Entity authentication method and device
A technology for identifying entities and messages, applied in the field of network security, can solve problems such as the inability to determine who the other party is and potential safety hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
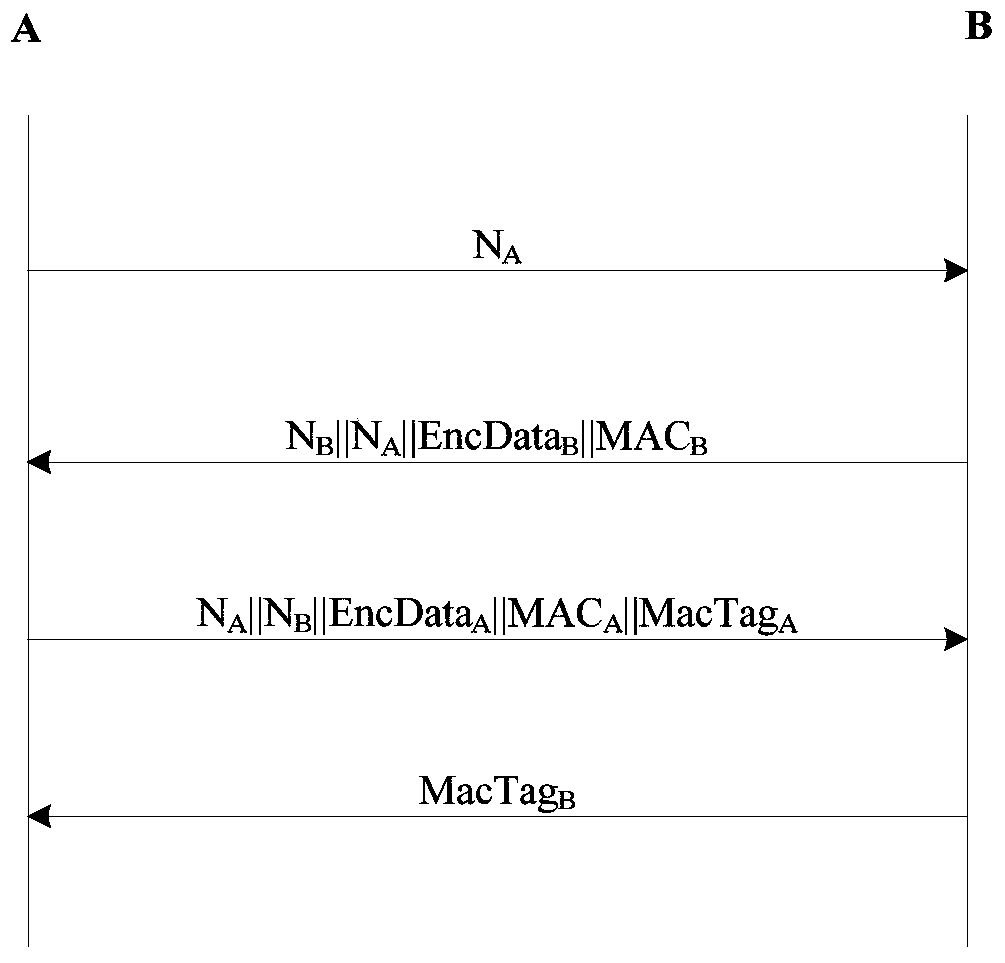
[0048] See figure 1 , the present invention provides an entity authentication method. When the method is implemented, entity A and entity B have shared a pre-shared key (Pre-Shared key, PSK) and know each other's identity, and entity A's identity as ID A , the identity of entity B is ID B , the method includes the following steps:
[0049] Step 1. Entity A generates random number N A , and send to Entity B.
[0050] Step 2. Entity B receives N A After that, generate a random number N B and the random number ZSEED used to seed the key B , calculate the key MKA||KEA||KIA=KDF1(N A ,N B ,PSK,ID A ,ID B ), calculate the ciphertext EncData B =ENC(KEA,N B ||N A ||ID B ||ID A ||ZSEED B ), calculate the message authentication code MAC B =MAC1(KIA,N B ||N A ||EncData B ), Entity B sends N B ||N A ||EncData B ||MAC B For entity A, MKA is an authentication key, KEA is a message encryption key, KIA is a message integrity key, KDF1 is a key derivation algorithm, ENC ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com