Authentication and encryption method for wireless network
A technology of wireless network and security method, which is applied in the field of identification and security of wireless network to achieve the effect of ensuring security, increasing the difficulty of cracking, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail:
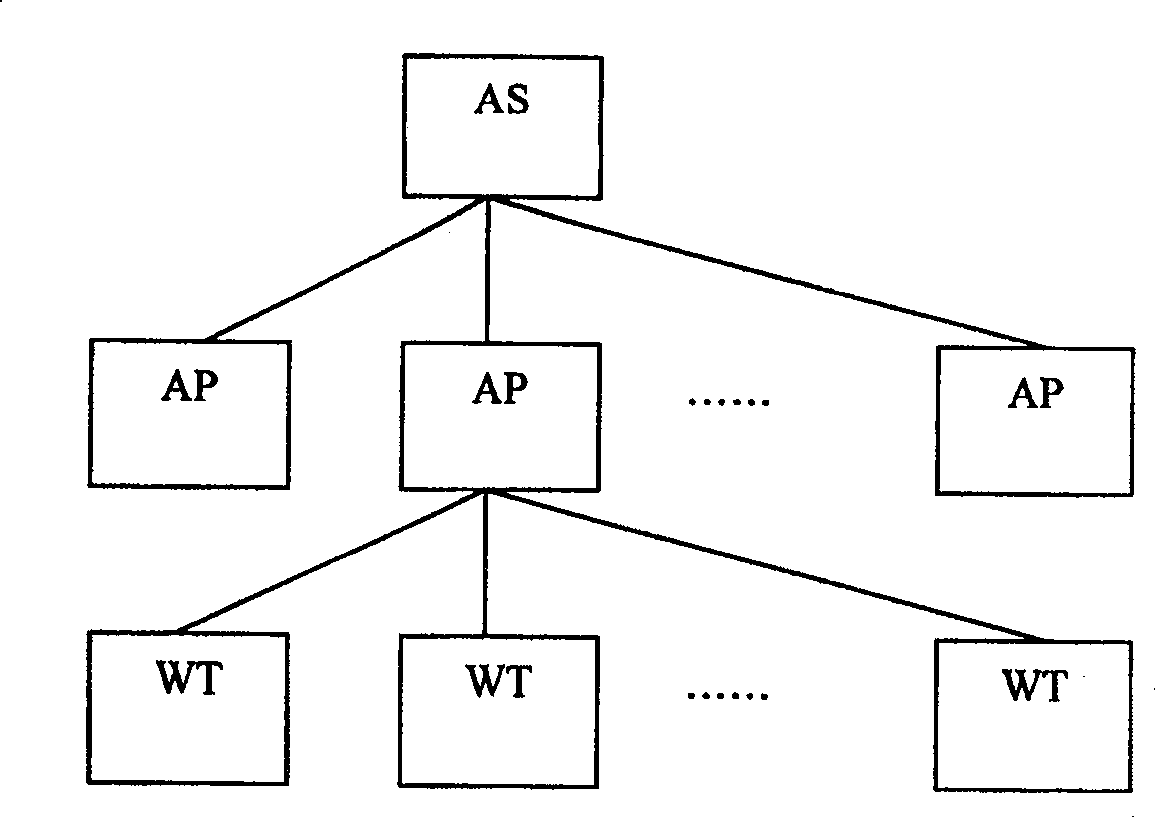
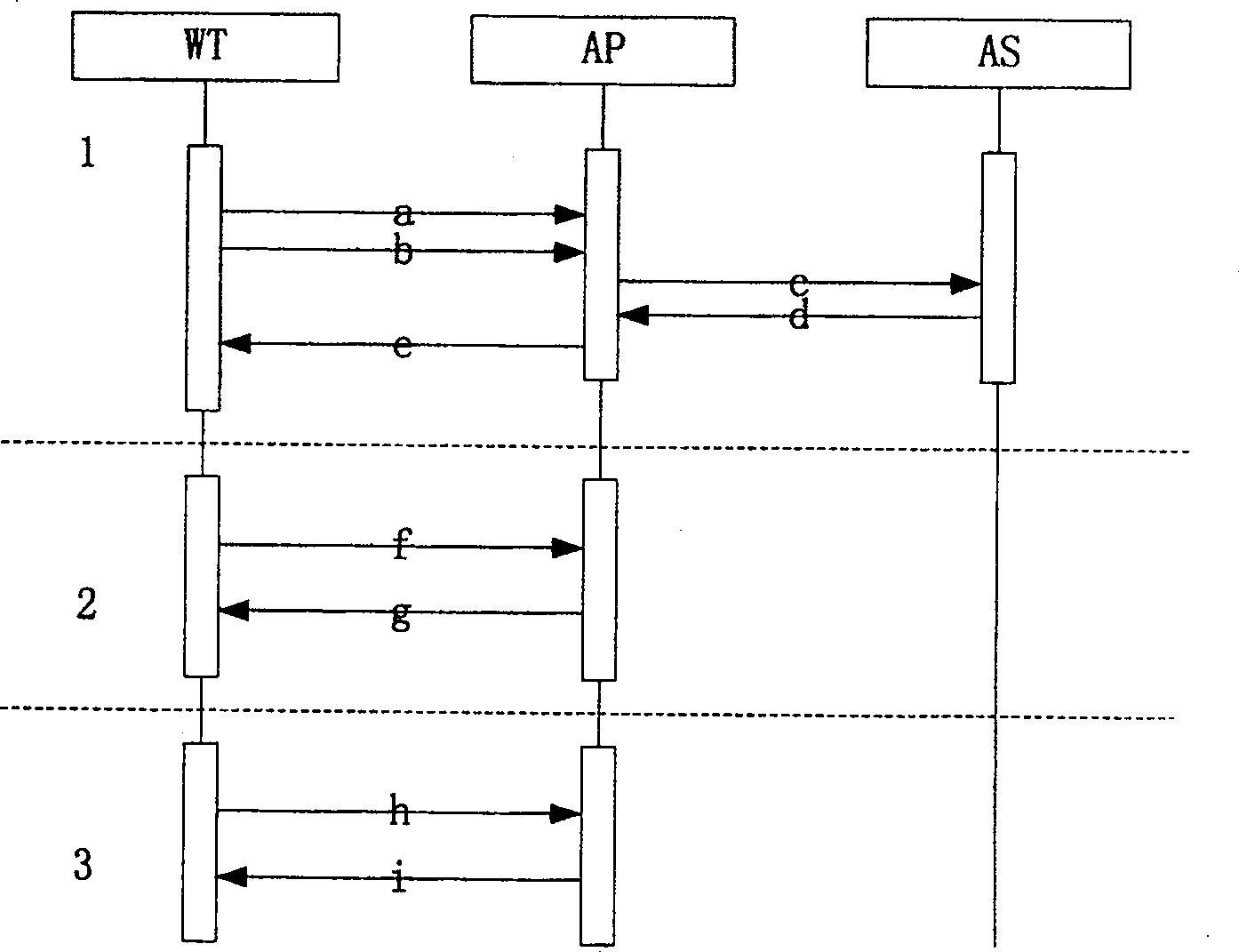
[0052] Such as figure 1 As shown, using the public key cryptography technology, when the wireless terminal WT is physically associated with the wireless access point AP, the authentication server AS is used for two-way certificate authentication, and only the wireless terminal WT with a valid certificate can access the wireless access point with a valid certificate AP, otherwise the wireless access point AP and the wireless terminal WT are physically disassociated. Among them, the content of the certificate mainly includes the serial number of the certificate, the name of the certificate issuer, the validity period of the certificate, the name of the certificate holder, the public key information of the certificate holder, the type of the certificate, the signature algorithm adopted by the certificate issuer, and the The signature of the certif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com