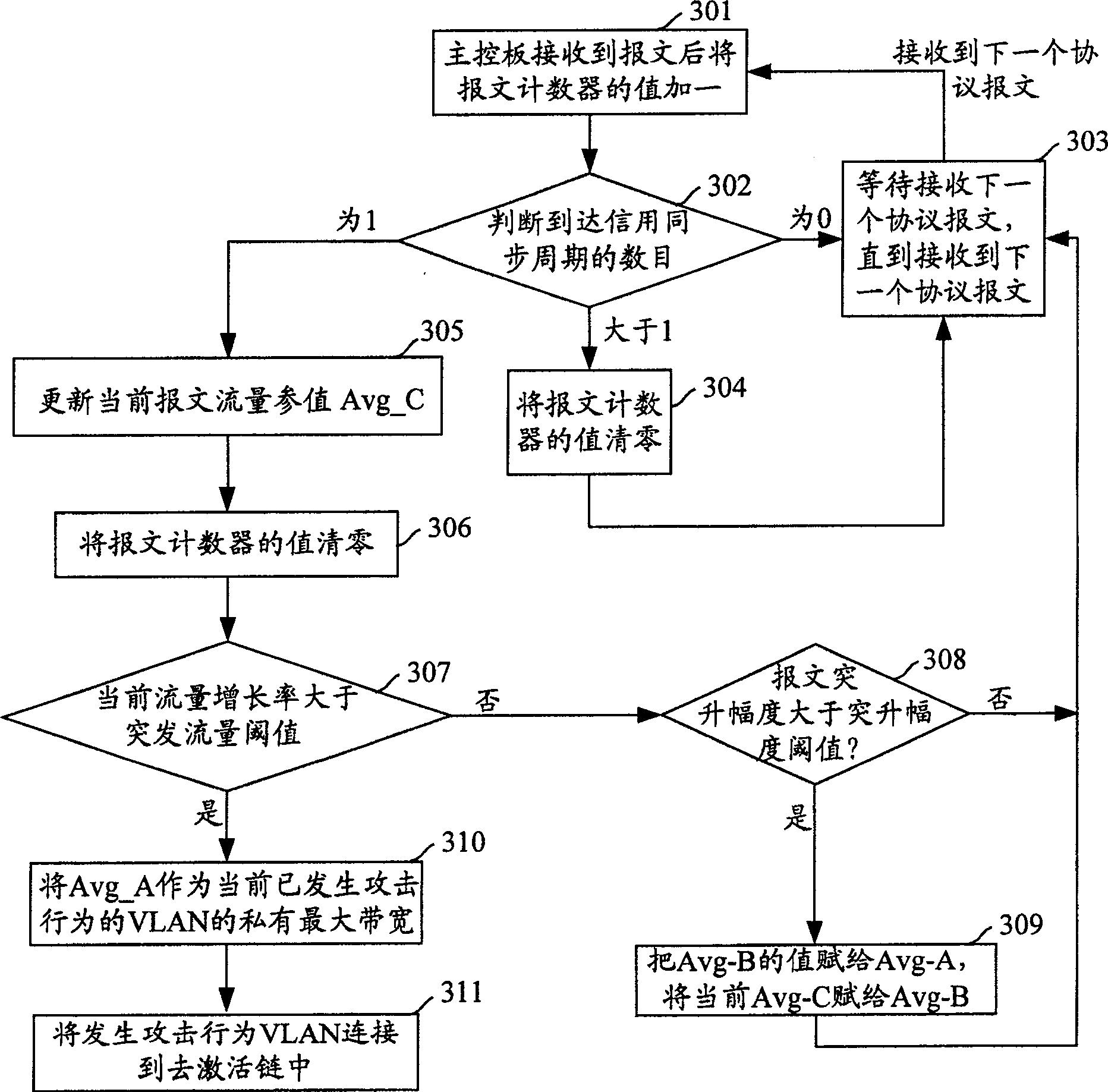
[0073] In this embodiment, the burst traffic threshold is preset, and the burst traffic threshold is a ratio, which indicates the rate of change of packet traffic that the system can bear when the packet traffic suddenly increases.
[0074] In this embodiment, it is judged whether an attack behavior occurs by comparing the current packet traffic growth rate with the burst traffic threshold.
[0075] image 3 It is a flow chart for realizing Embodiment 1 of the present invention, see image 3 In this embodiment, the specific process for realizing the control protocol message attack includes the following steps:
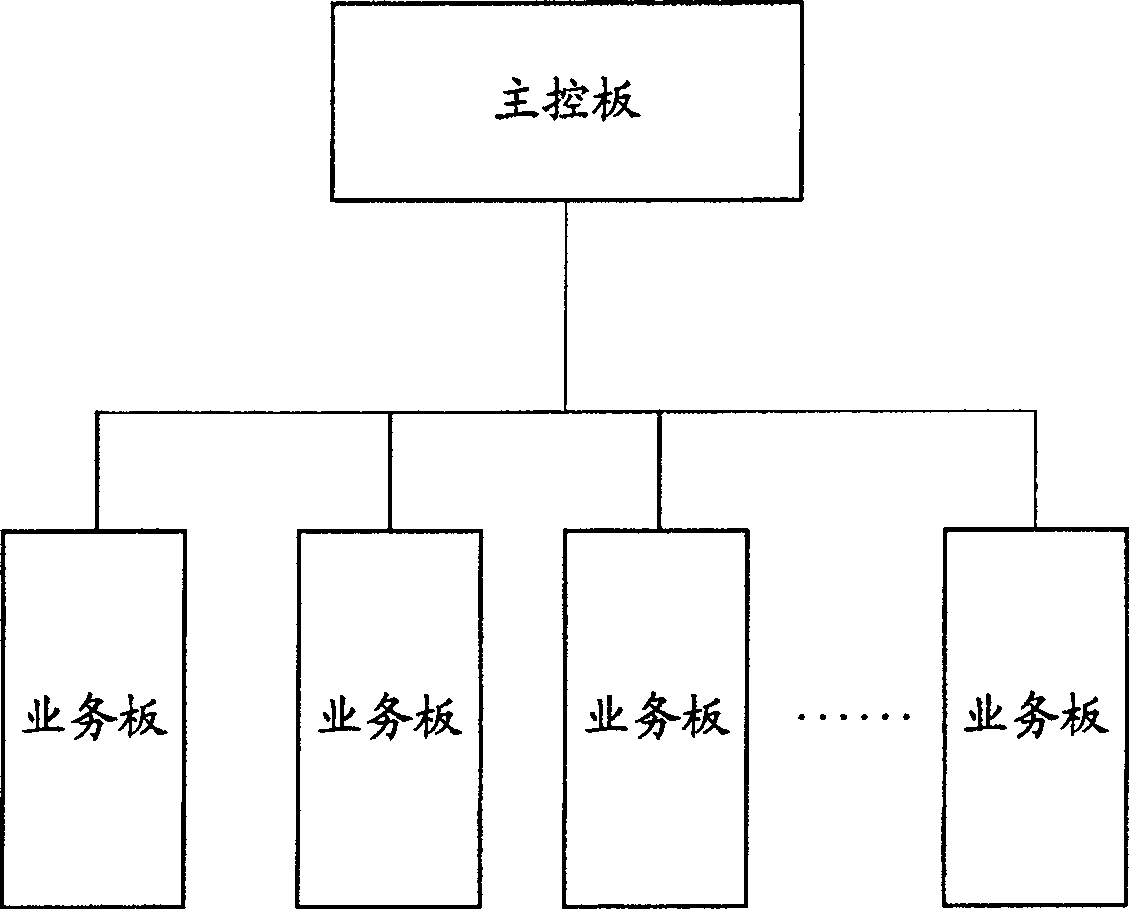
[0076] Step 301: the main control board receives a protocol message sent by a VLAN of a slot of the service board, and updates the value of the message counter, that is, the current value of the message counter Dyn_Speed=(last message counter value+1) .
[0077] Step 302: Count the number of credit synchronization cycles that arrive at the time interval between the ...
Embodiment 2
[0090] In this embodiment, the queue usage threshold is preset, and the queue usage threshold is an empirical value set according to the usage of each queue on the main control board under normal conditions when no attack occurs.
[0091] In this embodiment, it is judged whether an attack behavior occurs by comparing the queue resource usage rate with the queue usage rate threshold.
[0092] Figure 4 It is a flow chart for realizing Embodiment 2 of the present invention, see Figure 4 , the specific process of realizing the control protocol packet attack in this embodiment is as follows:
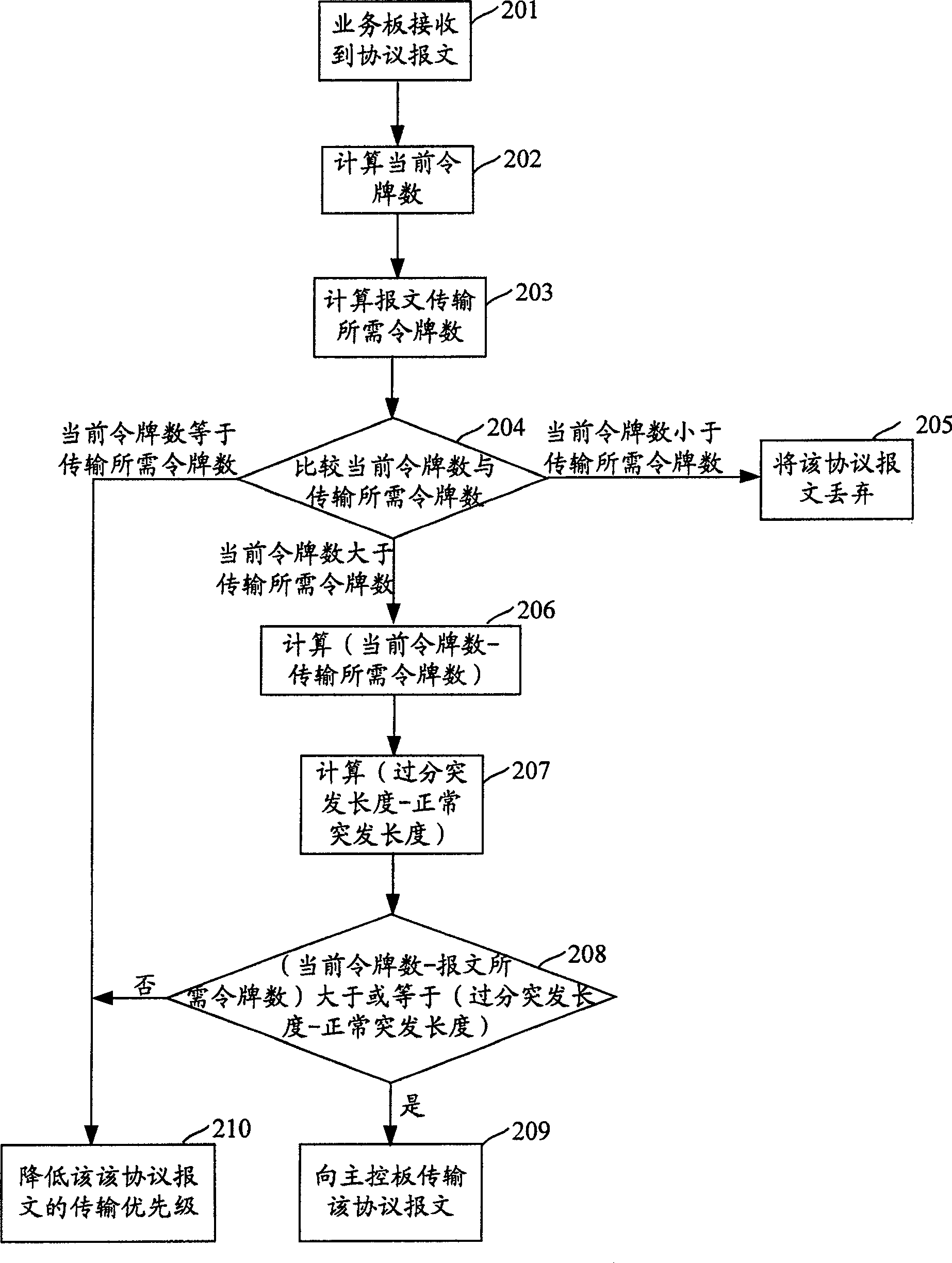
[0093] Replace step 307 of the inventive method in Embodiment 1 with step 401 of the inventive method of this embodiment, that is, calculate the queue resource utilization rate of the queue receiving the protocol message, and compare the queue resource utilization rate with the queue utilization rate threshold, if the queue resource Utilization rate is greater than the queue utilization r...
Embodiment 3
[0096] In this embodiment, the time allowed for the upper-layer application to wait for the arrival of the protocol message is set in advance as the time-sensitive response threshold.
[0097] In this embodiment, it is judged whether an attack occurs by comparing the waiting time of the upper-layer application program for the arrival of the message with the time-sensitive response threshold.
[0098] Figure 5 It is a flow chart for realizing Embodiment 3 of the present invention, see Figure 5 , the specific process of realizing the control protocol packet attack in this embodiment is as follows:
[0099] Replace step 307 of the inventive method in Embodiment 1 with step 501 of the inventive method in this embodiment, that is, judge whether the time for the upper-layer application program to receive the reachable protocol message is greater than the time-sensitive response threshold; If an attack has occurred in the VLAN corresponding to the program, then step 310 is perfor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com